Implementation method and device for improving operation speed of industrial security host
A technology of running speed and industrial safety, applied in the field of implementation methods and devices for improving the running speed of an industrial safety host, can solve the problems of slow running of the host system, increased memory usage, downtime, etc. The effect of usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
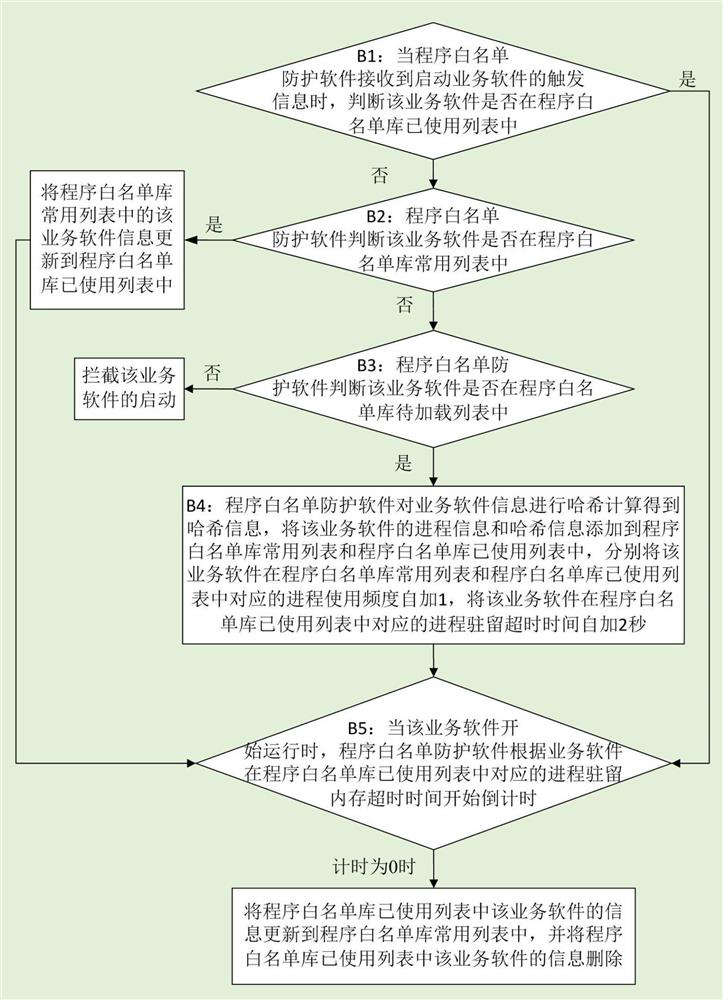
[0027] Embodiment 1 of the present invention provides an implementation method for increasing the operating speed of an industrial security host computer, such as figure 1 shown, including:
[0028] Step B1: When the program whitelist protection software receives the trigger information for starting the business software, it judges whether the business software is in the used list of the program whitelist library, if yes, execute step B5, otherwise execute step B2;
[0029] In this embodiment, the programs in the program whitelist library used list are extracted from the program whitelist full library, and are being used by the program whitelist protection software. The hash table of the program whitelist library process file; the program whitelist library The initial value of the used list is empty, and the used list of the program whitelist library is stored in memory;
[0030] Optionally, in this embodiment, if it is judged that the business software is in the used list of...
Embodiment 2
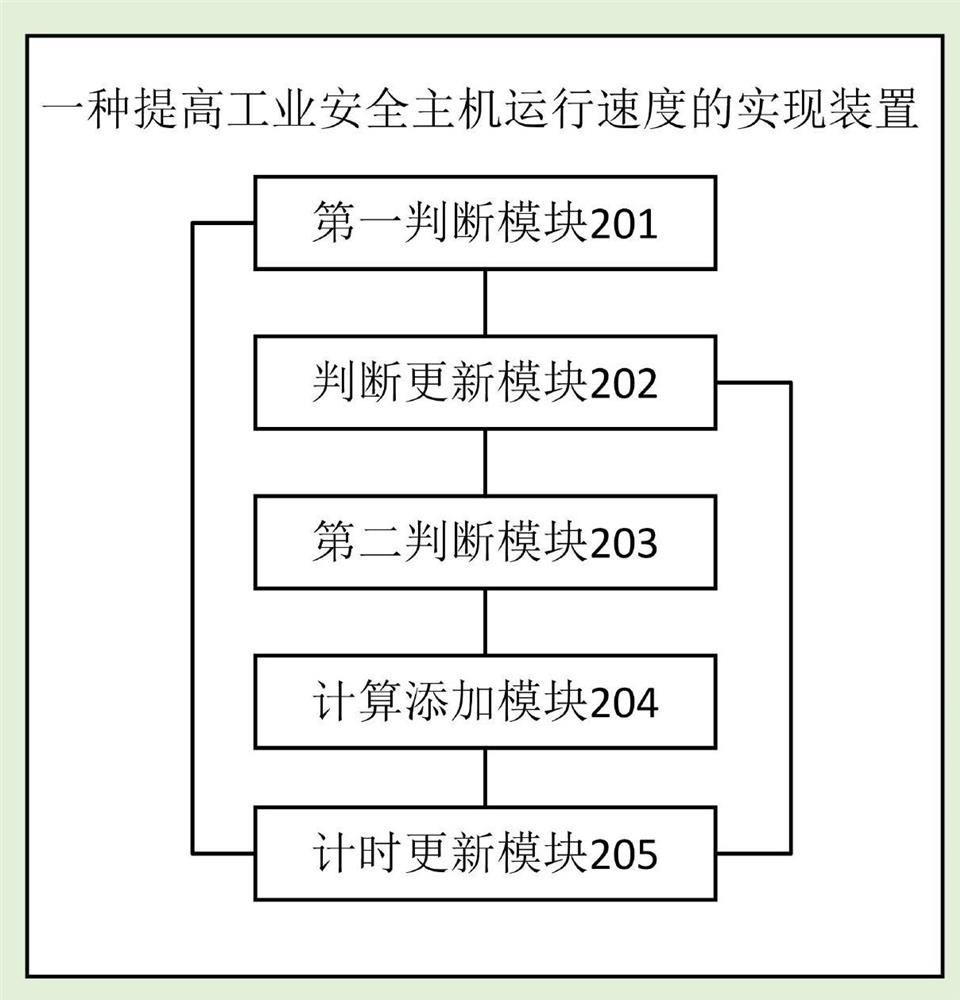
[0046] Embodiment 2 of the present invention provides an implementation device for increasing the operating speed of an industrial security host, such as figure 2 shown, including:
[0047] The first judging module 201 is used to judge whether the business software is in the used list of the program whitelist library when receiving the trigger information for starting the business software, if so, trigger the timing update module 205, otherwise trigger the judgment update module 202;
[0048] Judgment update module 202, used to judge whether the business software is in the common list of the program whitelist database, if so, update the business software information in the common list of the program whitelist database to the used list of the program whitelist database, and execute the trigger timing update module 205, otherwise trigger the second judging module 203;
[0049] The second judging module 203 is used to judge whether the business software is in the list to be loa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com