Federated machine learning method and device based on security computing, device and medium
A machine learning and federation technology, applied in the field of machine learning, can solve the problems of model exposure, security machine learning data privacy leakage, etc., to achieve the effect of reducing nodes, preventing model parameter leakage, and reducing the risk of data loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other. The present application will be described in detail below with reference to the accompanying drawings and embodiments.
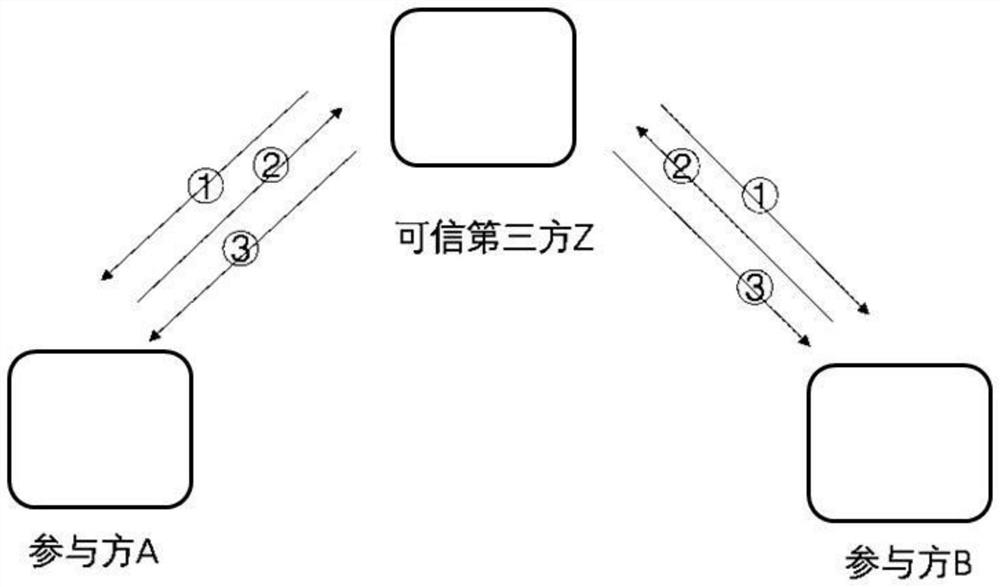
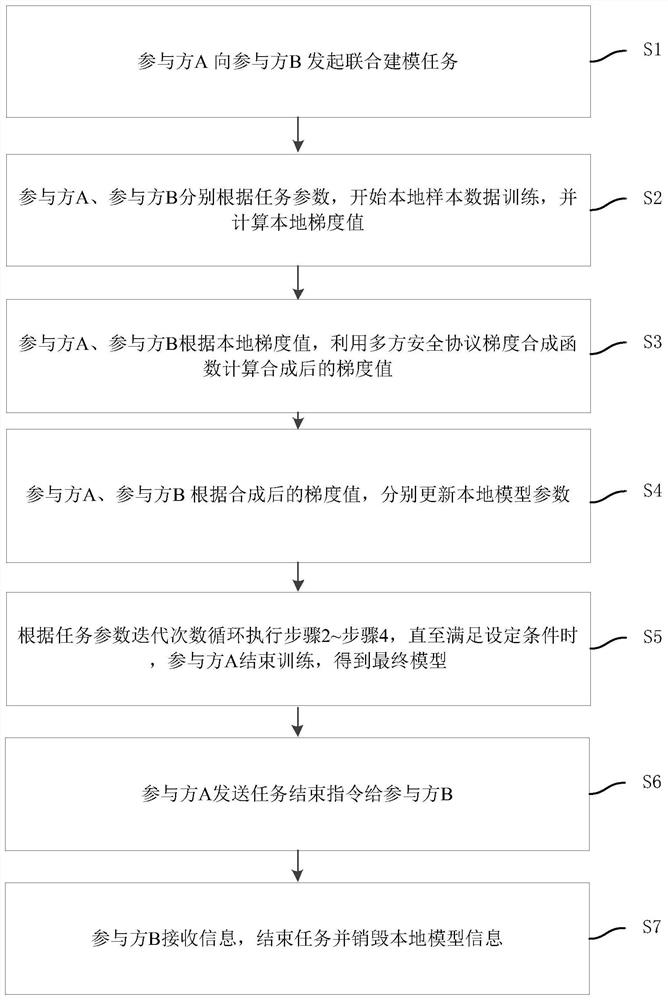
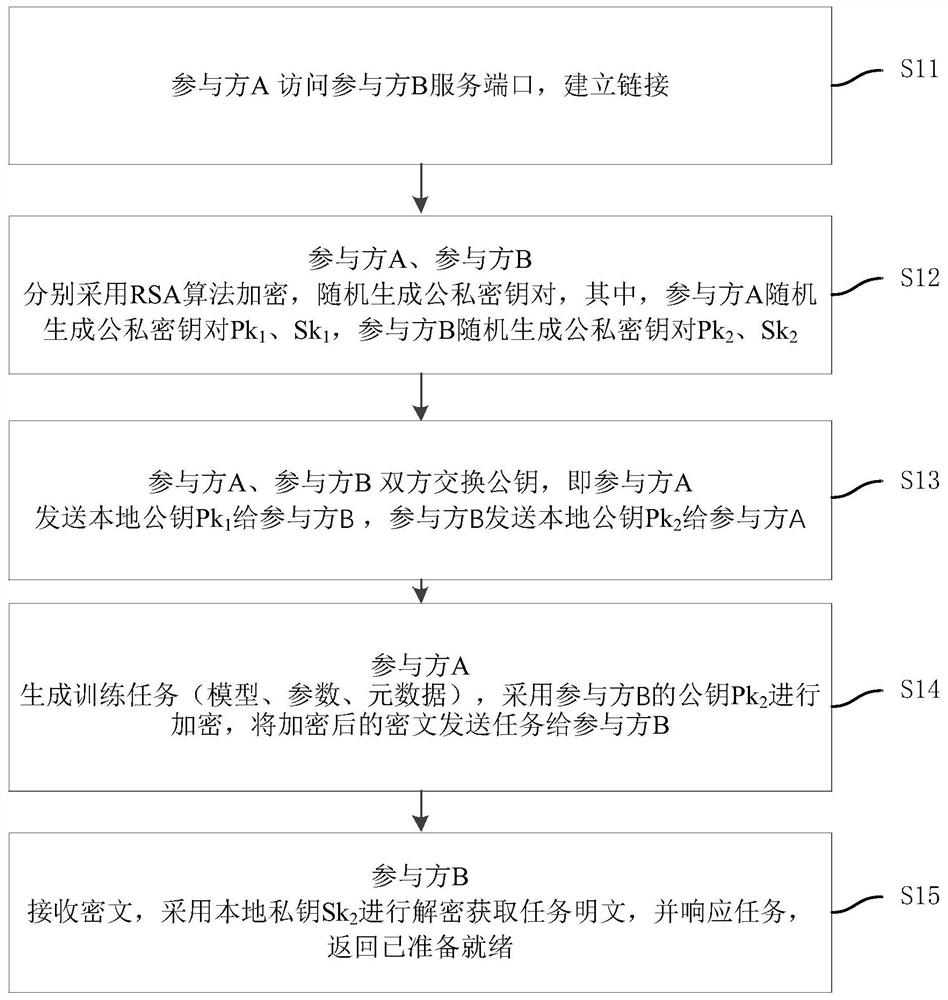
[0053] In the era of big data, the use of data is ubiquitous, and the risk of data leakage in the process of data circulation has become a problem that cannot be ignored. Privacy Computing (Privacy Computing) allows users to implement data analysis and calculation on the premise that the data itself is not leaked to the outside world. Typical privacy-secure computing technologies include blockchain, multi-party secure computing, and federated learning frameworks.
[0054] Multi-party secure computing refers to the safe completion of certain collaborative computing through the joint participation of multiple parties without a trusted third party. That is, in a distributed network, each part...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com