Network slice cutover alarm shielding method and device
A network slicing and slicing technology, which is applied in the field of electronic information, can solve problems such as inability to adapt to needs, complex slicing structure, and intricate relationships, and achieve the effect of improving accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
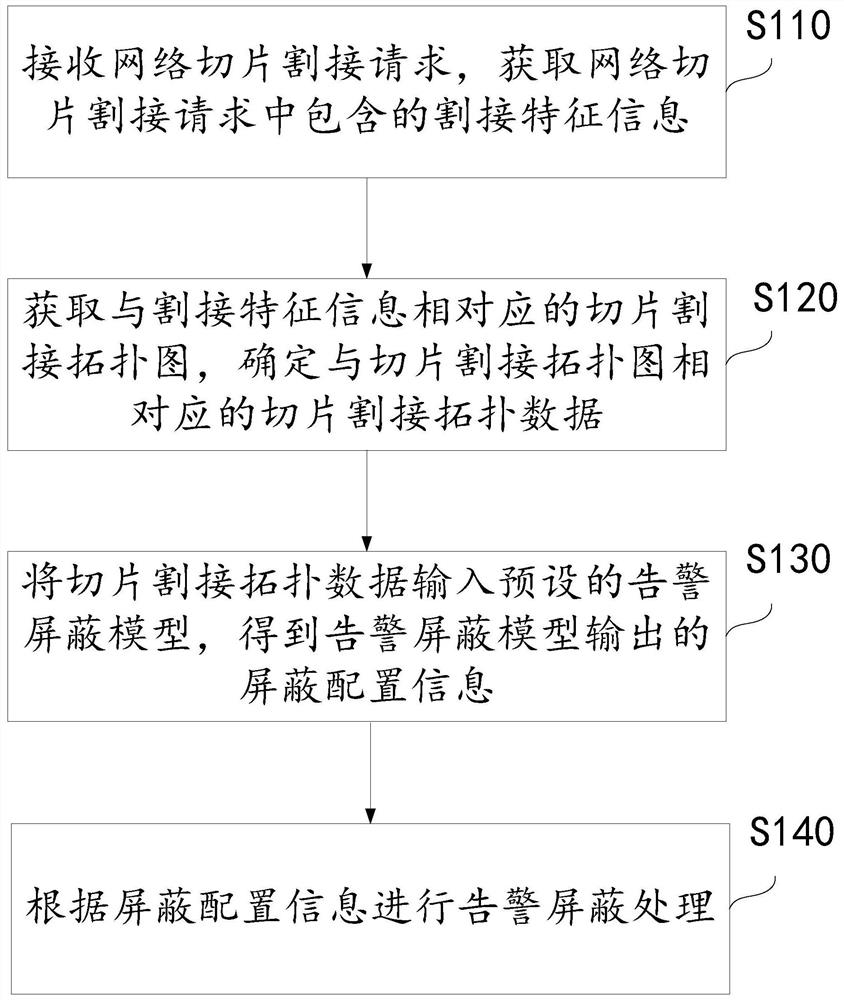
[0053] figure 1 A flow chart of a cutover alarm shielding method for network slicing provided by Embodiment 1 of the present invention is shown. Such as figure 1 As shown, the method includes:
[0054] Step S110: Receive a network slice cutover request, and obtain cutover feature information contained in the network slice cutover request.
[0055] Among them, the cutover feature information contained in the network slice cutover request is used to describe the objects and processing methods of the network slice cutover processing. Therefore, any cutover processing objects and cutover processing that can be used to describe the network slice The information of the mode can be used as the cutover feature information.
[0056] For example, in a specific example, the cutover feature information contained in the network slice cutover request includes at least one of the following: network elements involved in cutover, network element components involved in cutover, cutover duratio...
Embodiment 3
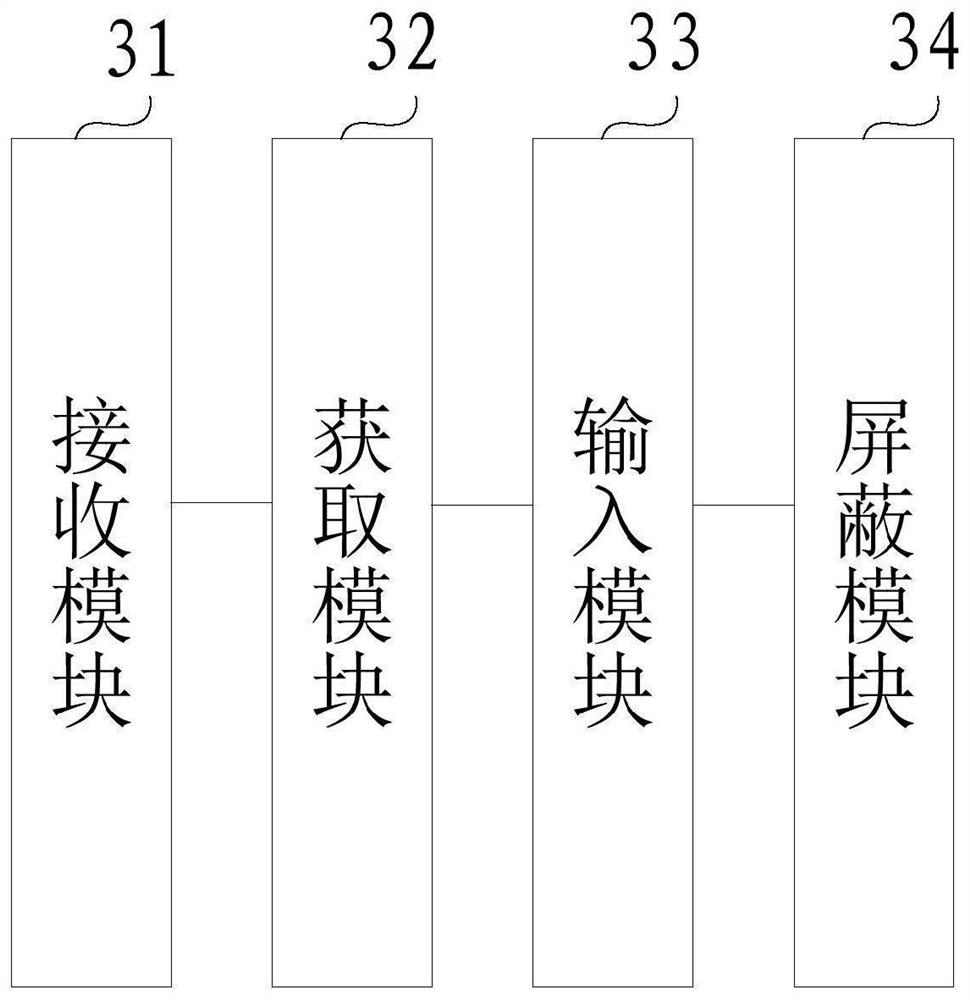
[0129] image 3 A schematic structural diagram of a cutover alarm shielding device for network slicing provided by Embodiment 3 of the present invention is shown, specifically including:
[0130] The receiving module 31 is adapted to receive a network slice cutover request, and obtain cutover feature information contained in the network slice cutover request;
[0131] The acquiring module 32 is adapted to acquire a slice cutover topology map corresponding to the cutover feature information, and determine slice cutover topology data corresponding to the slice cutover topology map;
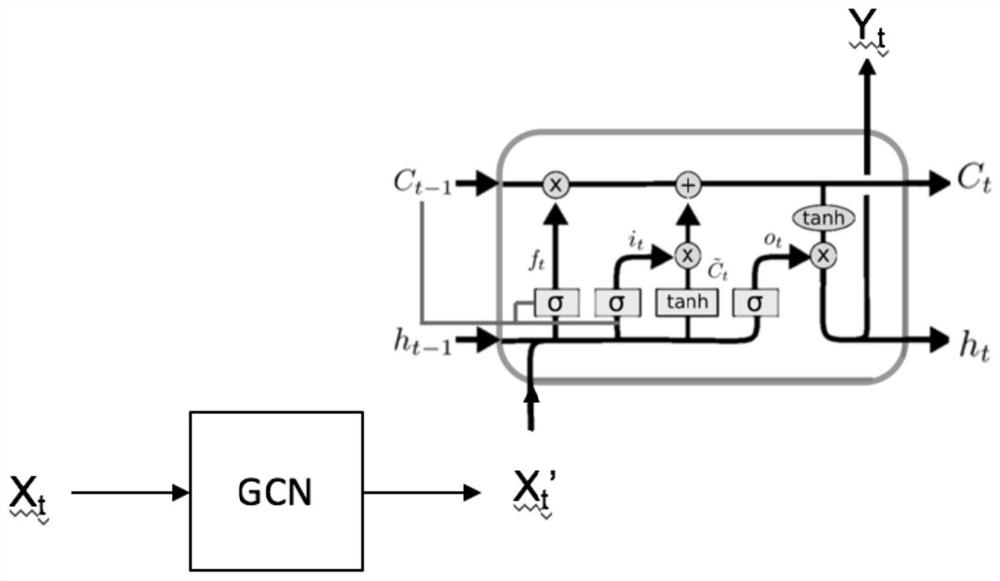
[0132] The input module 33 is adapted to input the slice cutover topology data into a preset alarm masking model, and obtain masking configuration information output by the alarm masking model;
[0133] The masking module 34 is adapted to perform alarm masking processing according to the masking configuration information.
[0134] Optionally, the acquisition module is specifically adapted to:
[...
Embodiment 4
[0147] Embodiment 4 of the present application provides a non-volatile computer storage medium, where at least one executable instruction is stored in the computer storage medium, and the computer executable instruction can execute the network slice cutover alarm in any of the above method embodiments Shielding method. The executable instruction may be specifically used to cause the processor to perform each corresponding operation in the foregoing method embodiments.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com