Safe network transmission method and system
A technology of secure network and transmission method, applied in the direction of transmission system, digital transmission system, data exchange network, etc., can solve the problem of host or specific port attack without providing technical means, and achieve the effect of preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
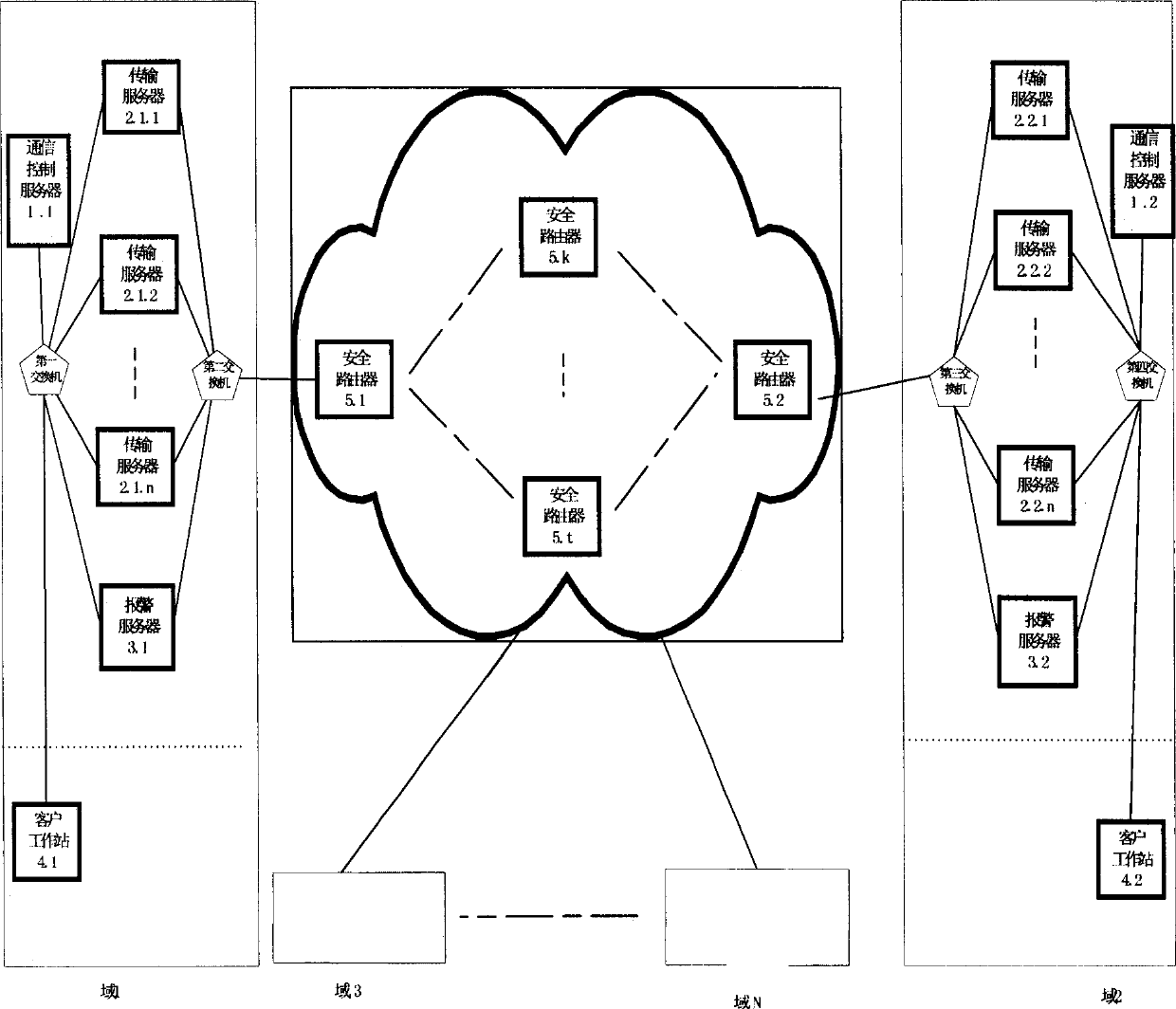
[0095] The inventive method utilizes computer technology and network technology to realize, and its main feature has:
[0096] (1) The messages transmitted by the application of the transmission server in the system include real messages and decoy messages: in addition to transmitting encrypted real messages, the transmission messages also transmit pseudo-random sequences with the same cryptographic characteristics as the real messages , to lure some malicious attacks, the data format in the transmission system provides the function of identifying different types of messages;
[0097] (2) Random identity switching during transmission: In this system, the communication control server and multiple transmission servers form a cluster system to jointly complete data transmission tasks. Each system in the cluster automatically performs identity switching and port switching at the application layer or transport layer to protect the security of hosts and ports in the cluster;
[009...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com