A method for intelligent offloading and security assurance of computing tasks in a 5G edge computing environment
A technology of edge computing and computing tasks, applied in the field of communication, can solve problems such as heavy load of base stations, private data infringement, and inability to obtain calculation results, so as to achieve effective use and avoid leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be described in detail below with reference to the accompanying drawings and specific embodiments.
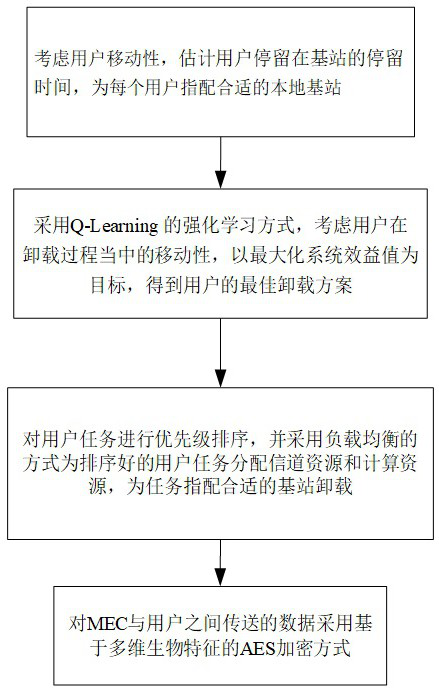
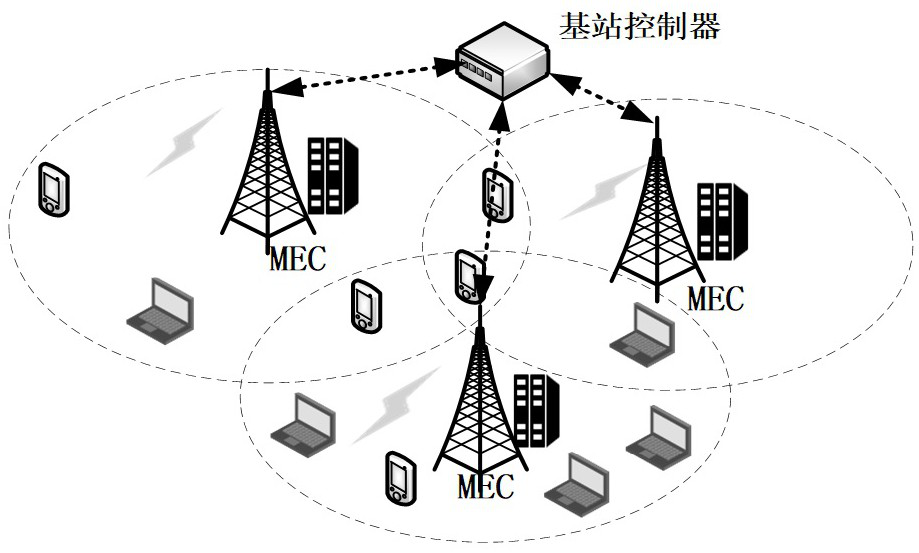
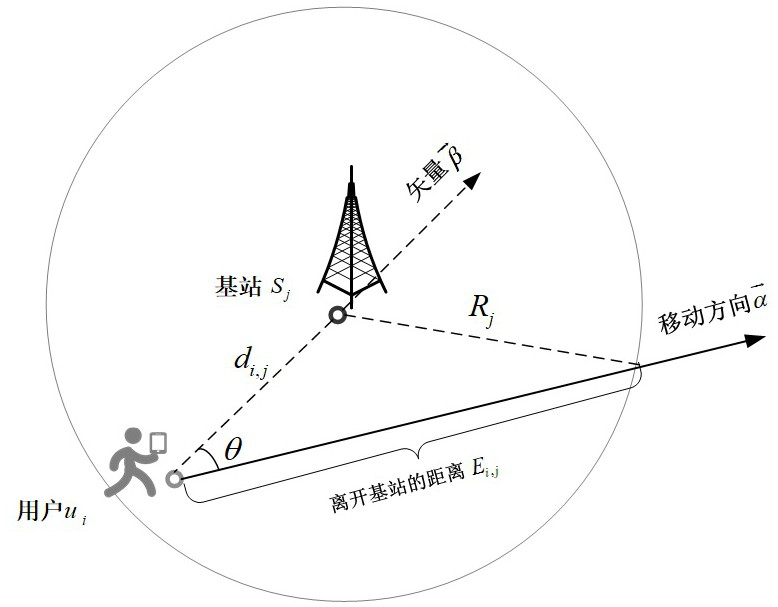
[0055] like figure 1 As shown, a method for intelligent offloading of computing tasks and optimization of security assurance in a 5G edge computing environment is applied to the network scenario of multi-user and multi-MEC servers. It also considers the time delay and energy consumed, as well as the fees paid by the user to the MEC server. Q-Learning is adopted to maximize the system benefit to obtain the user's offloading solution. In addition, the load balance between the base stations is also considered. Tasks are prioritized to more effectively utilize the computing resources of the MEC server and the channel resources of the base station. Finally, considering the security of user tasks during offloading, AES encryption based on multi-dime...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com