Android malicious software detection method and system based on multi-modal graph characteristics
A technology of malware and detection methods, applied in the field of malicious code analysis, can solve the problems of lack of information, incomplete capture of malicious behavior information, and impact of classification results, and achieve the effect of good processing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
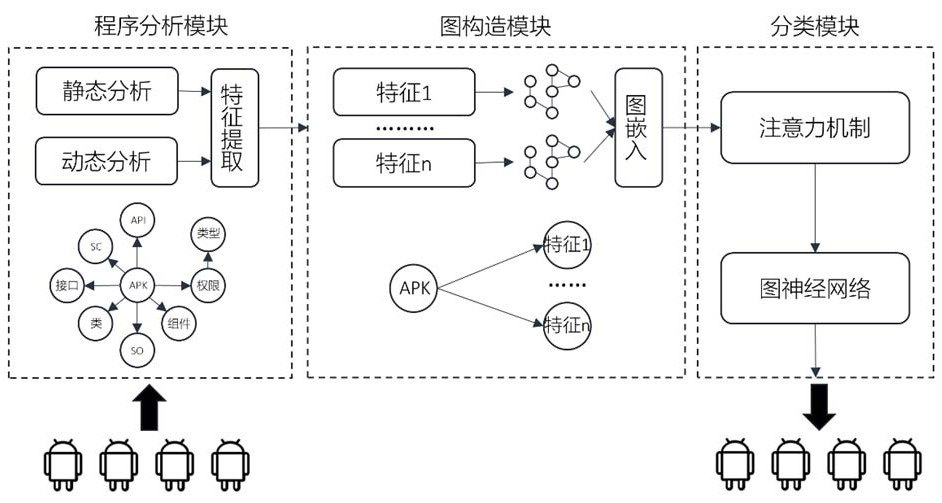
[0114] Step 1: Build a data set, collect 1600 Android benign samples, 1600 malicious samples, a total of 3200 samples, and divide them into training set, validation set and test set according to the ratio of 8:1:1, while ensuring that the benign samples in each set are The ratio of samples to malicious samples is 1:1;
[0115] Step 2: Process all samples in the dataset, including the following steps:
[0116] Step 2.1: Perform static analysis on the Android APK file, use static analysis tools to obtain its static characteristics, and obtain permission characteristics, API, class, interface characteristics, .SO file characteristics and component characteristics;
[0117] Step 2.2: Dynamically analyze the Android APK file, use the dynamic analysis sandbox to obtain its dynamic characteristics, and obtain the system call characteristics;
[0118] Step 2.3: Process the static features obtained in step 2.1 and the dynamic features obtained in step 2.2 as multi-dimensional features...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com