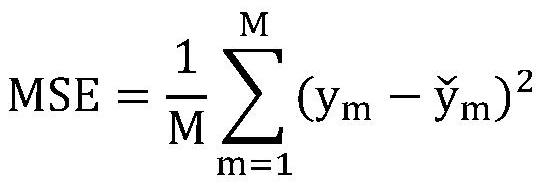Method and system for defending network traffic reconnaissance based on generative adversarial network, terminal and storage medium
A network traffic and network technology, applied in the field of network security technology and data privacy protection, can solve the problems of high operating cost, network feature confusion and deception defense technology deployment, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings.
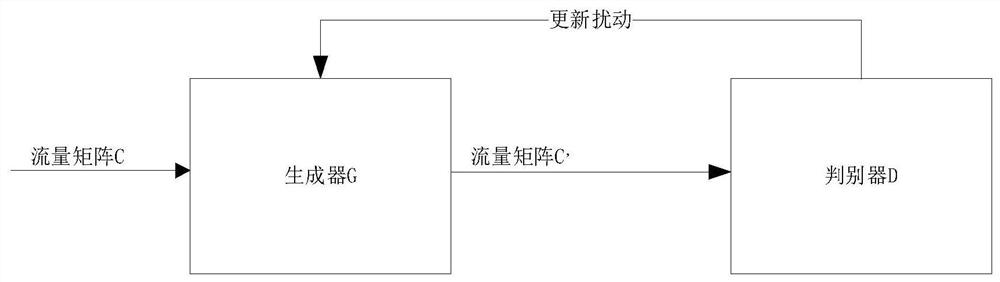
[0038] Embodiments of the present invention provide a method and system for resisting network traffic reconnaissance based on generative adversarial networks, including the following steps:
[0039] 1) Data preprocessing
[0040] 1.1) Dataset
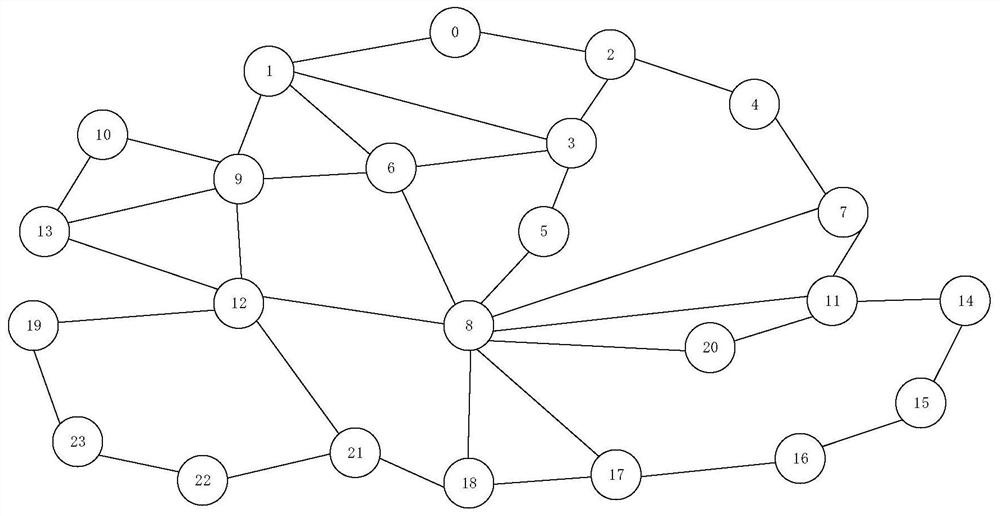
[0041] The data set of the present invention adopts a GEANT network with 24 nodes and 37 links. The schematic diagram of the GEANT network is as follows: figure 1 As shown, the dataset contains topology information of a network and a large number of routing tables and traffic information. The routing information consists of BGP routes of the GEANT network, collected from 00:30 on January 1, 2005 to 15:30 on April 21, 2005, once every 15 minutes. All router ID and absolute time information is anonymized in a publicly available dataset with attributes of time (points in 15-minute intervals) and traffic values (unit: kbps (kil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com