Network attack detection system and method based on two-stage learning model
A network attack and learning model technology, which is applied in the two-stage detection system field of network attack data preprocessing and network attack data identification, can solve the problems of long model training time, increase the difficulty of network attack detection model and system deployment, and reduce the volume effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
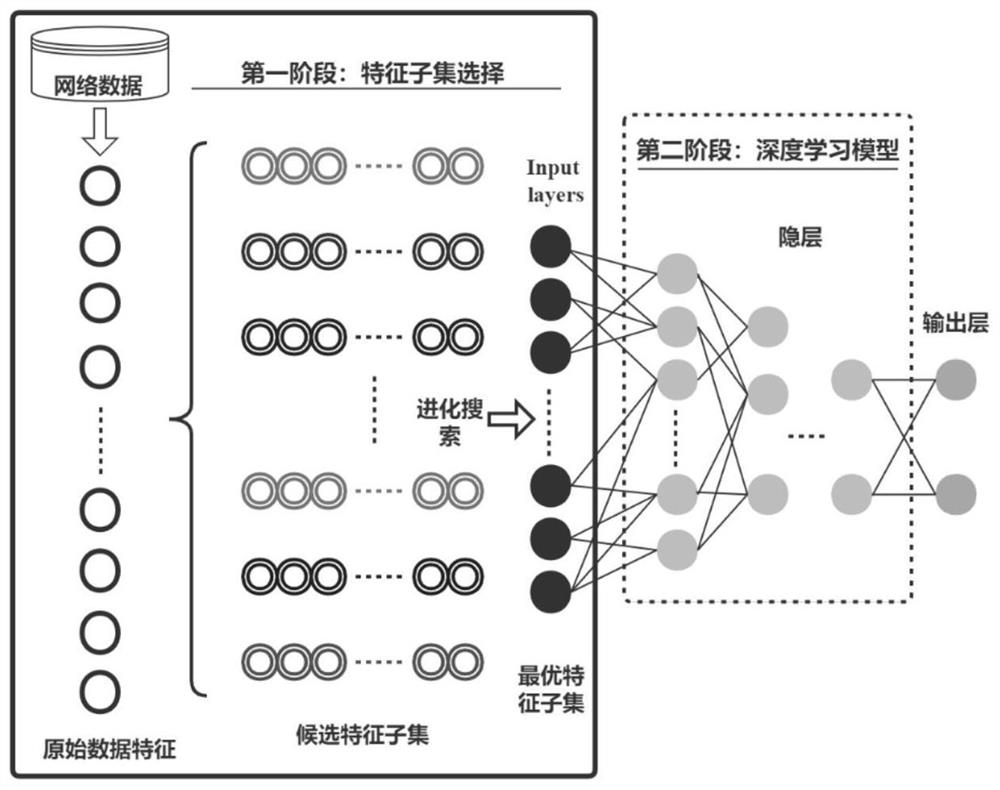
[0041] Such as figure 1 As shown, the network attack detection method based on the two-stage learning model in this embodiment is carried out in the following steps:
[0042] Stage 1: Reduction of the feature dimension of the network dataset; in this stage, the feature subset of the network dataset is used as an inseparable unit for feature combination evaluation, and the feature dimension reduction of the network dataset is realized; the details are as follows:
[0043] Step 1.1, preprocessing of massive network data. Firstly, the data instances that exceed the limit of the missing feature threshold are screened out; then, the features with low information content are deleted in the network data set after the initial screening, such as serial number, timestamp, etc.; finally, the non-numeric data in the network data set The features are one-hot encoded and mapped to binary vectors;
[0044] Step 1.2, construct a feature subset evaluation function for the network dataset. B...
Embodiment 2
[0053] Such as Figure 4 As shown, the network attack detection system based on the two-stage learning model in this embodiment includes the following modules:
[0054] The feature dimension reduction module of the network dataset: this module evaluates the feature combination of the feature subset of the network dataset as an inseparable unit, and realizes the feature dimension reduction of the network dataset; specifically, it includes the following sub-modules:
[0055] Preprocessing module of massive network data: preprocessing of massive network data. Firstly, the data instances that exceed the limit of the missing feature threshold are screened out; then, the features with low information content are deleted in the network data set after the initial screening, such as serial number, timestamp, etc.; finally, the non-numeric data in the network data set The features are one-hot encoded and mapped to binary vectors;
[0056] Feature Subset Evaluation Function Building Bl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com