A verification method and system for formalization of security protocols
A security protocol and verification method technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of model detection state explosion, error-prone, heavy workload, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0072] Such as figure 1 As shown, a verification method for the formalization of security protocols includes the following steps:
[0073] The security protocol description to be verified is obtained from the security protocol specification;
[0074] Analyzing the security protocol specification to obtain a protocol configuration object;
[0075] Constructing a protocol model according to the protocol configuration object;
[0076] Constructing an attacker model based on the protocol model, and optimizing the attacker model;
[0077] describing the security properties of the security protocol according to linear temporal logic;
[0078] A communication environment is constructed based on the optimized attacker model, in which the model detector SPIN is used to verify whether the protocol model satisfies the security attribute, and if not, the model detector SPIN outputs an attack path.
[0079] In the above-mentioned embodiments, the protocol model is constructed for the s...
Embodiment 2
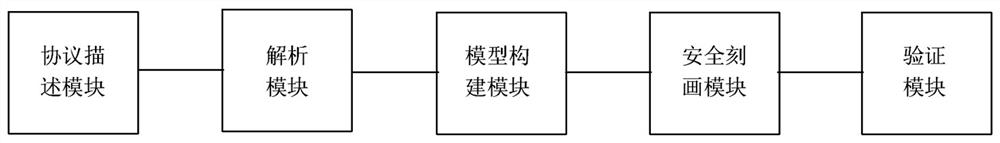
[0182] Such as figure 2 As shown, a verification system for the formalization of security protocols is characterized in that it includes:
[0183] The protocol description module is used to obtain the security protocol specification according to the security protocol description to be verified according to the formal security protocol description language;
[0184] A parsing module, configured to parse the security protocol specification to obtain a protocol configuration object;
[0185] A model building module, configured to build a protocol model according to the protocol configuration object;
[0186] It is also used to construct an attacker model based on the protocol model, and optimize the attacker model;
[0187] A security characterization module, configured to describe the security attributes of the security protocol according to linear temporal logic;
[0188] A verification module, configured to construct a communication environment based on the optimized attac...
Embodiment 3
[0190] A verification system for the formalization of security protocols, comprising a memory, a processor, and a computer program stored in the memory and operable on the processor, when the processor executes the computer program, the Verification methods for the formalization of security protocols as described above.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com