Authorization management method and system, server and client
An authorization management and server technology, applied in the field of authorization security management, can solve problems such as difficulty in obtaining credible time, and achieve the effects of improving effectiveness, preventing tampering, and enhancing effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
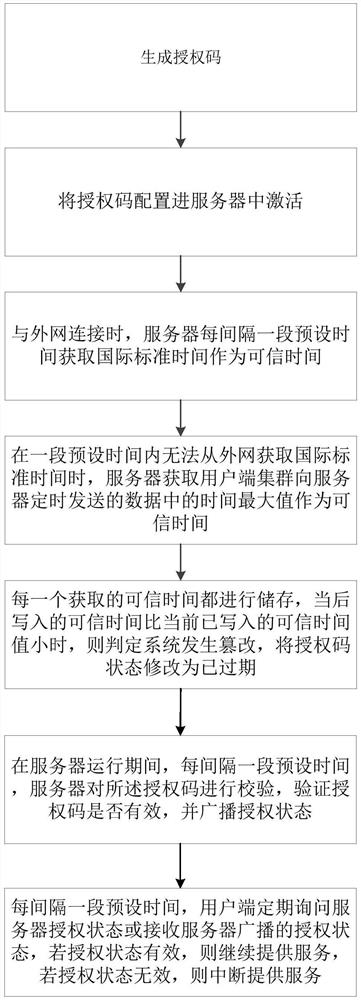
[0046] as attached figure 1 Shown is a flow chart of an authorization management method provided in this embodiment, and the method specifically includes the following steps:
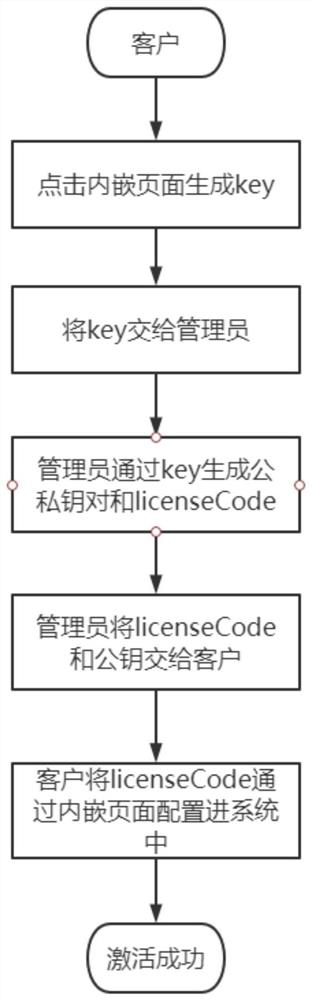
[0047] Step 1: Generate an authorization code. Specifically, the authorization code generation steps are as attached figure 2 As shown, the client clicks on the embedded page through the server to generate a key, where the key is the machine information string of the server, and the machine information string is encrypted. The customer gives the machine information string to the administrator of the service provider, and the administrator configures the expiration time, operating parameters and machine information according to the machine information string to generate an authorization code. The administrator then asymmetrically encrypts the authorization code to obtain a public-private key pair, and hands over the public key and authorization code to the client, and keeps the private key for himself...
Embodiment 2
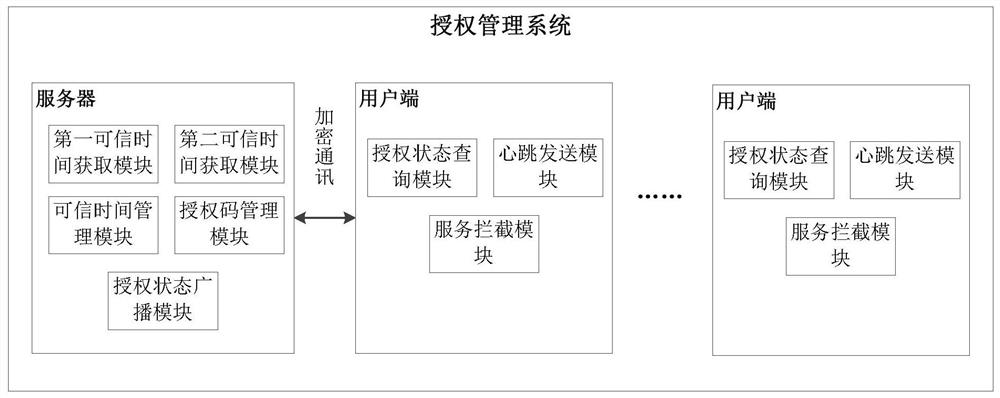
[0057] as attached image 3 As shown, it is a structural block diagram of an authorization management system provided by this embodiment, and the system specifically includes a server and several client terminals that communicate encryptedly with the server.
[0058] Among them, the server is used to configure and verify the authorization code, obtain the trusted time from the external network or the client cluster, judge whether the time has been tampered with, and broadcast the verification result of the authorization code. Specifically, the server includes a first credible time acquisition module, which is used to obtain the international standard time when the client is connected to the external network; a second credible time acquisition module, which is used to collect Time value; credible time management module, used to store credible time and judge whether the time has been tampered with; authorization code management module, used to configure and verify the authorizat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com