Private transaction generation and verification method and system based on block chain
A blockchain and transaction technology, applied in the blockchain field, can solve problems such as security risks, algorithm differences, cut off transaction tracking, etc., and achieve the effects of avoiding security risks, high credibility, and preventing transaction fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
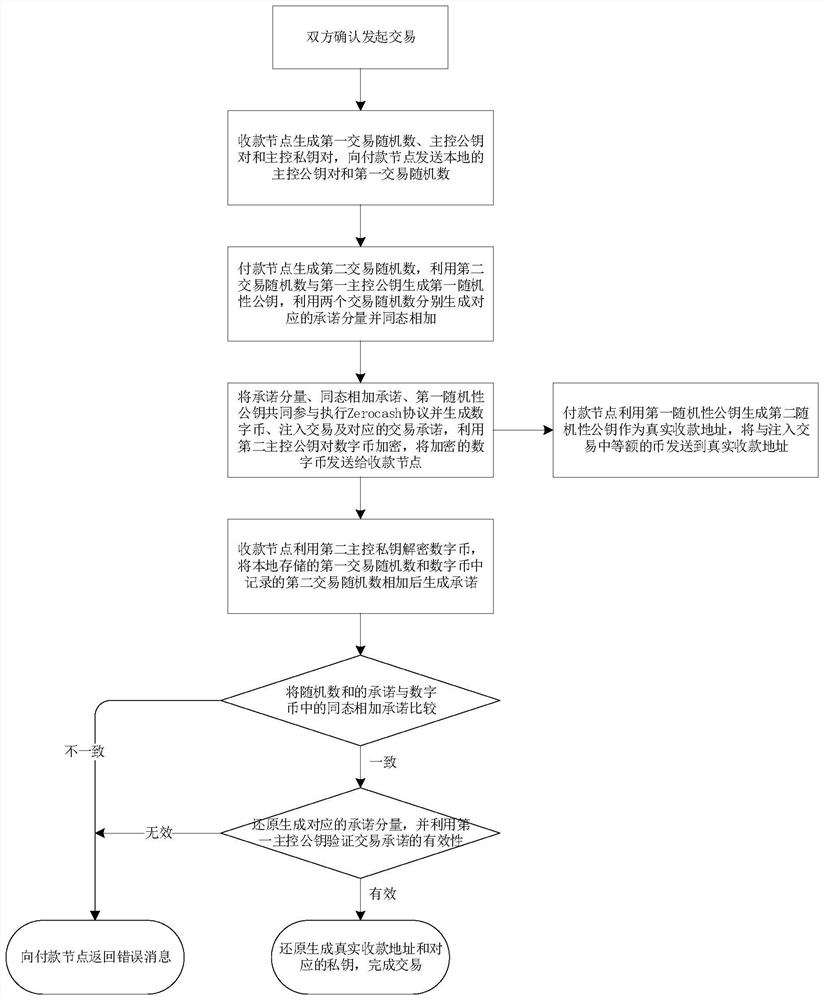
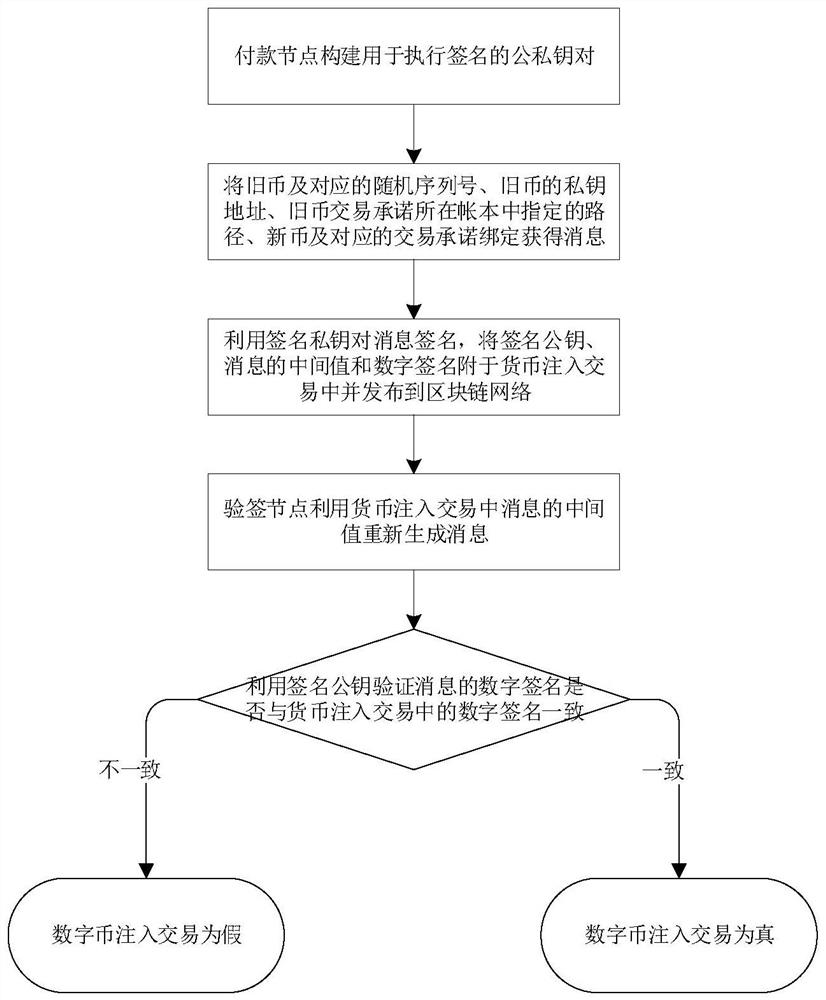
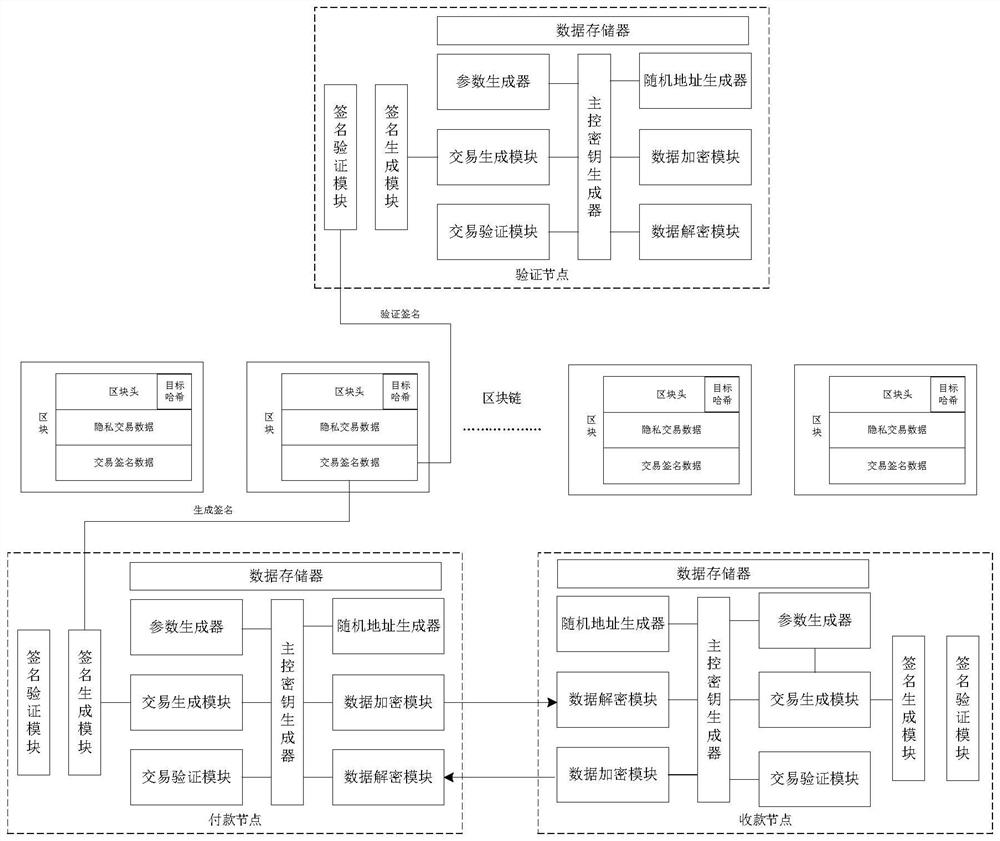
[0074] In order to make the objectives, technical solutions and advantages of the present invention clearer, the embodiments of the present invention will be further described in detail below with reference to the accompanying drawings.
[0075] The Zerocash protocol is a digital currency based on zk-SNARK, which uses zero-knowledge proof as a verification method in transactions. In the specific Zerocash transfer process, it can be understood that the prover is the sender of the Zerocash transaction, the verifier is the maintenance node of the blockchain, and the message to be verified is the transaction transfer information. The sender of the transaction provides a proof, and other users cannot infer the transfer information (including the sender's address and transaction amount) through this proof, but the blockchain node can still verify the legitimacy of each transaction transfer. As the earliest widely used zk-SNARK in the digital currency system, Zcash aims to provide us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com