Chaotic cipher production method under limited precision
A technology of chaotic ciphers and generation methods, applied in secure communication, digital transmission systems, secure communication devices, etc., can solve problems such as characteristic degradation, achieve the effect of reducing correlation, reducing the degree of cross-correlation, and increasing linear complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0020] The chaotic map in this method is a simple one-dimensional logistic iterative
[0021] x i + 1 = 1 - 2 x i 2 ; x i ⋐ ( - 1,1 ) - - - ( 1 )
[0022] calculating x i + 1 = 1 - 2 x i 2 , because the input value for the next iteration is still 64 bits, but x i 2 is 128 bits, so x must be i 2 For rounding, this method adopts the tail removal method. (Explanation of the rounding method).
[0023]...
example 2
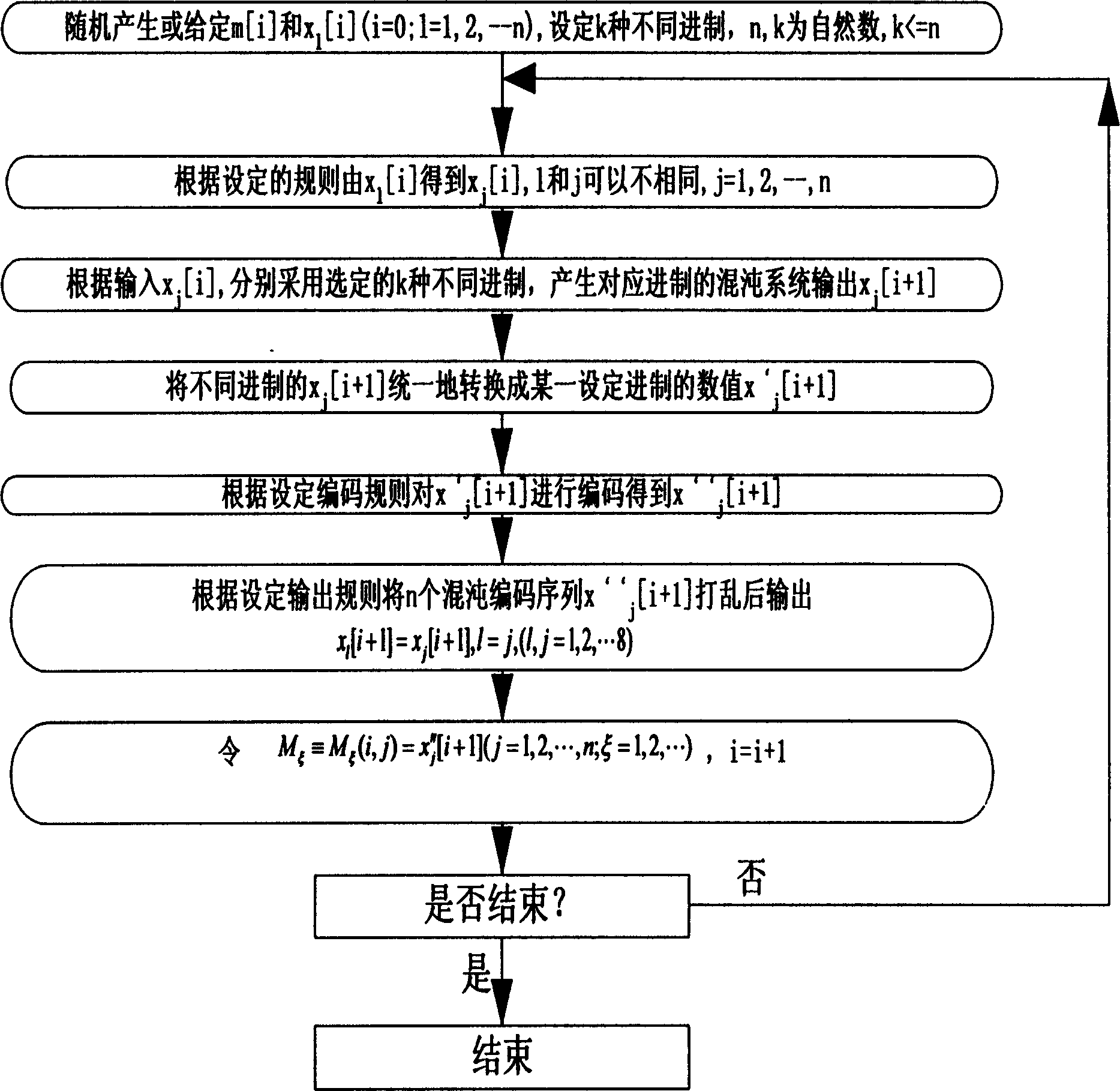
[0047] The following method can also be used to increase the period and linear complexity of the digital chaotic sequence: use the method of cyclic shift to exchange the iterative values of different bases, and then perform iterative calculation. Its algorithm is described as follows:
[0048] (1) Randomly generate the initial value m of the output control rule 0 and the initial value of the chaotic system
[0049] x l [0], (1=1, 2, ... 8), select 8 bases 12, 13, 14, 15, 28, 29, 30 and 31;
[0050] (2)x j [i]=x l [i], j=l+1, (l=1,2,...7), when l=8, j=1;
[0051] (3) by x j [i] According to the chaotic map x i + 1 = 1 - 2 x i 2 Use different base calculations to generate chaotic map output x j [i+1](j=1, 2, ... 8);
[0052] (4) Put x in different bases j [i+1] converted to...
example 3
[0059] Since the existing microprocessors and hardware arithmetic units are based on binary calculations, FPGA technology must be used to implement M-ary arithmetic operations when implementing M-ary digital chaotic mapping in Example 1. The design of the multiplier requires Lots of hardware resources. However, the existing binary-based hardware multipliers are quite mature in design method and quite optimized in algorithm. If the existing binary-based hardware multiplier and M-ary operation can be combined, then hardware resources can be reduced while reducing design difficulty.
[0060] Therefore, binary calculations can be used in the calculation of the chaotic map, and then the obtained result x k+1 Convert to M-ary number x' k+1 , and then the M-ary number x′ k+1 convert to binary x" k+1 .
[0061] Because the carry rule of the N-ary system is different from that of binary, the rounding precision and binary are also different when performing rounding processing, so u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com