Terminal-based method and architecture for using security, monitoring and management of equipment account
A technology for managing terminals and equipment, applied in the direction of secure communication devices, digital transmission systems, electrical components, etc., can solve problems such as insufficient protection strength, unprotected equipment passwords of IoT devices, and failure to provide protection effects, etc., to increase usability And the effect of convenience and high safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
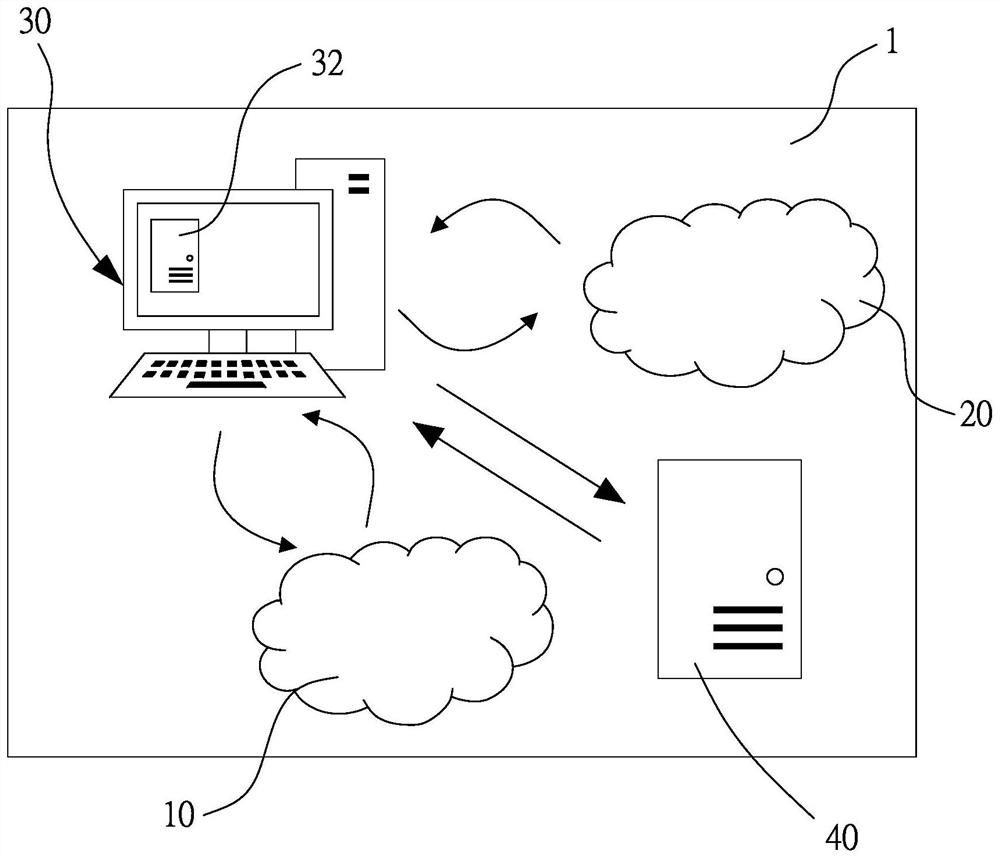
[0037] In order to illustrate the present invention more clearly, preferred embodiments are given and described in detail with the accompanying drawings as follows. figure 1 Shown is a network usage architecture 1 according to an embodiment of the present invention, including a decentralized network 10 , a device network 20 , a terminal device 30 , and an identity management system 40 .
[0038]The device network 20 includes a plurality of devices (not shown). The identity management system 40 is responsible for managing at least one digital identity of one of the devices allowed to use the device network 20 . In detail, each of the digital identities corresponds to a real user, and the user must pass authentication to confirm that the identity is correct, in order to obtain the digital identity to which it belongs, and then use the digital identity on the device network 20 through the digital identity. the device. In order to ensure the credibility of the authentication, ea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com