Image processing method and system, storage medium and computing equipment
An image processing and image technology, applied in image data processing, image data processing, computing, etc., can solve the problem that image processing methods cannot cope with attacks such as rotation, scaling, translation, mirroring, cutting, collage, and compression
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] Common attacks on images in real life include rotation, scaling, translation, mirroring, cutting, collage, compression, etc. Related digital image watermarking schemes are often difficult to resist the combined attacks of the above attacks, resulting in digital image watermarking failure and digital image security. The security is low, and there are still problems such as image copyright ownership, anti-counterfeiting and anti-tampering.
[0036] In order to solve the above problems, the embodiment of the present application provides an image processing method. Using the characteristics of Fourier transform, a watermark template method based on discrete Fourier transform is proposed, which has strong robustness and can deal with rotation, Attacks such as scaling, translation, mirroring, cutting, collage, compression, etc., and can give the image's rotation scaling factor, is a watermarking method for image correction. Moreover, this method is a watermark template scheme...
Embodiment 2
[0187] According to an embodiment of the present application, an image processing method is also provided. Figure 11 It is a flowchart of an image processing method according to Embodiment 2 of the present application. Such as Figure 11 As shown, the method includes the following steps:
[0188] Step S112, acquiring a detection image and a binary sequence, wherein the binary sequence is used to generate a watermark contained in the detection image.
[0189] Specifically, the detection image in the above step may be an image that needs to be detected whether it contains a watermark, it may be the above target image, or it may be other images. Since the watermark embedded in the original image adopts a circular shape, the target magnitude image may be a polar coordinate magnitude image.
[0190] It should be noted that the construction of the binary sequence satisfies at least one of the following conditions: the traversal result obtained from traversing from the head of th...
Embodiment 3
[0213] According to an embodiment of the present application, an image processing device for implementing the above image processing method is also provided, such as Figure 12 As shown, the apparatus 1200 includes: an acquisition module 1202 and a modification module 1204 .
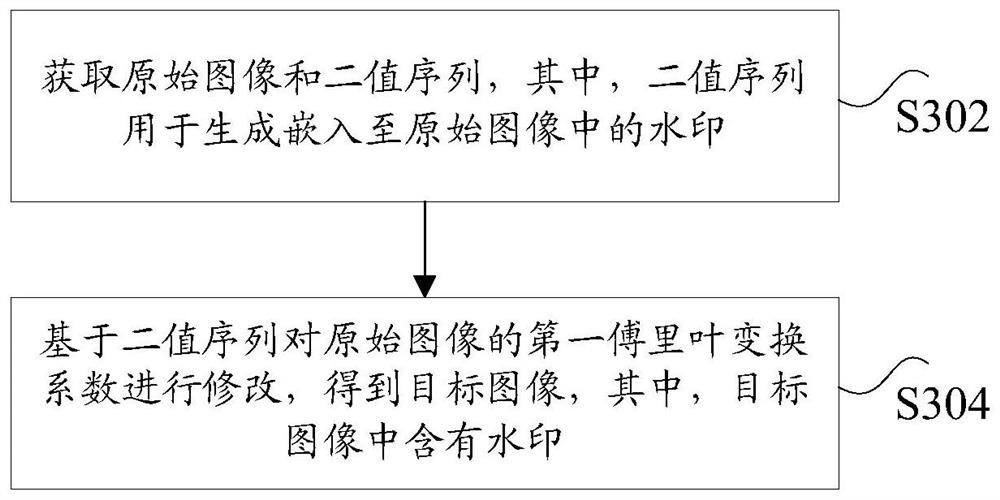
[0214] Wherein, the obtaining module 1202 is used to obtain the original image and a binary sequence, wherein the binary sequence is used to generate a watermark embedded in the original image; the modification module 1204 is used to perform the first Fourier transform of the original image based on the binary sequence The coefficients are modified to obtain the target image, wherein the target image contains a watermark.
[0215] It should be noted here that the above acquisition module 1202 and modification module 1204 correspond to steps S302 to S304 in Embodiment 1, and the examples and application scenarios realized by the two modules are the same as those of the corresponding steps, but they are no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com