Data inspection method and device, computer readable storage medium and electronic equipment
A data inspection and computer program technology, applied in the field of financial technology, can solve problems such as the high error rate of decryption result judgment and the inability to accurately judge the encryption party and decryption party, so as to avoid the large judgment error rate and improve the accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
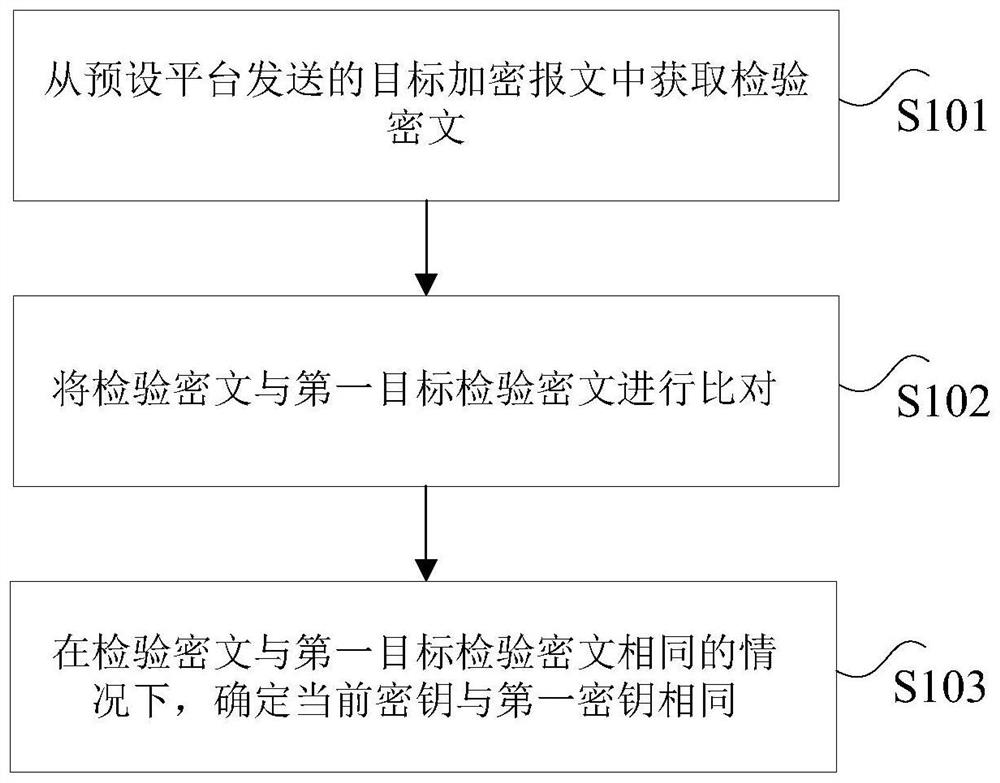
[0032]In the existing related technologies, DES (Data Encryption Standard, data encryption standard) is an encryption and decryption algorithm widely used in the banking industry. The DES algorithm is encrypted in blocks, and every 8 bytes is a block. It supports ECB (Electronic Codebook), CBC (Cipher Block Chaining, ciphertext block chaining), CFB (Cipher Feedback, ciphertext feedback) and OFB. (Output Feedback, output feedback) 4 operation modes, of which the most commonly used is the ECB mode. In the case of encryption, the length of the plaintext is N, then the length of the ciphertext is ((N / 8)+1)*8; in the case of decryption, the length of the ciphertext is N, then the length of the plaintext is ((N / 8)-1) *Between 8 and N. In many cases, ECB and CBC use a PKCS#5 complementing principle. This complementing part is used in the existing algorithm to judge whether the decryption is successful and effective.
[0033] Specifically, the complementing principle of PKCS#5 is: w...
Embodiment 2
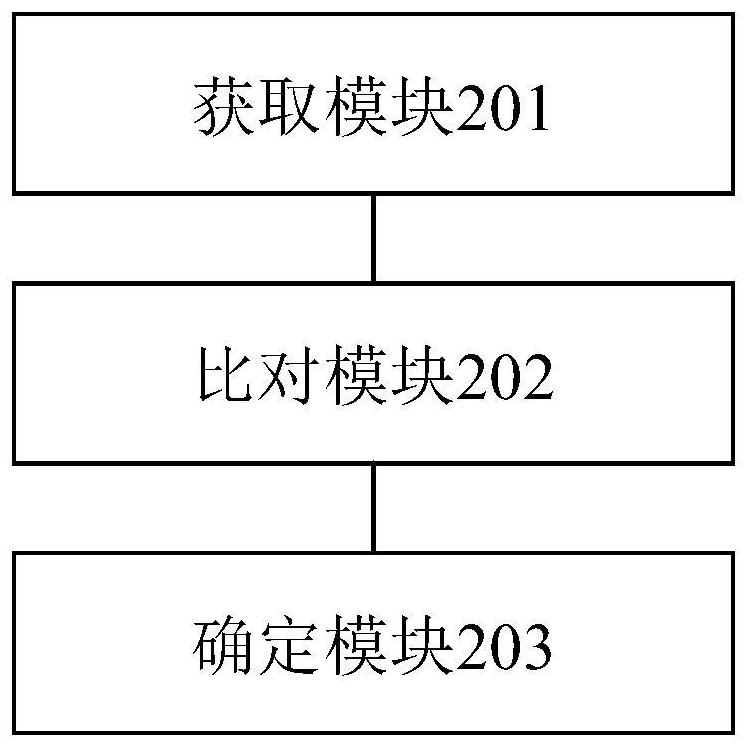
[0081] According to an embodiment of the present invention, an embodiment of a data checking apparatus is provided, wherein, figure 2 is a schematic diagram of an optional data checking device according to an embodiment of the present invention, such as figure 2 As shown, the device includes:
[0082] The obtaining module 201 is configured to obtain the verification ciphertext from the target encrypted message sent by the preset platform, wherein the verification ciphertext is the ciphertext obtained after the preset platform encrypts the preset verification plaintext based on the first key, The first key is used to encrypt the first data sent by the preset platform to the terminal device, and the plaintext is verified as a fixed-length character, and is used to verify the first key;
[0083] The comparison module 202 is configured to compare the verification ciphertext with the first target verification ciphertext, wherein the first target verification ciphertext is the ci...
Embodiment 3
[0096] According to another aspect of the embodiments of the present invention, a computer-readable storage medium is also provided, and a computer program is stored in the computer-readable storage medium, wherein the computer program is configured to execute the above-mentioned data verification method when running.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com