Micro-service operation method, device and equipment and readable storage medium
A technology for microservices and configuration information, applied in the computer field, can solve the problems of fragmentation, a large number of basic components, and backward governance methods, and achieve the effect of reducing operating costs, improving governance and control capabilities, and meeting the needs of upgrades and governance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
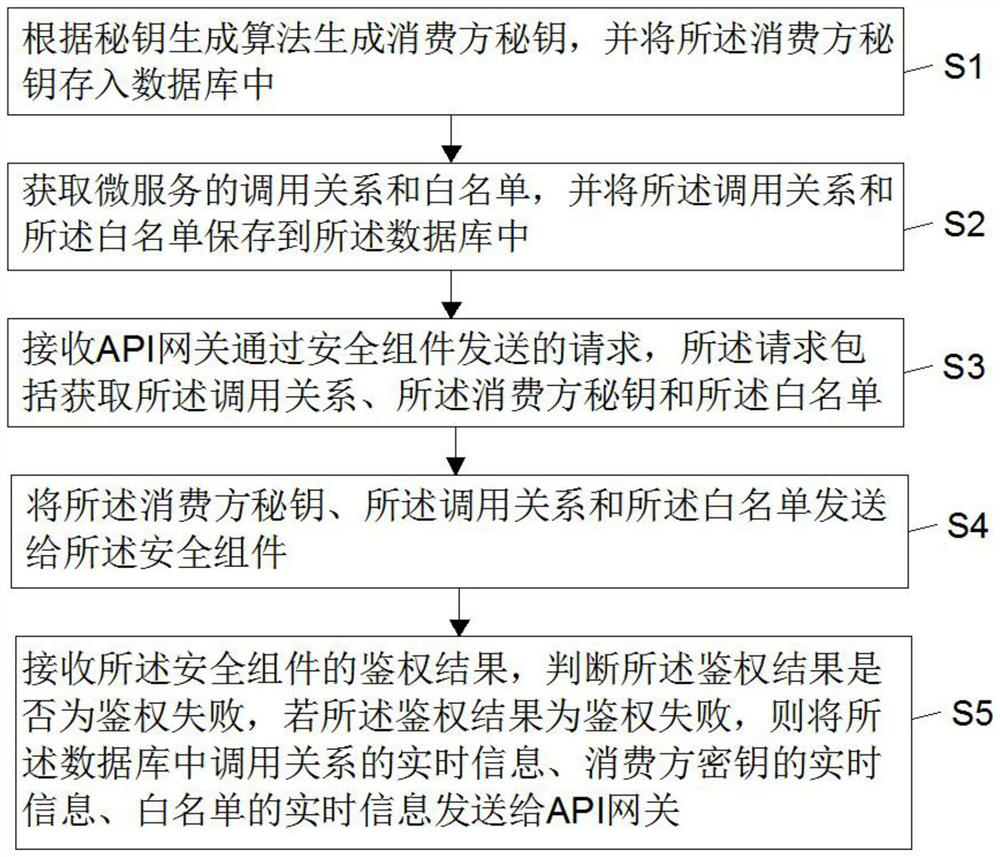
[0055] Such as figure 1 As shown, this embodiment provides a microservice operation method, and the method includes step S1, step S2, step S3, step S4 and step S5.
[0056] Step S1, generating the consumer secret key according to the secret key generation algorithm, and storing the consumer secret key in the database;
[0057] Step S2, obtaining the calling relationship and whitelist of the microservice, and saving the calling relationship and the whitelist into the database;
[0058] Step S3, receiving the request sent by the API gateway through the security component, the request includes obtaining the call relationship, the consumer secret key and the white list;
[0059] Step S4, sending the consumer key, the calling relationship and the whitelist to the security component;
[0060] Step S5, receiving the authentication result of the security component, judging whether the authentication result is an authentication failure, if the authentication result is an authenticati...
Embodiment 2
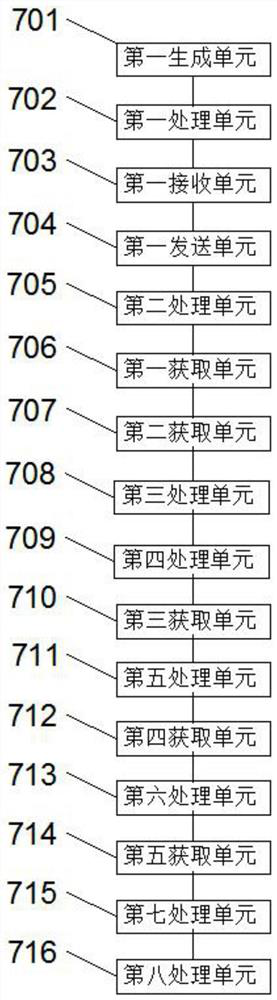
[0092] Such as figure 2 As shown, this embodiment provides a microservice operation device, which includes a first generating unit 701 , a first processing unit 702 , a first receiving unit 703 , a first sending unit 704 and a second processing unit 705 .
[0093] The first generating unit 701 is configured to generate a consumer secret key according to a secret key generation algorithm, and store the consumer secret key in a database;
[0094] The first processing unit 702 is configured to obtain the calling relationship and whitelist of the microservice, and store the calling relationship and the whitelist in the database;
[0095] The first receiving unit 703 is configured to receive a request sent by the API gateway through a security component, where the request includes obtaining the call relationship, the consumer secret key, and the white list;
[0096] A first sending unit 704, configured to send the consumer key, the calling relationship and the whitelist to the se...
Embodiment 3
[0115] Corresponding to the above method embodiment, the embodiment of the present disclosure further provides a microservice operation device. The microservice operation device described below and the microservice operation method described above can be referred to in correspondence.
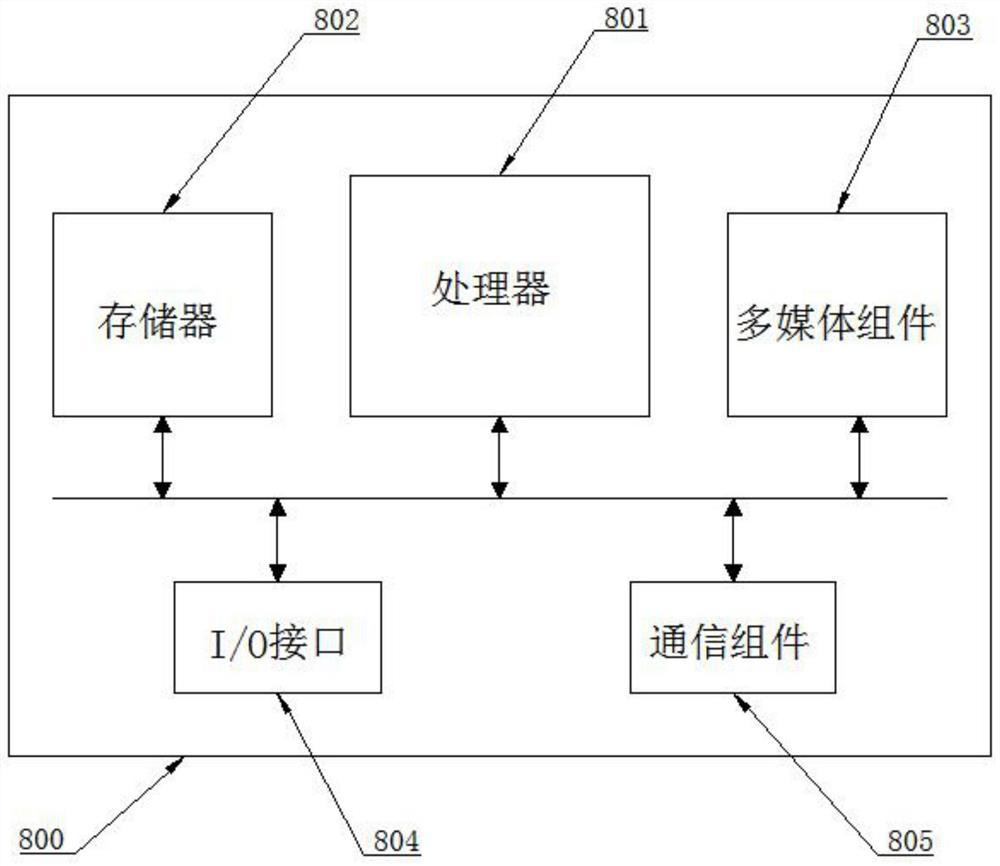
[0116] image 3 It is a block diagram of a microservice operating device 800 shown according to an exemplary embodiment. Such as image 3 As shown, the microservice operation device 800 may include: a processor 801 and a memory 802 . The microservice operating device 800 may also include one or more of a multimedia component 803 , an input / output (I / O) interface 804 , and a communication component 805 .
[0117] Wherein, the processor 801 is used to control the overall operation of the microservice operation device 800, so as to complete all or part of the steps in the above microservice operation method. The memory 802 is used to store various types of data to support operations on the micr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com