Encryption key management
A technology for encrypting keys and keys, which is applied in the field of memory and can solve problems such as loss of content in volatile memory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
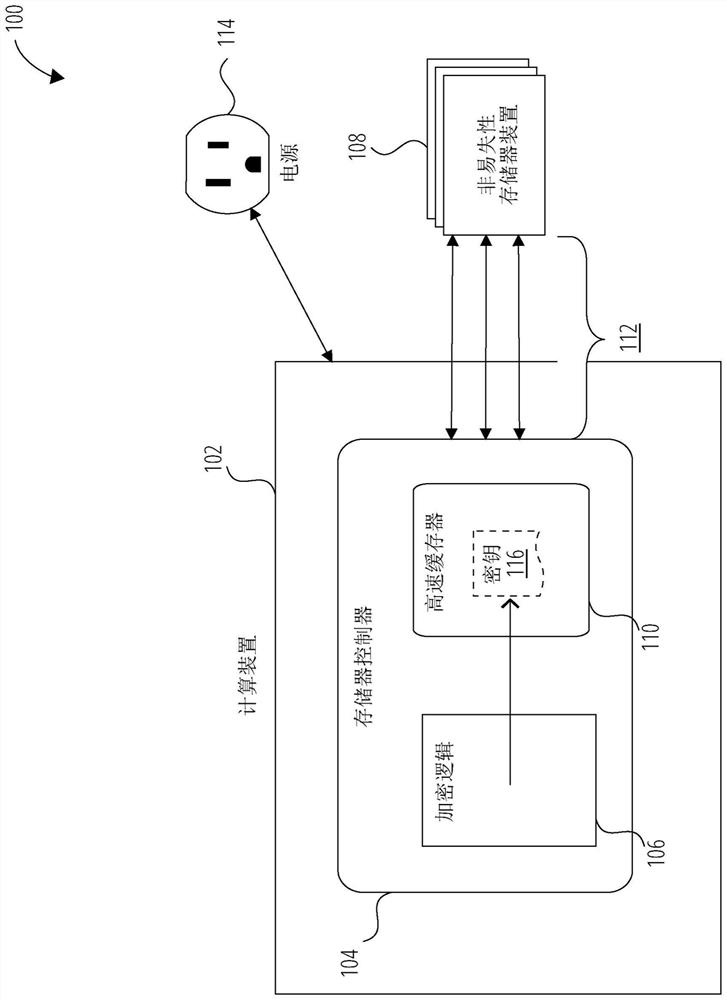
[0010] Encryption methods may use block ciphers to provide data security, for example, using keys to authenticate data. For example, a key can convert data from plaintext to ciphertext when encrypting; and convert data from ciphertext to plaintext when decrypting. Block ciphers provide block transformation of information bits to encrypt (or conversely, decrypt) data. For example, Advanced Encryption Standard (AES) is a type of block cipher. Additionally, block ciphers may operate in different modes within the encryption device / method, eg, as a "stream cipher" using a counter. For example, a counter can be used as a basis for changing the underlying key used by the block cipher so that the key changes over time; in turn, changing the data in the encrypted data stream. For example, Galois / Counter Mode (GCM) is a type of stream cipher.
[0011] It can be complex and cumbersome to secure NVDIMM devices.
[0012] Examples of systems and methods described herein provide for eras...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com