Security protection providing system and method for database
A security protection and database technology, applied in digital data protection, digital data authentication, electronic digital data processing, etc., can solve the problems that computers accessing the database cannot be controlled, blocked, and illegal computer connections cannot be prevented.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
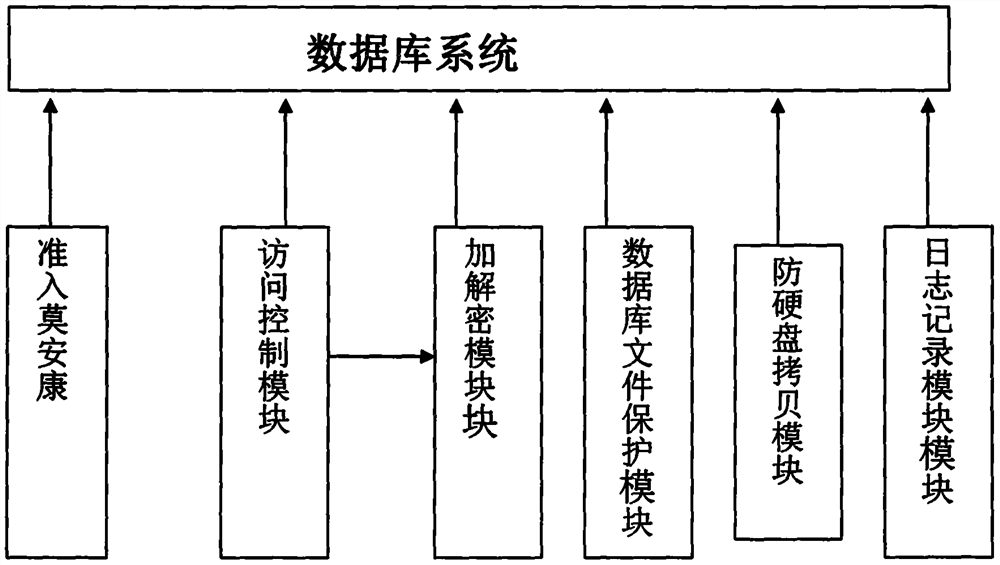
[0031] The server program is installed on the database service, and the client is installed on the application side.
[0032] In addition, a very important point to realize the system of the present invention is the setting of security policy:
[0033] The security policy includes the following items:
[0034] 1) Security level setting
[0035] In order to meet the different security needs of various customers, there are three levels of security: nuclear secret, confidential, and secret.
[0036] 2) Encryption algorithm setting
[0037] Different encryption algorithms can be set through the application, such as DES, 3DES, AES, RC4, etc.
[0038] 3) Key setting
[0039] Different keys can be set through the application program, and keys of any length can be set.
[0040] 4) Risk query operation setting
[0041] Define the query object, including: table name, field name.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com