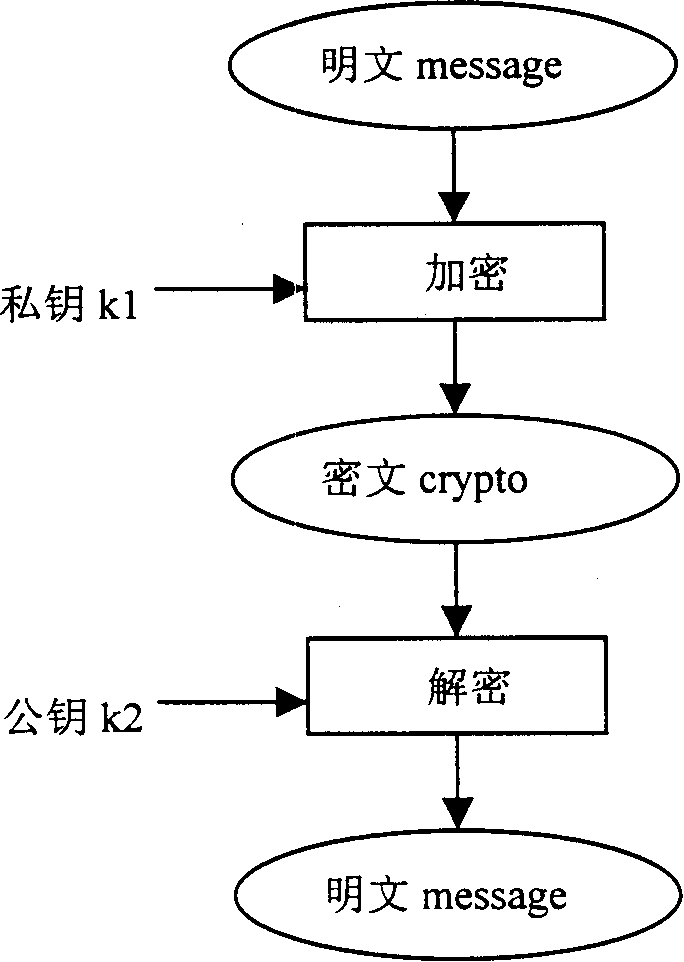
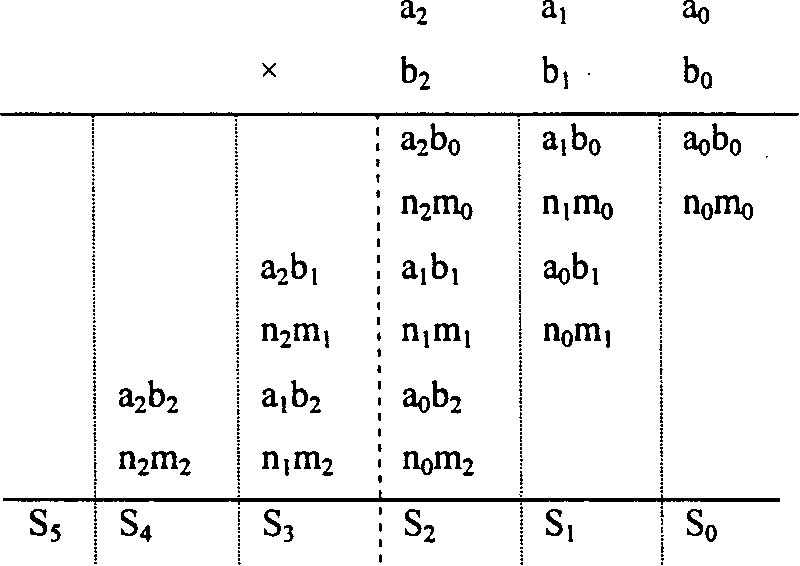Montgomery analog multiplication algorithm for VLSI and VLSI structure of intelligenjt card analog multiplier
A technology of multipliers and smart cards, applied in instruments, computing, digital transmission systems, etc., can solve the problems of large implementation area and low speed of modular exponentiation of RSA cryptographic coprocessors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
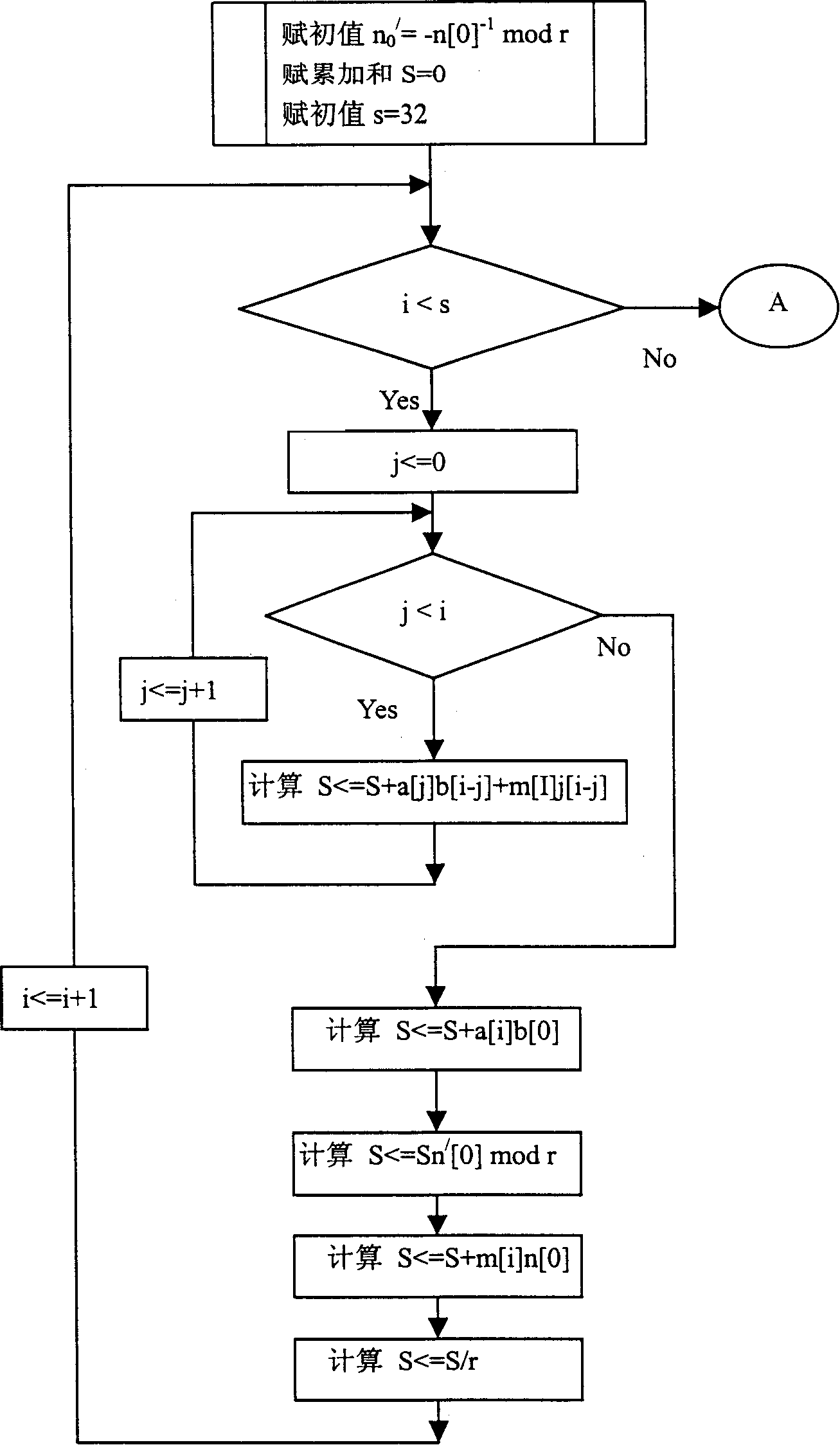
[0067] please see figure 2 . It is an example of the modified FIPS method for s=3. It is divided into A, B, C three parts. A corresponds to figure 2 The calculation on the right side of the dot-dash line is to calculate the low-order s words of the product result; B corresponds to the calculation on the left side of the dot-dash line, and the high-order s words of the product result. In order to save storage space, the storage space of the high-order s words is borrowed from the storage variable m, and finally the Montgomery product is stored in (m[s-1]m[s-2]...m[1]m[0]). Since the Montgomery product can only be guaranteed to be in the range of [0, 2N), it should also be adjusted to the range of [0, N). C just completes this adjustment function.
[0068] The computational bottleneck of the above algorithm is the number of multiplications. A needs to perform s 2 +2s multiplications, B needs to perform s 2 -s times of multiplication, a total of 2s 2 +s multiplications...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com