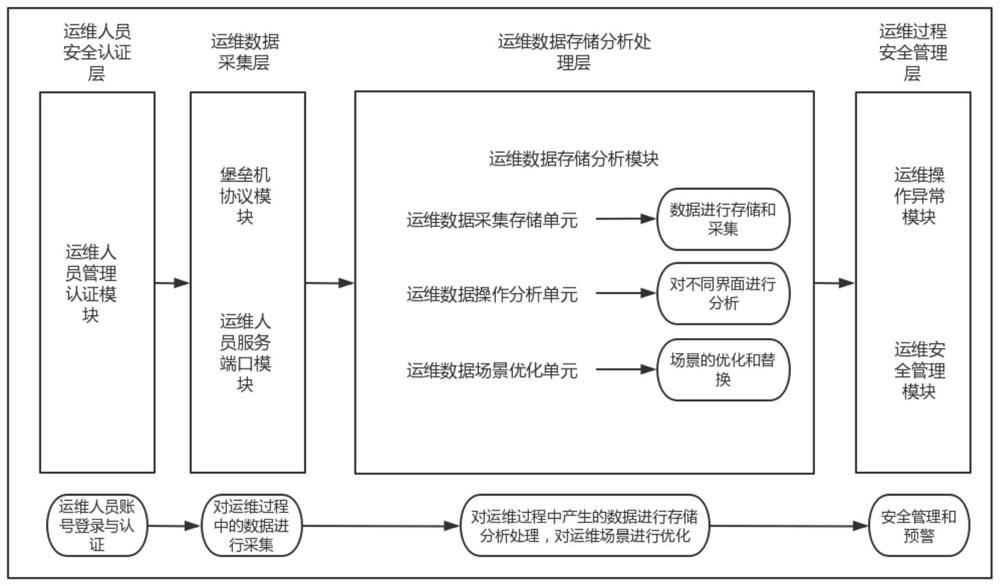
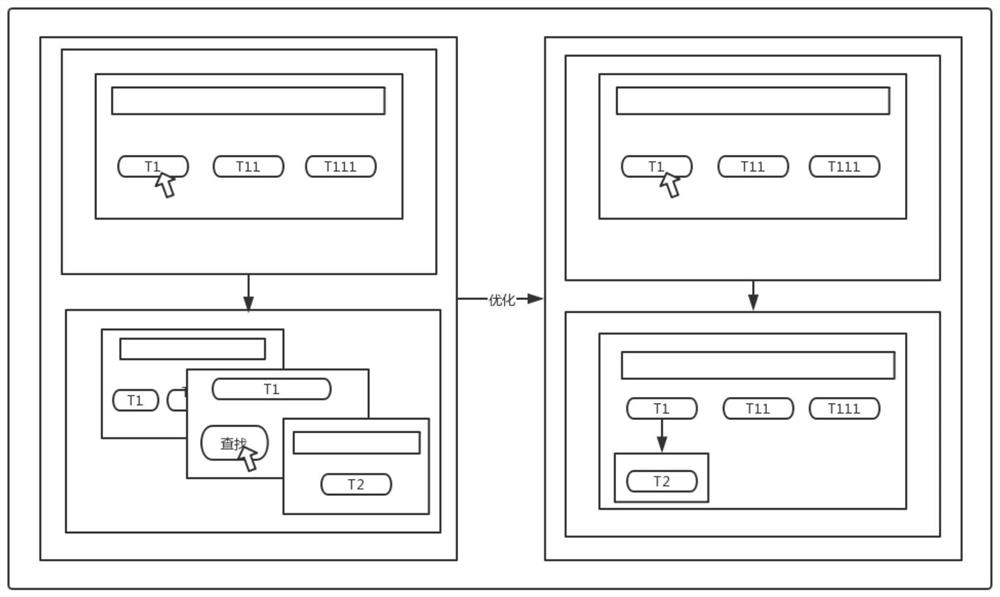
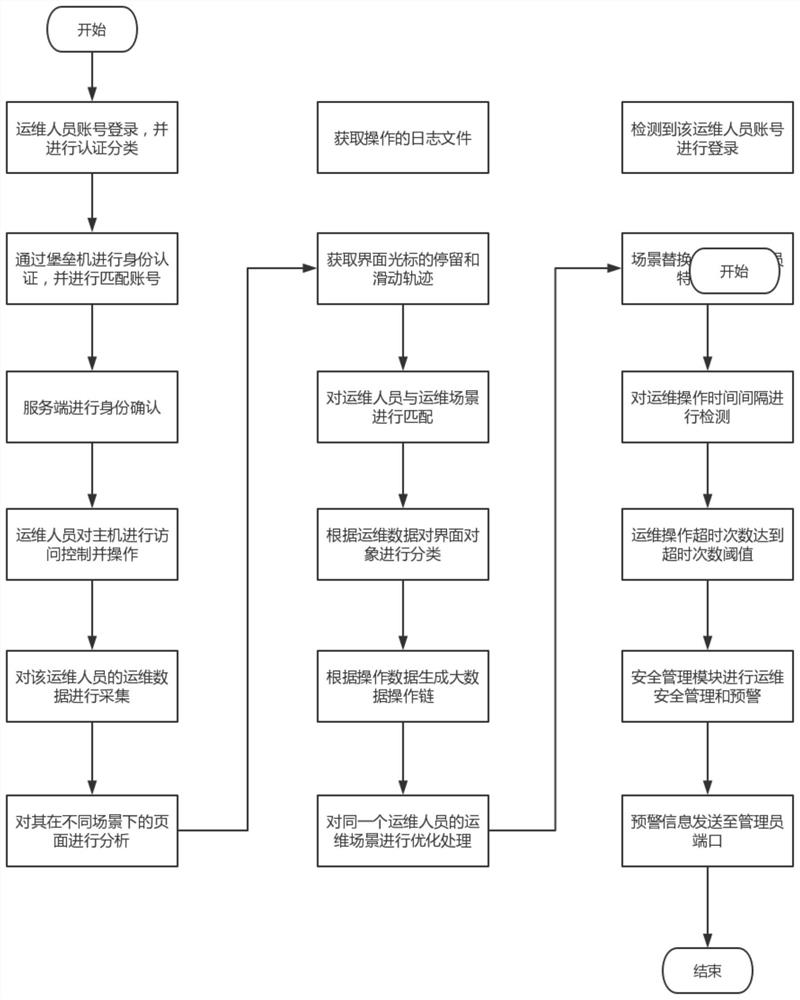
Network security operation and maintenance management system based on bastion host
An operation and maintenance management and network security technology, applied in the field of operation and maintenance management, can solve problems such as inability to judge accounts, unfavorable operation and maintenance personnel operations, affecting normal work, etc., to prevent system freezes, ensure system security, and benefit effect of operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0098] In this embodiment one:
[0099] The operation and maintenance personnel A is set up, and the login account is used for operation and maintenance operations;
[0100] The operation and maintenance data acquisition storage unit retrieves the log files of the operation and maintenance personnel A during the operation and maintenance operation, and regularly samples the position coordinates and sliding curves of the cursor clicked by the operation and maintenance personnel on the interface during the operation and maintenance process, records the position coordinates and samples Time, regularly sample all objects that exist in the operation and maintenance scene presented on the interface when the operation and maintenance personnel operate, read the object list; store the above data;
[0101] The operation and maintenance operation recording unit extracts the recorded operation and maintenance operation process data from the structured data storage file; the operation env...
Embodiment 2
[0106] In this second embodiment:
[0107] The system detects that the operation and maintenance personnel A has logged in, and the scene replacement unit replaces the scene;
[0108] The time management unit records the operation and maintenance personnel A in the operation and maintenance scene H 1 The operation and maintenance operation time under ;
[0109] It is found that its time is t 1 , t 2 , t 3 , t 4 , t 5 ;
[0110] where t 1 , t 2 , t 3 , t 4 , t 5 Both exceed the average operating time t 0 ;
[0111] Set N as the timeout threshold; N=3;
[0112] Therefore, it is considered that there is an abnormal situation in this operation, and the operation and maintenance security management module will issue an early warning and send relevant early warning information to the administrator terminal.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com