User internet data traceability identification method and device
A data traceability and user technology, applied in the field of computer networks, can solve problems such as affecting accuracy, incomplete data packets, and consuming CPU performance, and achieve the effect of accurate auditing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
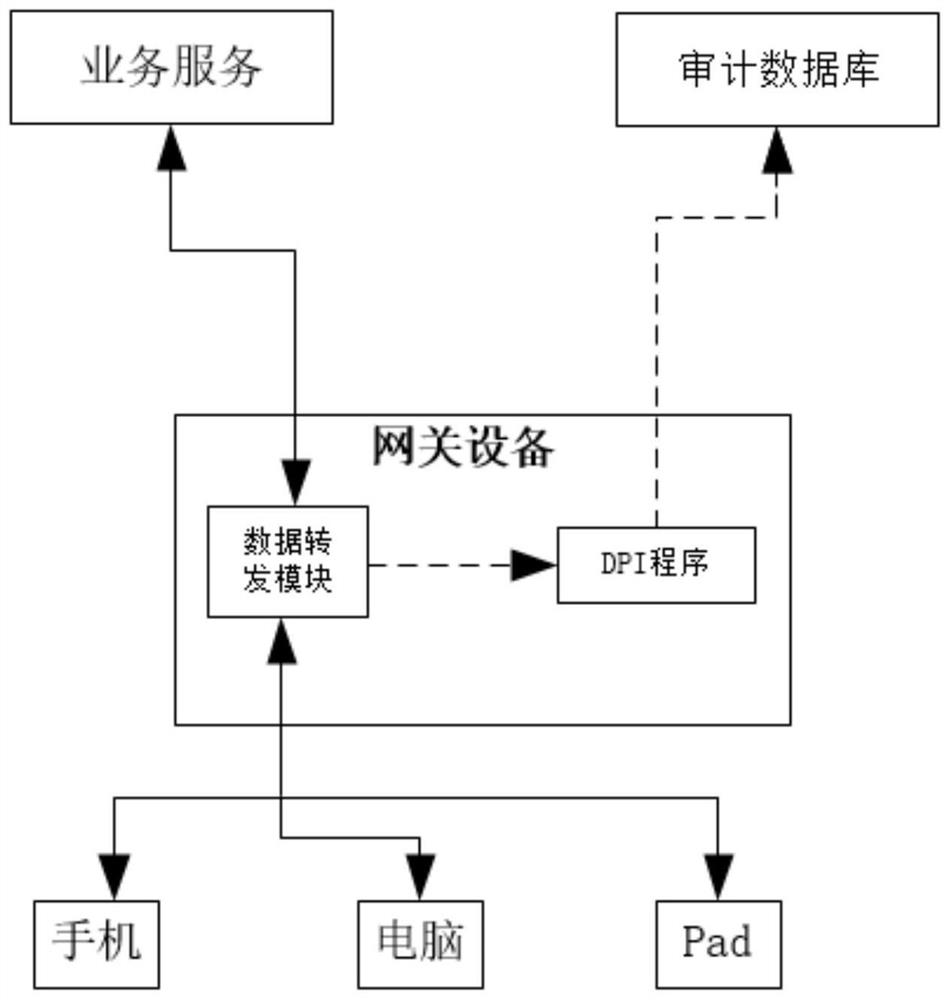
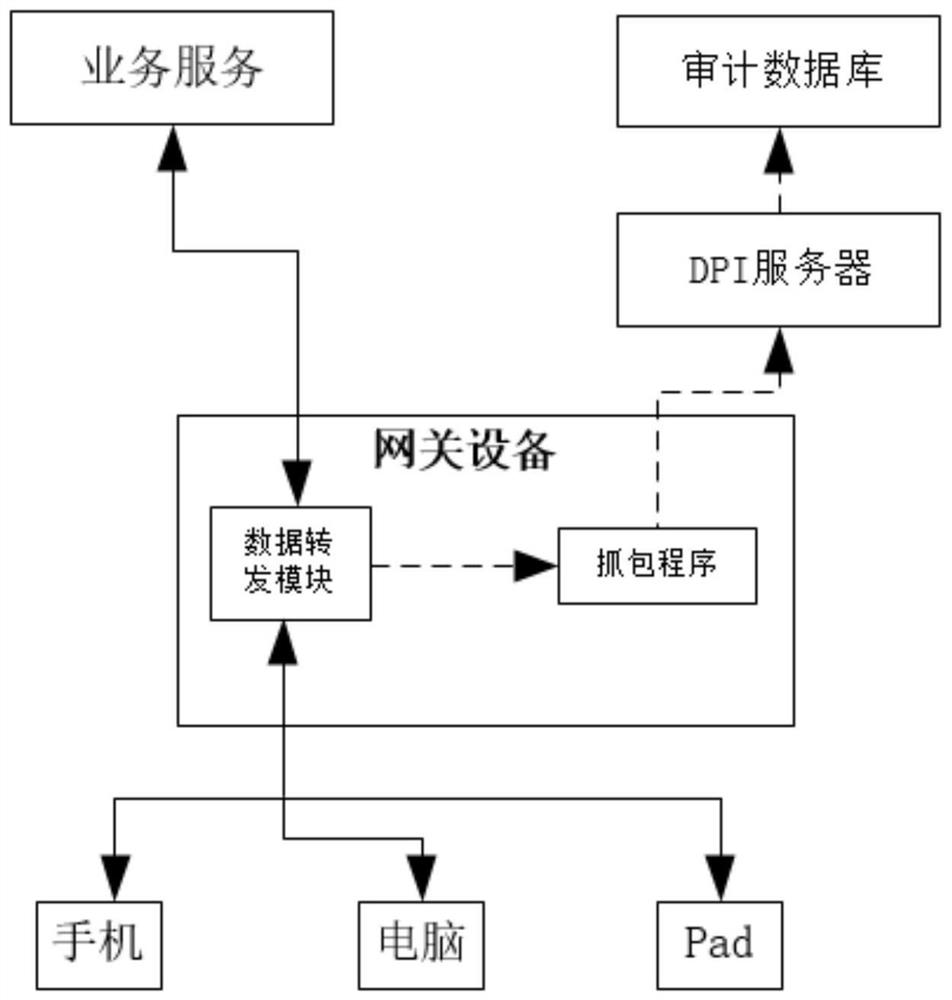
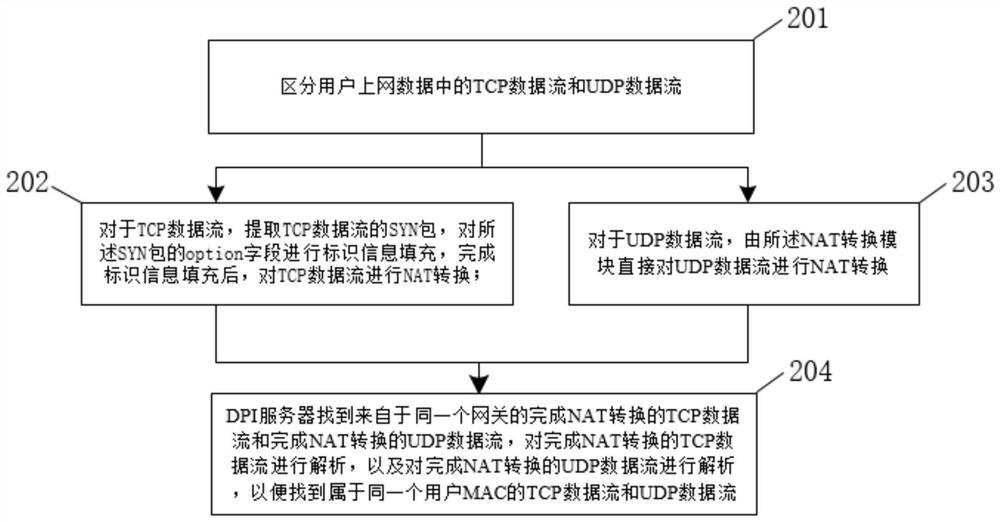
[0049] The embodiment of the present invention provides a method for traceability and identification of user online data, such as image 3 shown, including:
[0050] In step 201, the TCP data flow and the UDP data flow in the user's online data are distinguished based on the data packet protocol type.
[0051] In step 202, for the TCP data flow, the data forwarding module sends the TCP data flow to the TCP option processing module, and the TCP option processing module extracts the SYN packet of the TCP data flow, and fills the option field of the SYN packet with identification information , after filling the identification information, send it to the NAT conversion module, and the NAT conversion module performs NAT conversion on the TCP data flow; wherein, the identification information includes the user MAC.
[0052] In step 203, for the UDP data flow, the NAT conversion module directly performs NAT conversion on the UDP data flow based on the first rule.
[0053] The NAT c...
Embodiment 2
[0098] In embodiment 1, both the TCP data flow and the UDP data flow need to carry out NAT conversion after completing the filling of the identification information; the NAT conversion includes converting the source port of the user's online data through the relevant information of the private network IP address in the user's online data; Taking Table 1 as an example, the first rule in Embodiment 1 above is described.
[0099] In Table 1, the calculation method of the start port and the end port is:
[0100] Start port = (the fourth segment of the private network IP address -1)*512+1024;
[0101] End port = start port + 511;
[0102] And the end port is less than 65535.
[0103] The private network IP address consists of four segments; for example, the fourth segment of the private network IP address 192.168.1.2 is 2, and the calculated starting port corresponding to the private network IP address 192.168. 1.2 The corresponding end port is 2047.
[0104] Table 1:
[0105]...
Embodiment 3
[0112] The embodiment of the present invention provides a user online data traceability identification device, such as Figure 7 As shown, one or more processors 21 and memory 22 are included. in, Figure 7 A processor 21 is taken as an example.
[0113] Processor 21 and memory 22 can be connected by bus or other means, Figure 7 Take connection via bus as an example.
[0114] The memory 22, as a non-volatile computer-readable storage medium, can be used to store non-volatile software programs and non-volatile computer-executable programs, such as the method for traceability and identification of user online data in Embodiment 1. The processor 21 runs the non-volatile software program and instructions stored in the memory 22 to execute the method for identifying the source of the user's online data traceability.
[0115] The memory 22 may include a high-speed random access memory, and may also include a non-volatile memory, such as at least one magnetic disk storage device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com