Key exchange acceleration method for establishing trusted execution environment security level
An execution environment and key exchange technology, which is applied to public keys for secure communication, secure communication devices, and key distribution, can solve the problems of slow public key exchange, high CPU overhead, and insufficient timeliness, and achieve fast one-to-many , to achieve the effect of flow control and avoid leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
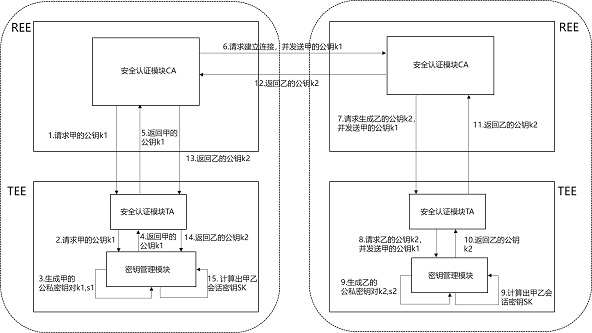
[0024] The technical solutions of the present invention will be further described in detail below with reference to the accompanying drawings.
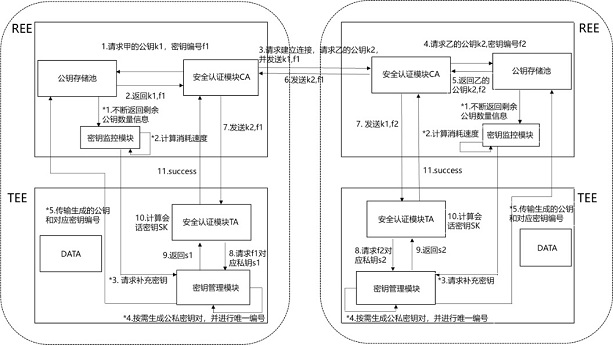
[0025] compared to figure 1 The traditional method process, the exchange process provided by this embodiment is as follows figure 2 As shown, the specific work consists of two parts, and the process is as follows:
[0026] (1), the key generation part
[0027] The key management module is connected to the public key storage pool, and writes the generated key into the public key storage pool. Each key corresponds to a unique key number, corresponding to its specific location in a public key storage pool. The key generation frequency can be flexibly set according to needs, and can be switched on demand, which can meet the needs of high-speed public key distribution, and the decryption terminal can quickly query the private key according to the number for decryption.
[0028] The public key storage pool module is connected to the key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com