Key data self-destruction and automatic restoration method and device based on embedded system
An embedded system and key data technology, which is applied to data error detection, electrical digital data processing, and response error generation in the direction of redundancy in computing, and can solve the problem of one-key restoration of unrealized system interface buttons and damage to memory chips Problems such as physical structure, incomplete deletion of data, etc., to achieve the effect of ensuring non-recoverability, guaranteeing no damage, and avoiding hardware changes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
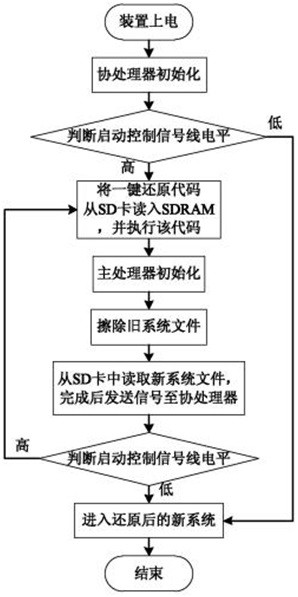
[0032] The following is attached Figure 1-2 and specific implementation modes The method and device for self-destruction and automatic restoration of key data based on embedded systems proposed by the present invention will be further described in detail. The advantages and features of the present invention will become clearer from the following description. It should be noted that the drawings are in a very simplified form and all use imprecise scales, which are only used to facilitate and clearly assist the purpose of illustrating the embodiments of the present invention. In order to make the objects, features and advantages of the present invention more comprehensible, please refer to the accompanying drawings. It should be noted that the structures, proportions, sizes, etc. shown in the drawings attached to this specification are only used to match the content disclosed in the specification, for those who are familiar with this technology to understand and read, and are ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com