Data security management method and system based on block chain
A technology of data security and management methods, applied in the field of blockchain-based data security management methods and systems, to achieve the effect of improving reliability and security, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
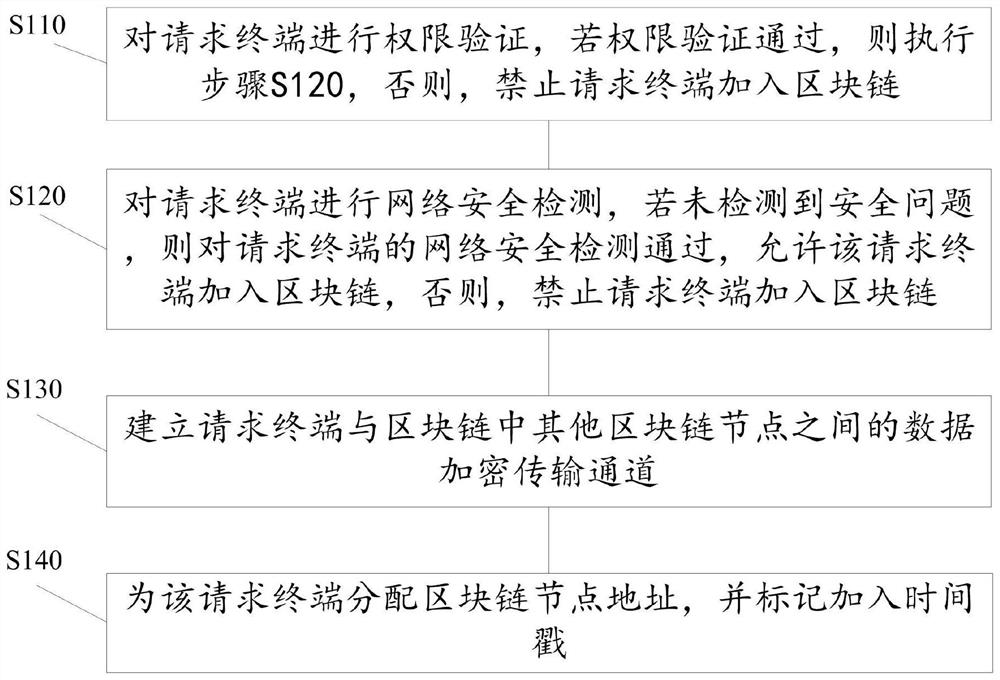
[0035] like figure 1 As shown, the present application provides a blockchain-based data security management method, which includes the following steps:
[0036] Step S1: Perform authority verification and network security detection on the requesting terminal requesting to join the blockchain. If both the authority verification and the network security detection pass, the requesting terminal is allowed to join the blockchain, and the requesting terminal and each of the blockchains are established. Data encrypted transmission channel between blockchain nodes, otherwise, the requesting terminal is prohibited from joining the blockchain.
[0037] Specifically, in response to a request for joining the blockchain sent by the requesting terminal, the requesting terminal is subjected to authority verification and network security detection. If both the authority verification and the network security detection pass, the requesting terminal is allowed to join the blockchain, and the req...
Embodiment 2
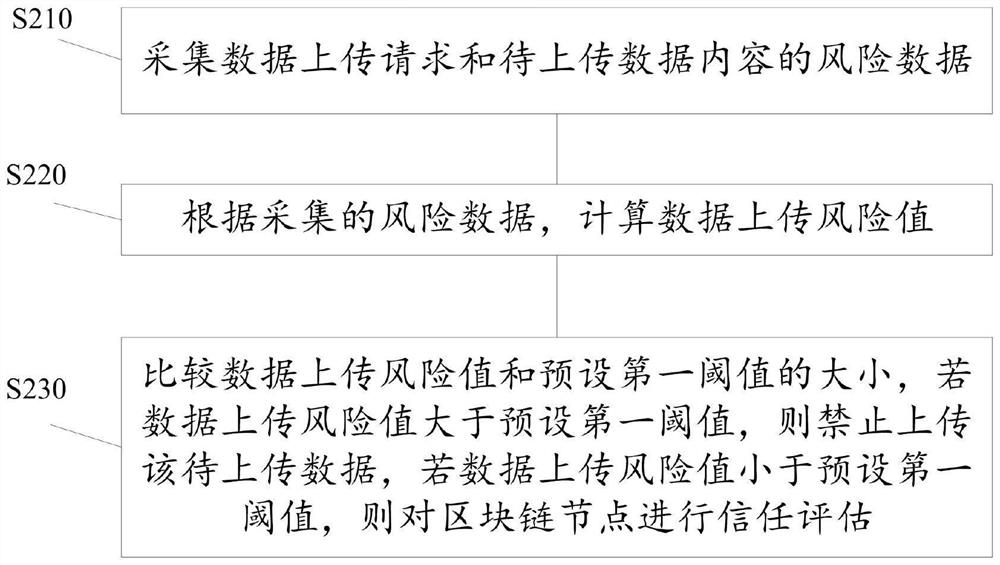
[0082] like Figure 5 As shown, the present application provides a blockchain-based data security management system 100, the system 100 includes:
[0083] The data security verification module 10 is used to perform security verification on the data upload request and the content of the data to be uploaded in response to the data upload request sent by the blockchain node. Trust evaluation data of blockchain nodes, otherwise, uploading the data to the blockchain is prohibited;
[0084] The data processor 30 is configured to calculate the reliability value of the blockchain node requesting to upload the data according to the trust evaluation data;
[0085] The data comparison module 40 is used to compare the reliability value of the blockchain node requesting to upload data and the size of the preset second threshold. If the reliability value of the blockchain node requesting to upload data is less than the preset second threshold, the request is prohibited. The blockchain nod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com