Detection method and system for counterfeit mobile application and related product
A mobile application and detection method technology, which is applied in the field of mobile information security, can solve the problems of automatic identification and detection of counterfeit mobile applications, and achieve the effect of reducing manual intervention and ensuring accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
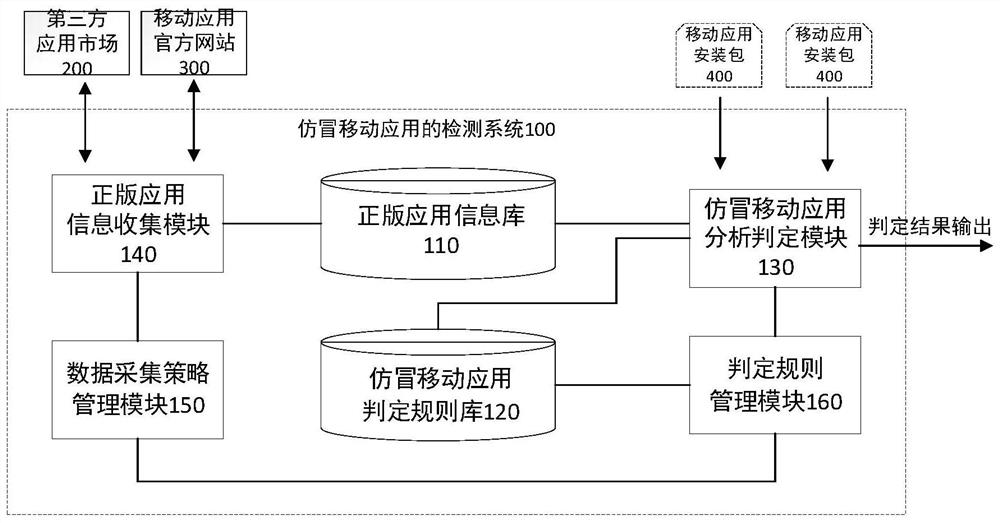
Image
Examples
Embodiment 1
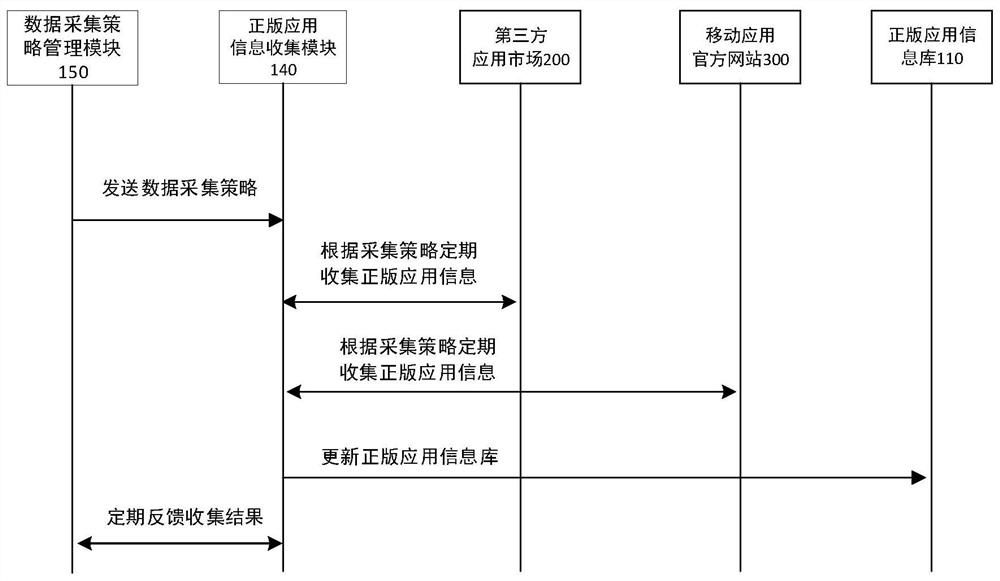
[0145]In this example, the automatic collection and updating of licensed information in the licensed application information database is realized.
[0146] Step 1: Through the data collection policy management module in this system, define the crawlers that collect APP data and which application dimension information needs to be extracted.
[0147] Step 2: The genuine application information collection module regularly collects application information in the third-party application market and major official websites according to the collection strategy, including application name, package name, publisher, installation package, etc., and regularly feedbacks the collection results to the administrator .
[0148] Step 3: The genuine application information collection module regularly and repeatedly crawls third-party application markets and major official websites according to manual settings, and checks the version number. If the version number is updated, re-download and update...
Embodiment 2
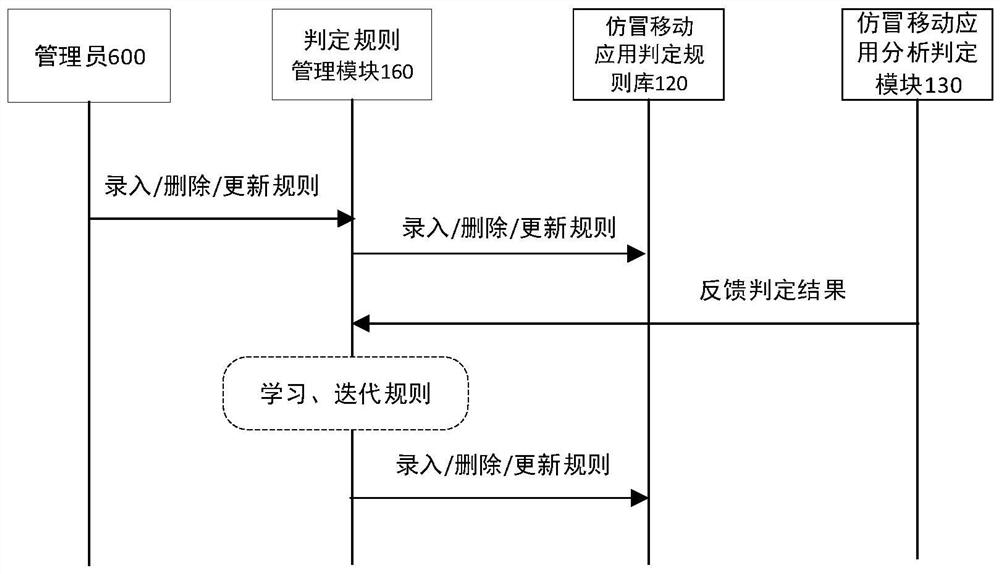
[0150] In this example, the counterfeit detection and judgment of the mobile application package is realized.
[0151] Step 1: The user uploads the mobile application installation package A, and the installation package enters the counterfeit mobile application analysis and determination module
[0152] Step 2: For the uploaded installation package A, perform static analysis and dynamic analysis, read the data in the genuine application information database, and use the counterfeit application determination rule base to determine. If the APP satisfies at least one of the first type of satisfaction conditions and the second type of satisfaction conditions, it will enter the filter of the third type of satisfaction conditions.
example 1
[0153] Example 1: The user uploaded the APP "DiDi Finance", and "DiDi Finance" exists in the genuine APP library, but the historical version number is different from that of the uploaded APP, and the uploaded APP logo has a low resolution, which is suspected to be a screenshot, so a high counterfeit score is output. It is judged as a counterfeit APP.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com