Memory device, terminal apparatus and data repair system
A technology for storage devices and terminal equipment, applied in the field of repair systems, can solve problems such as hindering the expansion of new services, hindering IT (information technology development, user inconvenience, etc.)
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
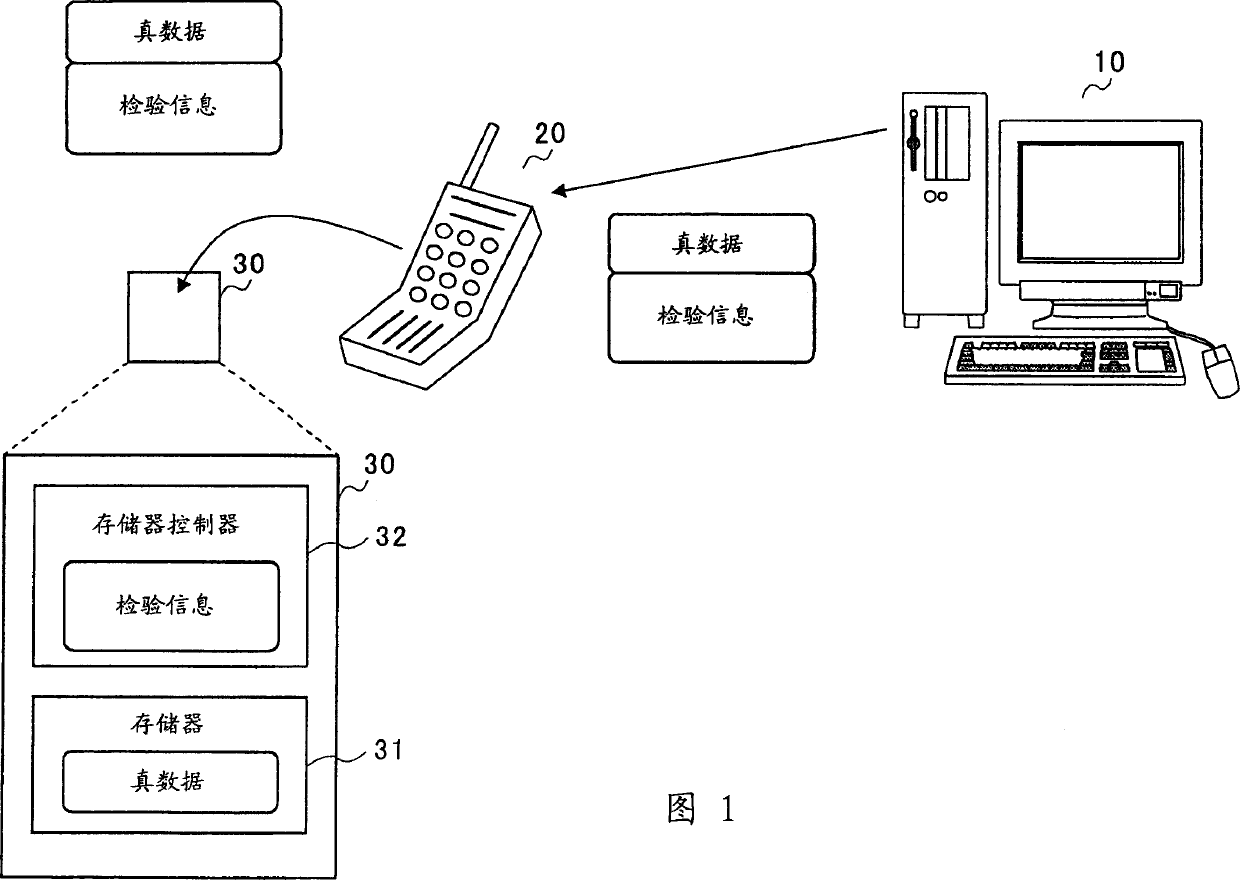
[0037] As shown in FIG. 1, the data restoration system according to the first embodiment of the present application includes a server 10 that manages data to be downloaded, a transmission path that protects sending / receiving with the server 10, and a terminal 20 that receives data to be downloaded. , and a storage device 30 inserted into the terminal 20 and storing downloaded data.
[0038] The data to be downloaded are immutable data such as program data, music data, and map data, etc., which do not allow the user to change the data. The server 10 separates the data of these items into several blocks, generates verification information (for example, hash value, check sum, CRC (cyclic redundancy check), signature, etc.) for the data in each block, and then retains and manages the authenticity data and inspection information. Then, upon receiving the data request from the terminal 20, the server 10 allows the download of the authentic data and verification information of the r...
no. 2 example
[0102] The second embodiment gives a description of a data restoration system that stores encrypted authentic data into a storage device.
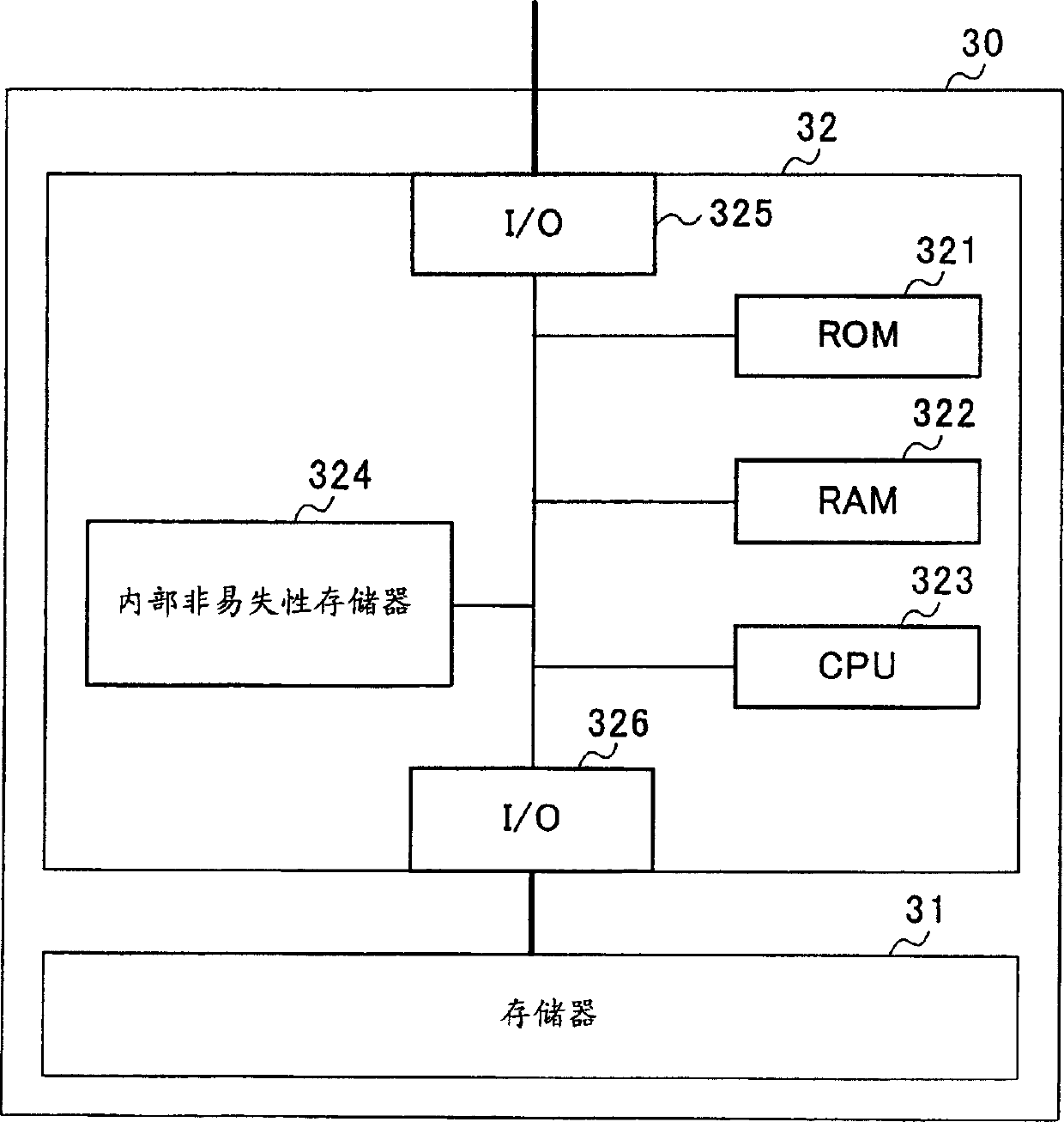
[0103] In this memory device, as shown in FIG. 13, the memory controller 32 further includes an encryption coprocessor 331 that decrypts encrypted data. Its configuration is the same as that of the first embodiment (FIG. 2) except as described above.
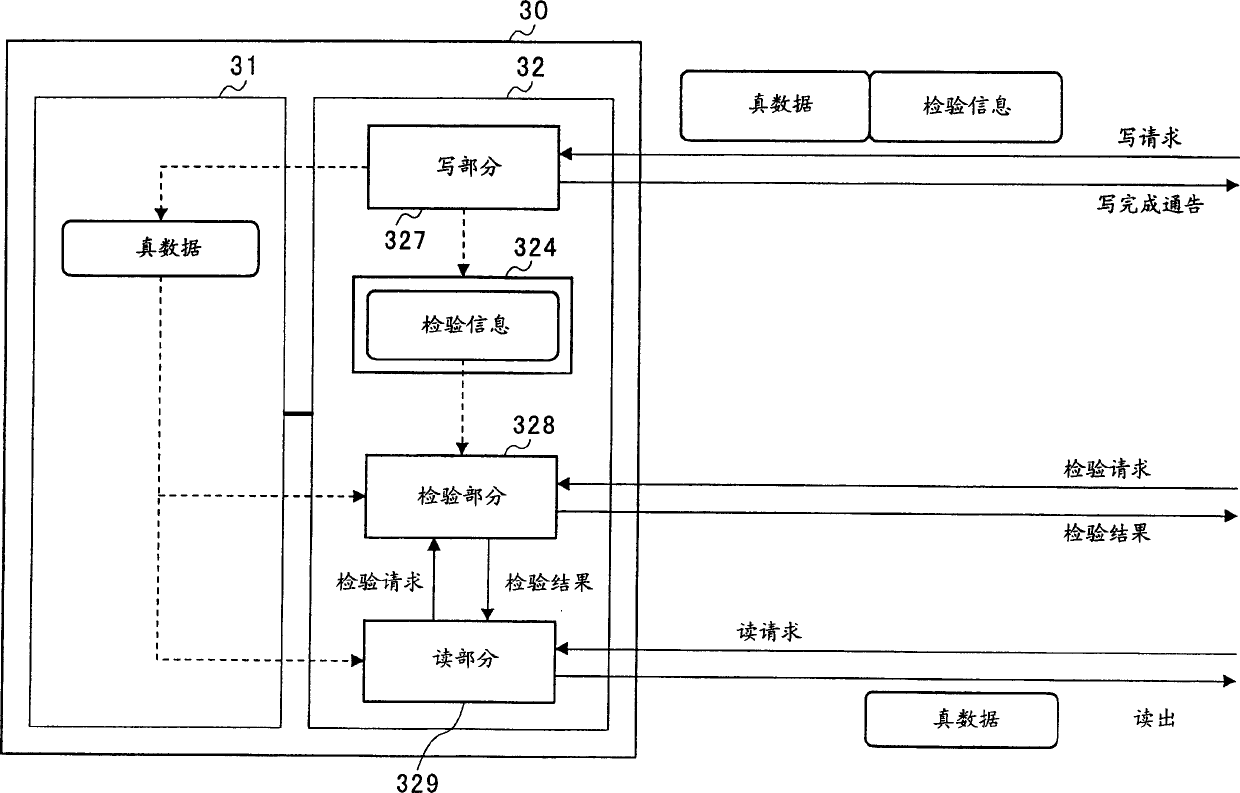
[0104] Data processing of this memory device 30 is shown in FIG. 14 . In addition to a write section 327, a check section 328, a read section 329, and an internal nonvolatile memory 324, the memory controller 32 includes a decryption section 332 that decrypts encrypted data. The function of the decryption part 332 is realized by the encryption coprocessor 331 .
[0105] After encrypting the file data, the server 10 in this system separates the encrypted data into several blocks, and generates verification information (for example, hash value, checksum, CRC, signature, etc.) for the data in...
no. 3 example
[0122] The third embodiment gives a description of a data restoration system equipped with countermeasures against falsification of verification information.
[0123] In this system, a server allows a terminal to download data separated into blocks and verification information with a signature attached, and when storing the verification information, the storage device verifies the signature.
[0124] Data processing of this memory device 30 is shown in FIG. 16 . In addition to the write section 327 and the internal nonvolatile memory 324, the memory controller 32 includes a signature verification section 333 that verifies the signature of the verification information. The function of this signature verification section 333 is realized by the CPU 323 by executing processing governed by programs.
[0125] The server 10 in this system retains and manages data separated into several blocks and their verification information, and, upon receiving a data request from the terminal 20...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com