Software use authorization protection method
A technology of authorization protection and software authorization, applied in digital data protection, program/content distribution protection, instruments, etc., can solve the problems of loss of security risk, frequent software theft, etc., to achieve the effect of protecting correct use and reducing security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
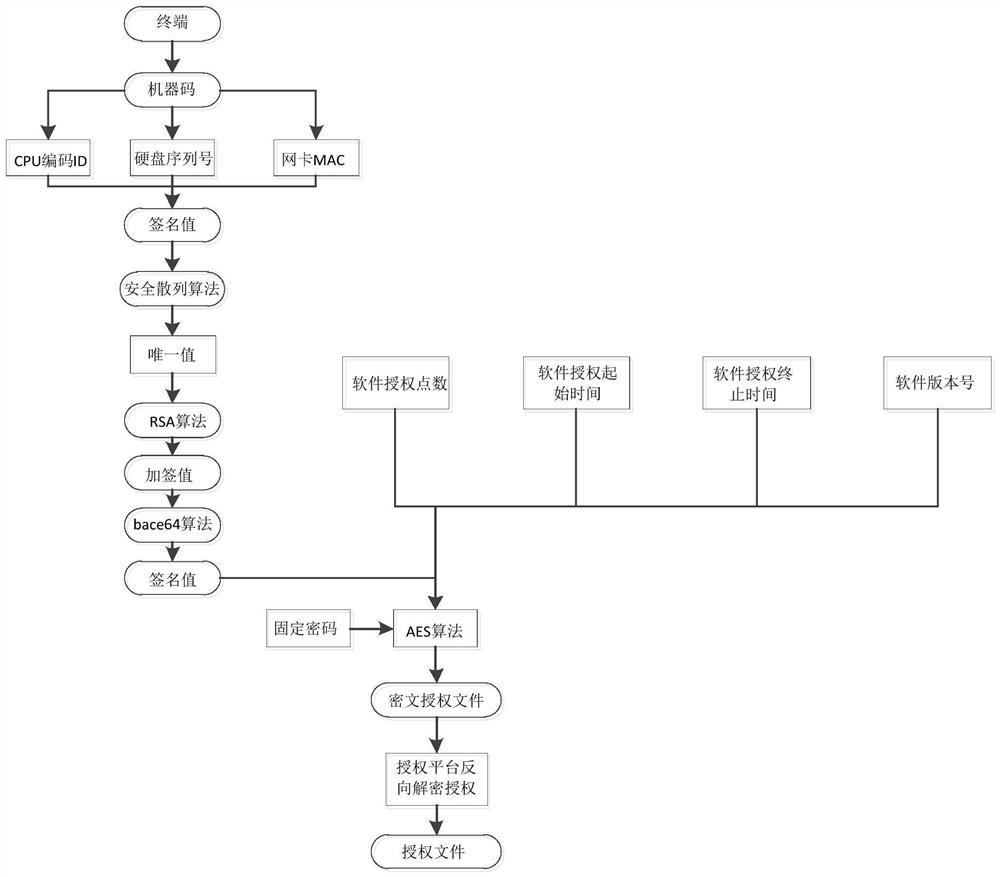
[0025] refer to figure 1 , this embodiment discloses a software authorization protection method, the method is:
[0026] S1. Generate a machine code, and determine the uniqueness of the standard software installation machine through the machine code;
[0027] S2. Generate a software XML authorization file template, and generate and obtain it through management platform configuration;
[0028] S3. Signature value generation, the machine code string is first generated by a secure hash algorithm to generate a unique value, and then the unique value is calculated by the RSA algorithm to generate a signed value, and the signed value is encoded by base64 encoding to generate a signed value;
[0029] S4. Based on the plaintext content of the authorization file template generated by S2 and S3, the AES algorithm is used to encrypt the content through a preset fixed password to generate a ciphertext authorization file;
[0030] S5. After the authorization file is decoded and authorize...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com