Data aggregation method capable of protecting privacy
A technology for data aggregation and privacy protection, which is applied to the public key and key distribution of secure communication, which can solve the problems of high resource overhead on the client side, achieve comprehensive security analysis, reduce interaction, and reduce resource overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
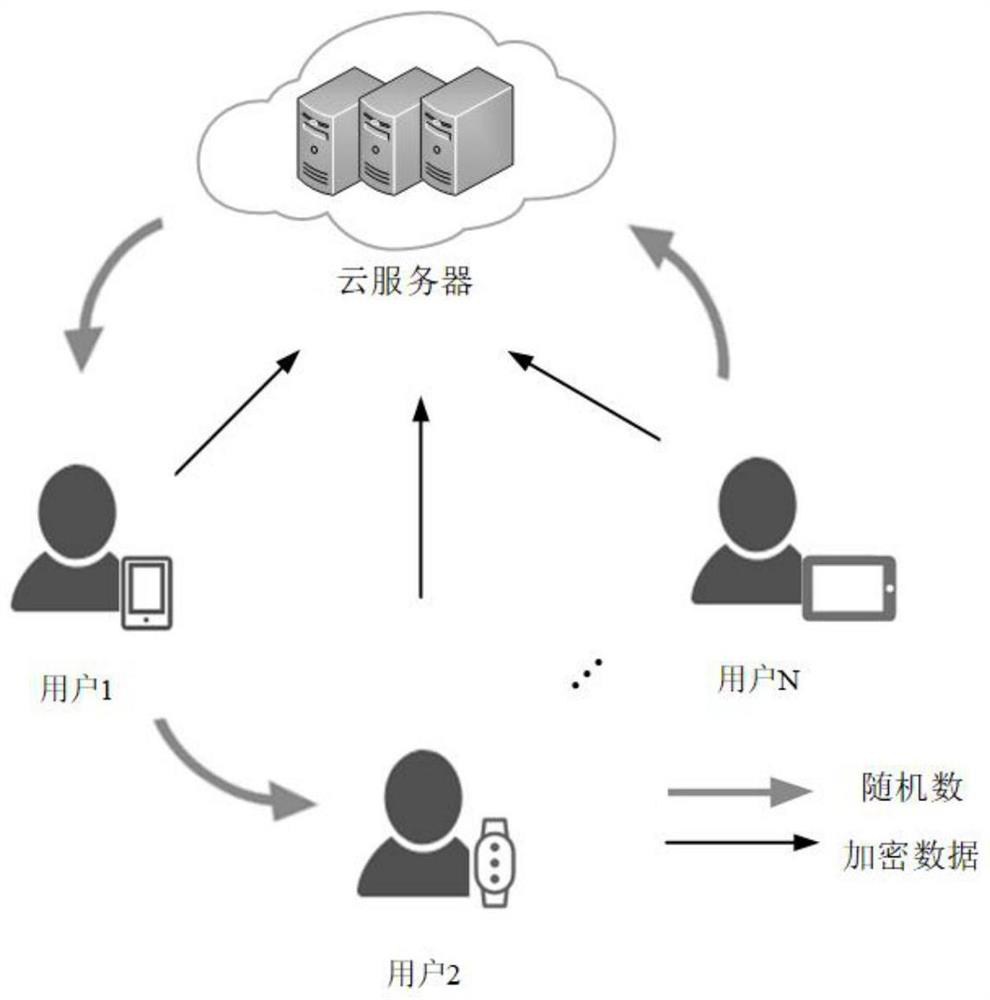
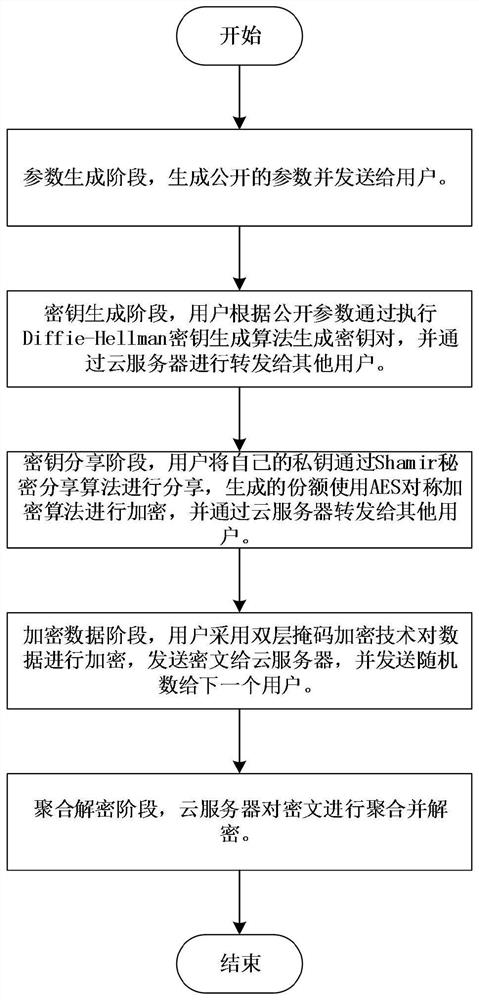
[0049] In this embodiment, see figure 1 , a privacy-preserving data aggregation method, is applied in a network environment composed of cloud servers and N users. In this embodiment, the process mainly includes: a parameter generation stage, a key generation stage, a key sharing stage, an encrypted data stage, and an aggregation decryption stage. See figure 2 , and includes the following steps:
[0050] Step 1. Parameter generation stage:
[0051] Step 1.1. Given the security parameter λ, the number of users N and the threshold value t, select a prime number q with a length of 2λ, and determine the q-order multiplication cyclic group let generator Define a hash function F: {0,1} * →{0,1} 2λ and a prime p of length λ;
[0052] Step 1.2, the cloud server will expose parameters Send to the i-th user u i ∈U, where U represents the set of all users;
[0053] Step 2: Key generation stage:
[0054] Step 2.1, the i-th user u i Execute the Diffie-Hellman key generation a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com