Credible data product delivery method
A data product and reliable technology, applied in the field of data transactions, can solve the problems of unreachable, inconvenient processing and analysis, and inconvenient integration of data, and achieve the effect of ensuring reasonable use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] The invention provides a credible data product delivery method, which includes a safe delivery method, a controllable delivery method and a standardized use delivery method.
[0034] As one of the methods: safe delivery method, its implementation process is as follows:
[0035] The supply and demand side installs the open source application container engine Docker; virtualizes the container according to the order details; saves the current container state; the supplier registers the compliant data product to the data platform, and copies the data product into the container through the front-end processor; records the container Operation log, and store the container operation log in the relational database MySQL for management; provide the usage method of the container to the demand-side customer; after the demand-side customer completes the use, apply to copy the results from the container; the demand-side customer Confirm use and destroy the container.
[0036] In thi...
Embodiment 2
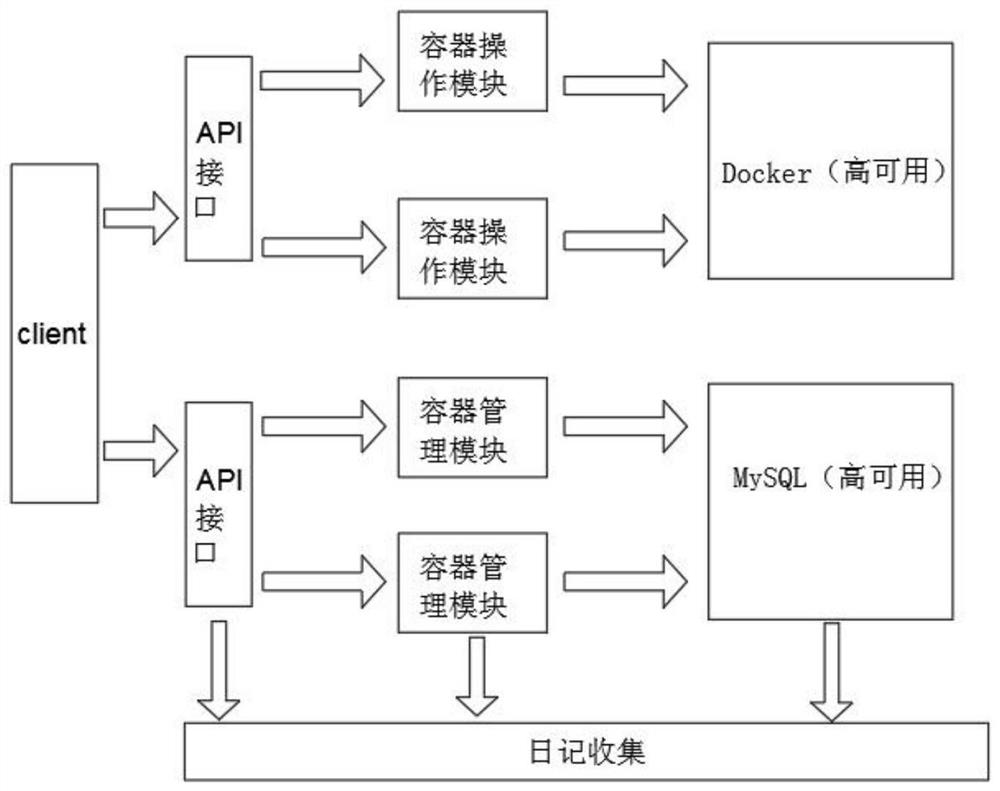
[0058] In order to realize the trusted data product delivery method in Embodiment 1, the present invention provides a total system architecture for implementation, such as figure 1 As shown, it consists of Api interface, container operation module, container management module, and log collection. Among them, the Api interface provides a trusted delivery interface for data transactions; the container operation module uses Docker virtual container technology to implement containers to provide guarantees for trusted delivery. It also supports custom implementation of containers, and its functions include starting containers, stopping containers, initializing containers, deleting containers, copying files to containers, and copying files from containers; the container management module manages container operations, including recording, displaying, Resource management, state maintenance, etc.; log collection centrally manages container logs, api module logs, container operation modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com