Video monitoring quantum encryption system
A quantum encryption system, video surveillance technology, applied in the direction of analog security/charging system, transmission system, digital transmission system, etc., can solve the problem of limited transmission range of Ethernet, reduce irrelevant interference factors, ensure integrity and fluency , the effect of ensuring the transmission speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
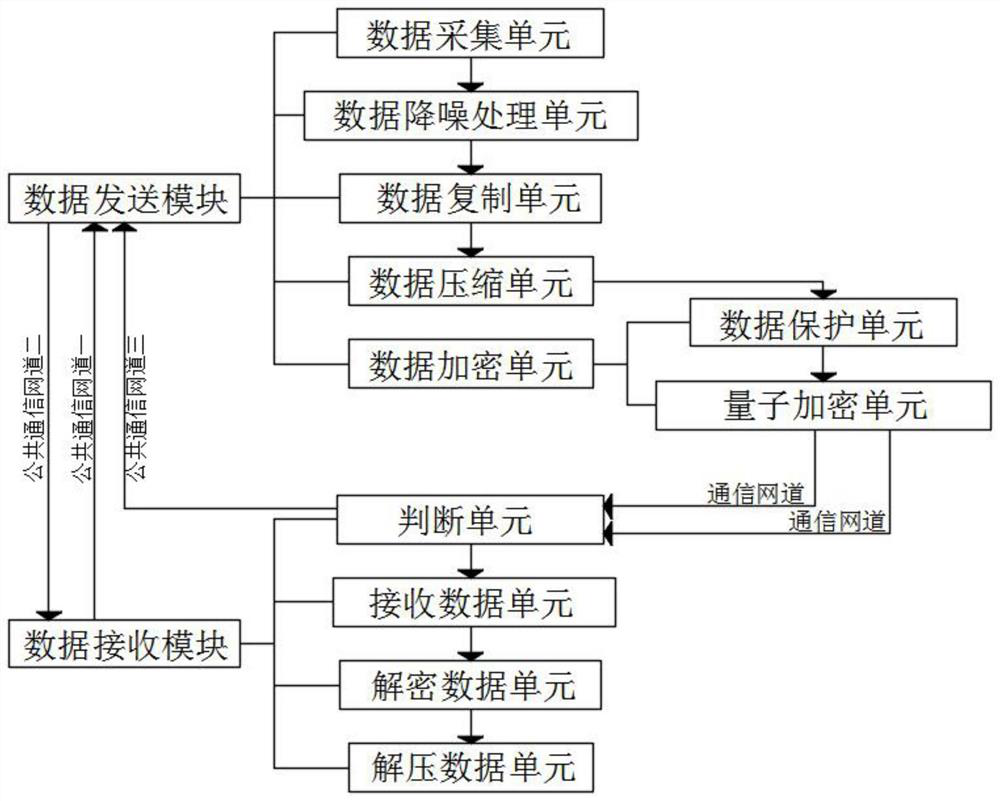
[0040] The data collection unit can collect and store the video data that needs to be transmitted, and the data copying unit can make multiple copies of the video data in the data collection unit that needs to be encrypted and transmitted.
[0041] Specifically, the video data to be transmitted is stored by the data acquisition unit, which can provide transmission source support for subsequent secondary and multiple transmissions. By duplicating the video data, cracking of the video data can be avoided. Moreover, after the data is cracked and reorganized, the fluency between data fragments is affected, thereby ensuring the integrity and fluency of the decrypted data, and providing conditions for reducing data distortion.
Embodiment 2
[0043] The data noise reduction processing unit uses a filter to process the video data, and the data compression unit can compress the video data processed by the data copying unit one by one.
[0044] In addition, the setting of the data noise reduction processing unit can perform corresponding preprocessing on the data before transmission. The filter can reduce the undue noise of the audio in the video, so as to obtain clear video data, which can reduce the memory size during the subsequent encrypted transmission. After compression processing, the memory size of data transmission is further reduced, so as to ensure the transmission speed of encrypted data.
Embodiment 3
[0046] There are two communication network channels connected between the quantum encryption unit and the judgment unit. When the quantum encryption unit performs encryption processing, the time of encrypting data, the quantity of encryption, and the data after encryption processing can be processed by the quantum encryption unit. Detect the encryption time and encrypted quantity transmitted by the quantum encryption unit as the basis, and check with the received encrypted processed data. If there is a discrepancy between the quantity or the encrypted time, it can be judged that there is a third party in the transmitted data. For interception or stealing, this information needs to be transmitted to the data receiving module through the public communication network channel 3 for secondary encrypted transmission. If both the quantity and the encrypted time are consistent, it means that there is no third-party interception in this encrypted transmission Or the phenomenon of steali...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com