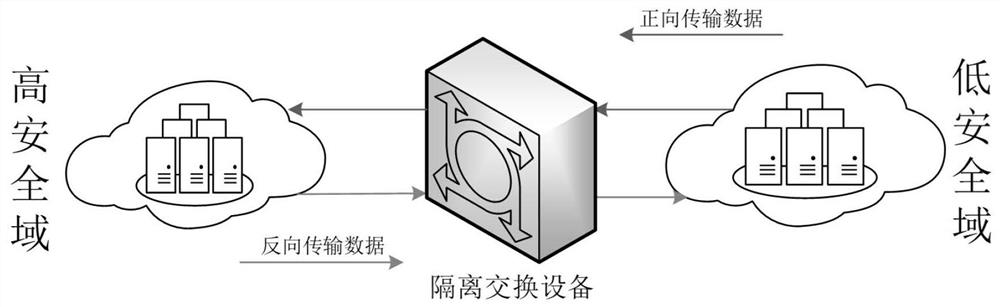
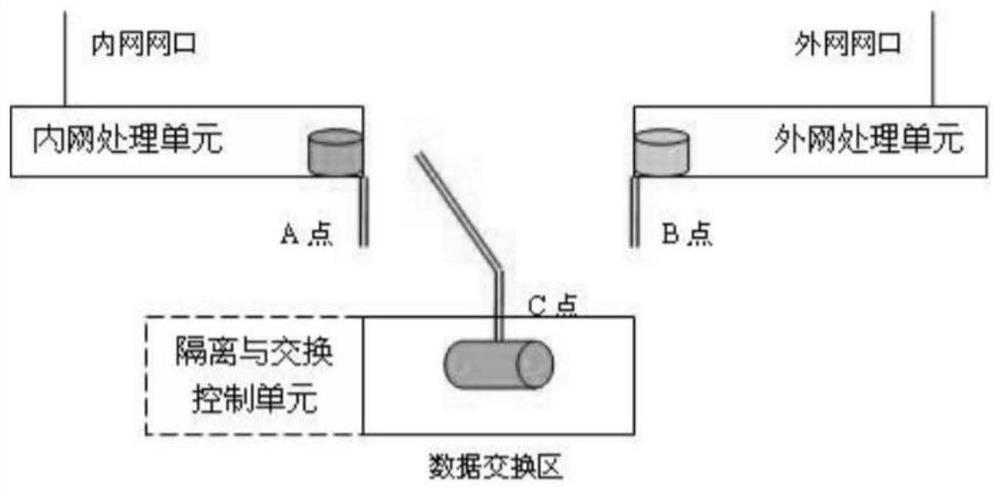
Data cross-security domain reverse transmission method
A reverse transmission, cross-security domain technology, applied in digital data protection, electrical digital data processing, computer security devices, etc., can solve problems affecting data exchange efficiency, resource consumption and cost, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
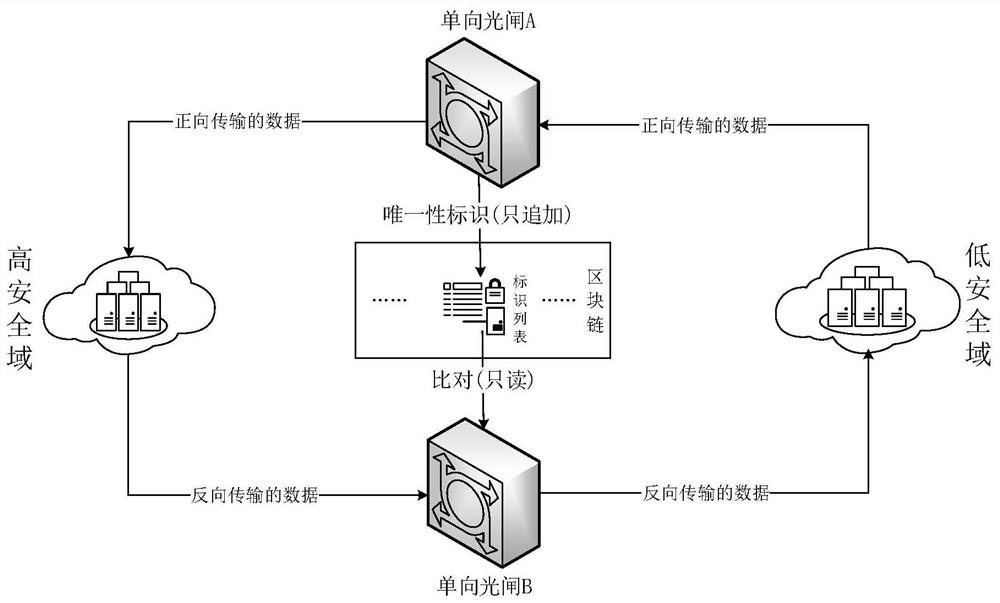
[0036] This embodiment provides a method for reverse transmission of data across security domains, such as image 3 As shown, the specific process is:
[0037] The one-way shutter A performs identity calculation on the data packets transmitted in the forward direction, and the process of obtaining the unique identification is as follows:
[0038] 1) The one-way shutter A obtains the original data unit in the forward transmission data packet, that is, the original video data, and conducts a security review on it;
[0039] 2) After completing the security review of the original video data, the one-way shutter A uses the SHA3-224 function to perform a hash operation on the data to obtain the hash value X; as shown in Table 1.
[0040] Table 1 Cross-domain data information
[0041]
[0042] 3) The one-way shutter A stores X in the identification list (it should be noted that the one-way shutter A only has the right to append to the identification list), and synchronizes it to...
Embodiment 2
[0054] This embodiment provides a method for reverse transmission of data across security domains, such as image 3 As shown, the specific process is:
[0055] The one-way shutter A performs identity calculation on the data packets transmitted in the forward direction, and the process of obtaining the unique identification is as follows:
[0056] 1) The one-way shutter A obtains the original data unit in the forward transmission data packet, that is, the original txt text data, and performs a security review on it;
[0057] 2) After completing the security review of the original txt text data, the one-way shutter A uses the SHA3-224 function to perform a hash operation on the data to obtain the hash value X; as shown in Table 3;
[0058] table 3
[0059]
[0060] 3) The one-way shutter A stores X in the identification list (it should be noted that the one-way shutter A only has the right to append to the identification list), and synchronizes it to each node of the blockc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com