Encrypting and de-encrypting method for personal hand-held communication system cell phone identification information
A technology for authentication information and handheld communication, applied in the field of PHS mobile phones, that is, personal handheld communication system mobile phones, can solve the problems of loss of PHS network operators, undiscovered technical solutions, and undiscovered problems, so as to prevent illegal parallel phenomena and prevent illegal The effect of obtaining and securing benefits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
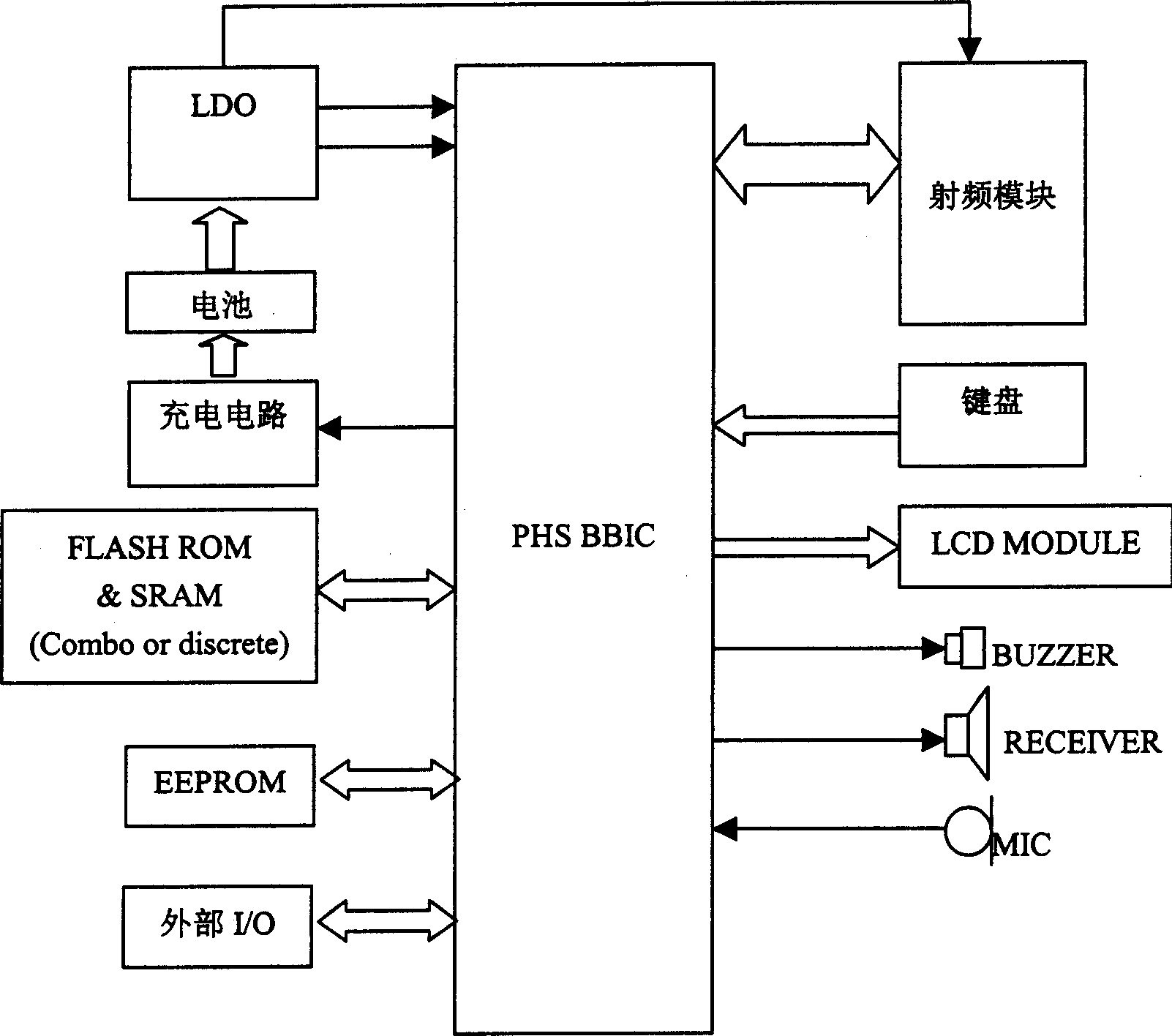
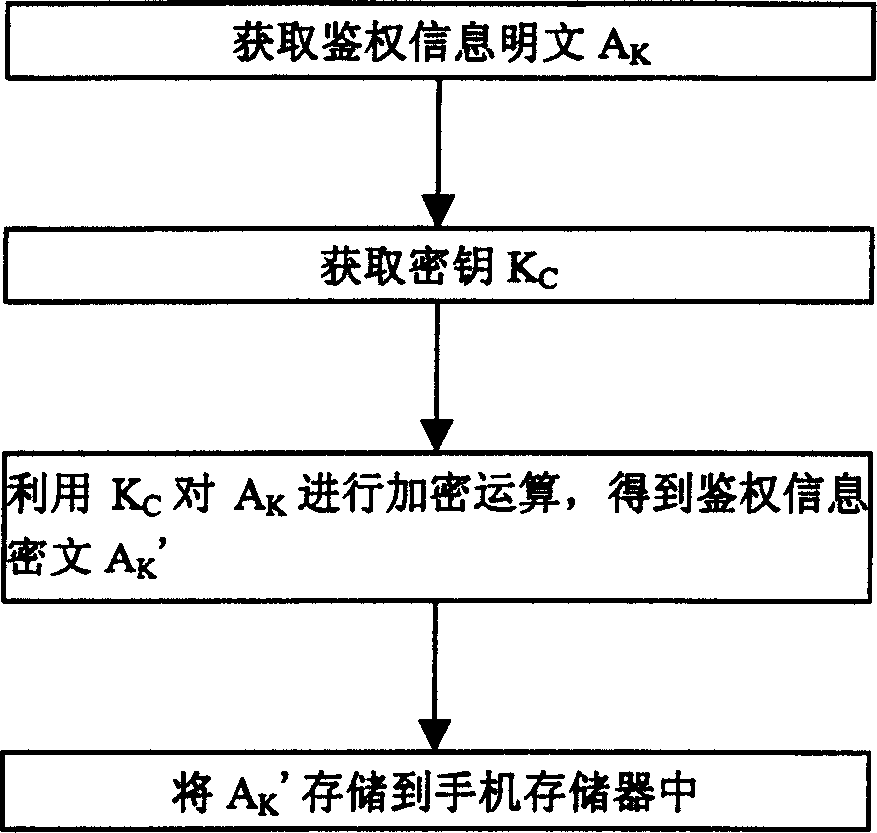
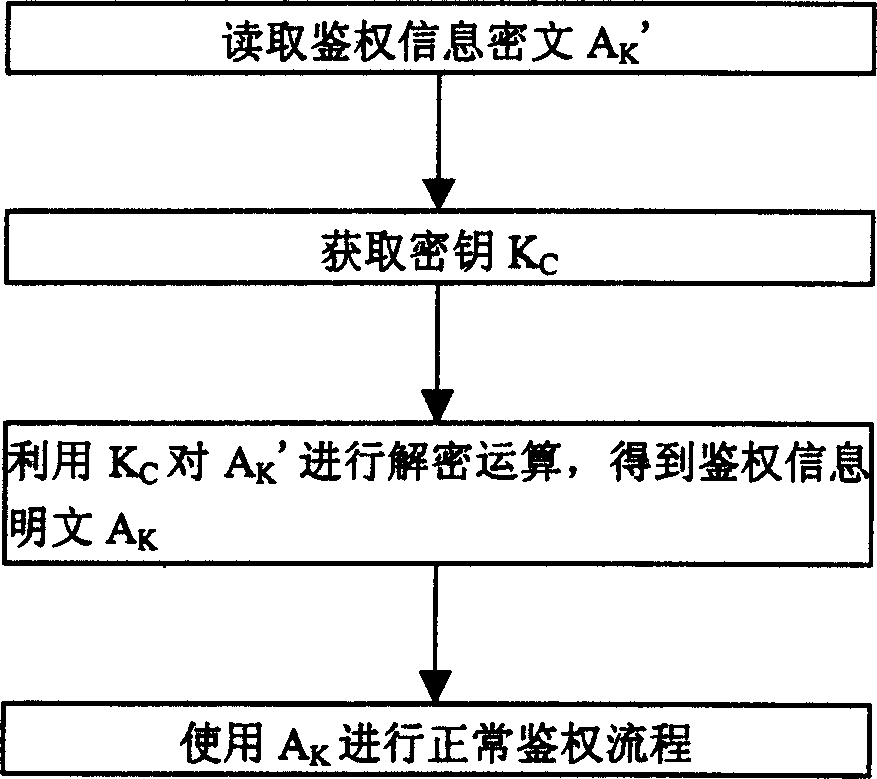
[0024] figure 1 It is a schematic diagram of the hardware structure of the existing PHS mobile phone. Such as figure 1 As shown, the hardware structure of PHS mobile phone is divided into baseband part and radio frequency part. The baseband circuit is composed of the baseband chip BBIC as the core. The PHS mobile phone program is generally stored in the external memory, that is, stored on FLASH or ROM. The adjustable parameters of the PHS mobile phone are generally stored on the EEPROM. In the prior art, the PHS mobile phone program is in the During the manufacturing process, it is directly stored in ROM (read-only memory) or Flash (flash memory). When the mobile phone is used, the mobile phone program is loaded into SRAM and DRAM to run. The very important authentication information on the PHS mobile phone exists in the EEPROM in the form ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com