Symmetrical encryption and decryption algorithm subpackage processing method
A technology of symmetric encryption algorithm and encryption and decryption algorithm, which is applied in the direction of encryption device with shift register/memory, digital transmission system, electrical components, etc. It can solve the limitation of transmission medium transmission volume, troublesome key management, easy to be cracked, etc. problem, to avoid the limitation of transmission medium, reduce the probability of transmission failure, and save time consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] In order to understand the technical content and advantages of the present invention more clearly, the present invention will be further described in detail in conjunction with the accompanying drawings.
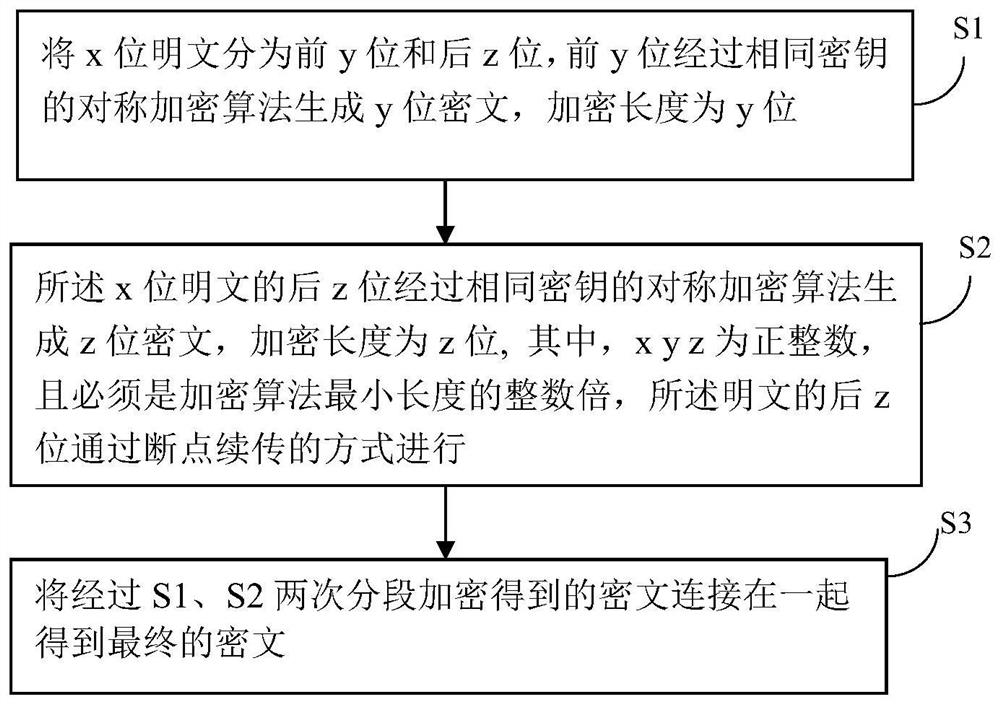
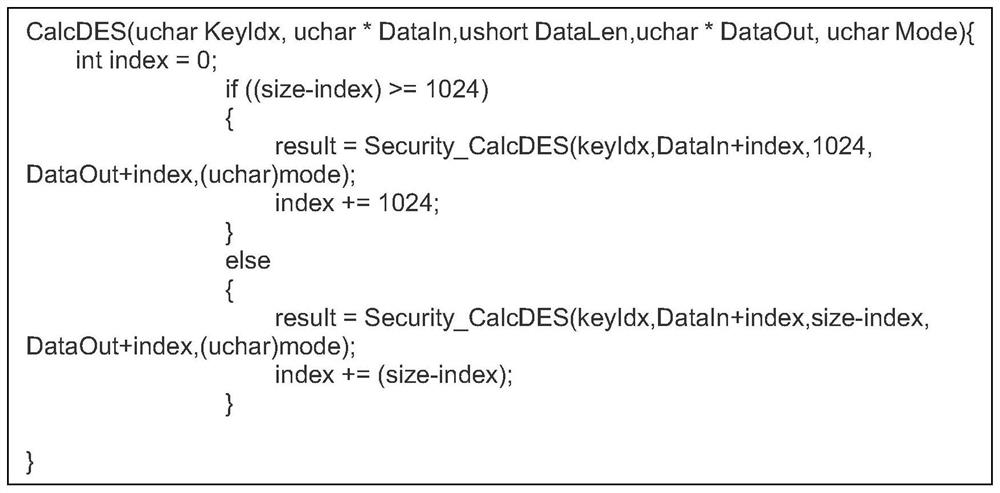
[0049] Different symmetric encryption algorithms have different subpackage methods, but the idea is roughly the same. Both are based on the encrypted data obtained by one-time encryption and segmental encryption of the encrypted data. Therefore, segmental encryption can be used.
[0050] like figure 2 Shown, the present invention relates to a kind of symmetric encryption and decryption algorithm packet processing method, described method comprises the following steps:
[0051] S1. Divide the x-bit plaintext into the first y-bit and the last z-bit. The first y-bit is passed through the symmetric encryption algorithm of the same key to generate y-bit ciphertext, and the encryption length is y bits;
[0052] S2, the last z bits of the x-bit plaintext pass through the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com