Anti-confusion method, system and application
A decompilation and real technology, applied in the field of anti-obfuscation, can solve problems such as omission, poor anti-obfuscation effect, inability to effectively detect and kill malicious scripts, and achieve the effect of eliminating omissions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
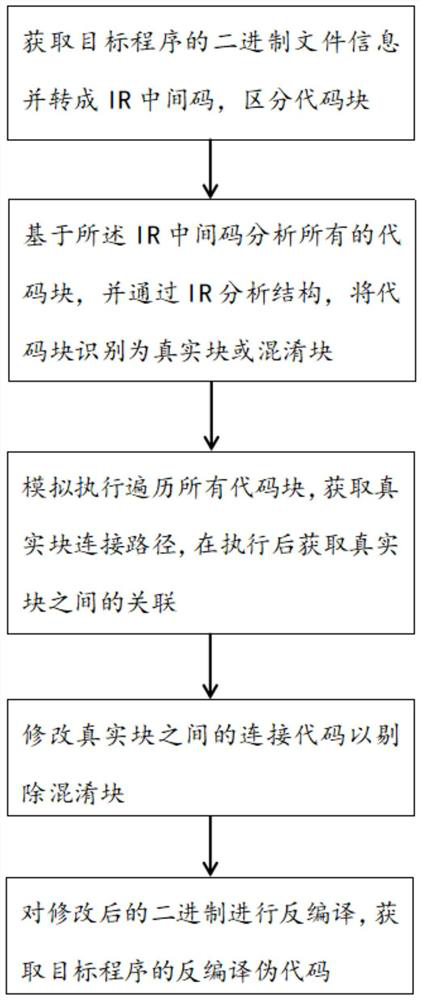
[0054] An anti-obfuscation method such as figure 1 ,include:
[0055] S10: Obtain the binary file information of the target program and convert it into an IR intermediate code to distinguish code blocks.
[0056] In one embodiment, Hopper, 010Editor, IDA or Ghidra decompilation tool is used for decompilation, and the binary file is divided into code blocks.
[0057] S20: Analyze all code blocks based on the IR intermediate code, and identify the code blocks as real blocks or obfuscated blocks by analyzing the structure through IR.
[0058] In one embodiment, block classification is performed using block instruction features:
[0059] If both goto and jcndv exist in the block, it is judged as an obfuscated block, and the obfuscated block is marked and the precursor of the obfuscated block is executed. If the obfuscated block has only one predecessor, the precursor block is also marked as an obfuscated block.
[0060] Both goto and jcndb exist in the block, and it is judged a...
Embodiment 2
[0085] A deobfuscation system including:
[0086] Data acquisition module to obtain the binary file information of the target program
[0087] The data processing module converts the target program into an IR intermediate code and distinguishes the code blocks; analyzes all the code blocks based on the IR intermediate code, and identifies the code blocks as real blocks or obfuscated blocks through the IR analysis structure; the simulation execution traverses all the code blocks Code block, obtain the connection path of the real block, and obtain the association between the real blocks after execution; modify the connection code between the real blocks to eliminate the obfuscated block; decompile the modified binary to obtain the decompiled pseudocode of the target program .
Embodiment 3
[0089] An anti-obfuscation device includes: a memory and a processor. Executable code is stored in the memory, and when the executable code is executed by the processor, the processor is caused to execute the deobfuscation method according to the first embodiment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com