Integration of high-assurance features into an application through application factoring
A technology of applications, members, applied in the field of computing, which can solve problems such as how applications can use two environments.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] review
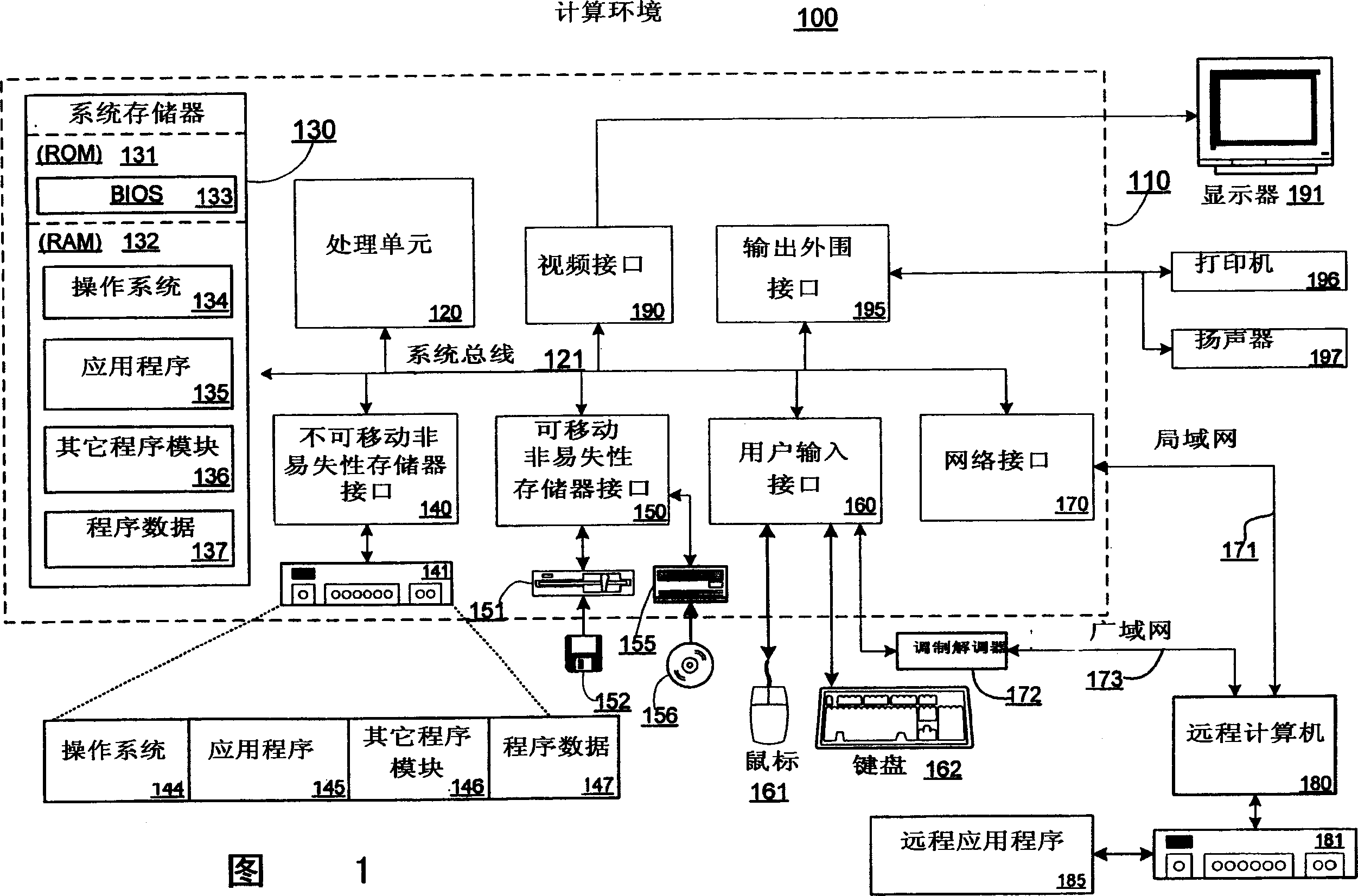
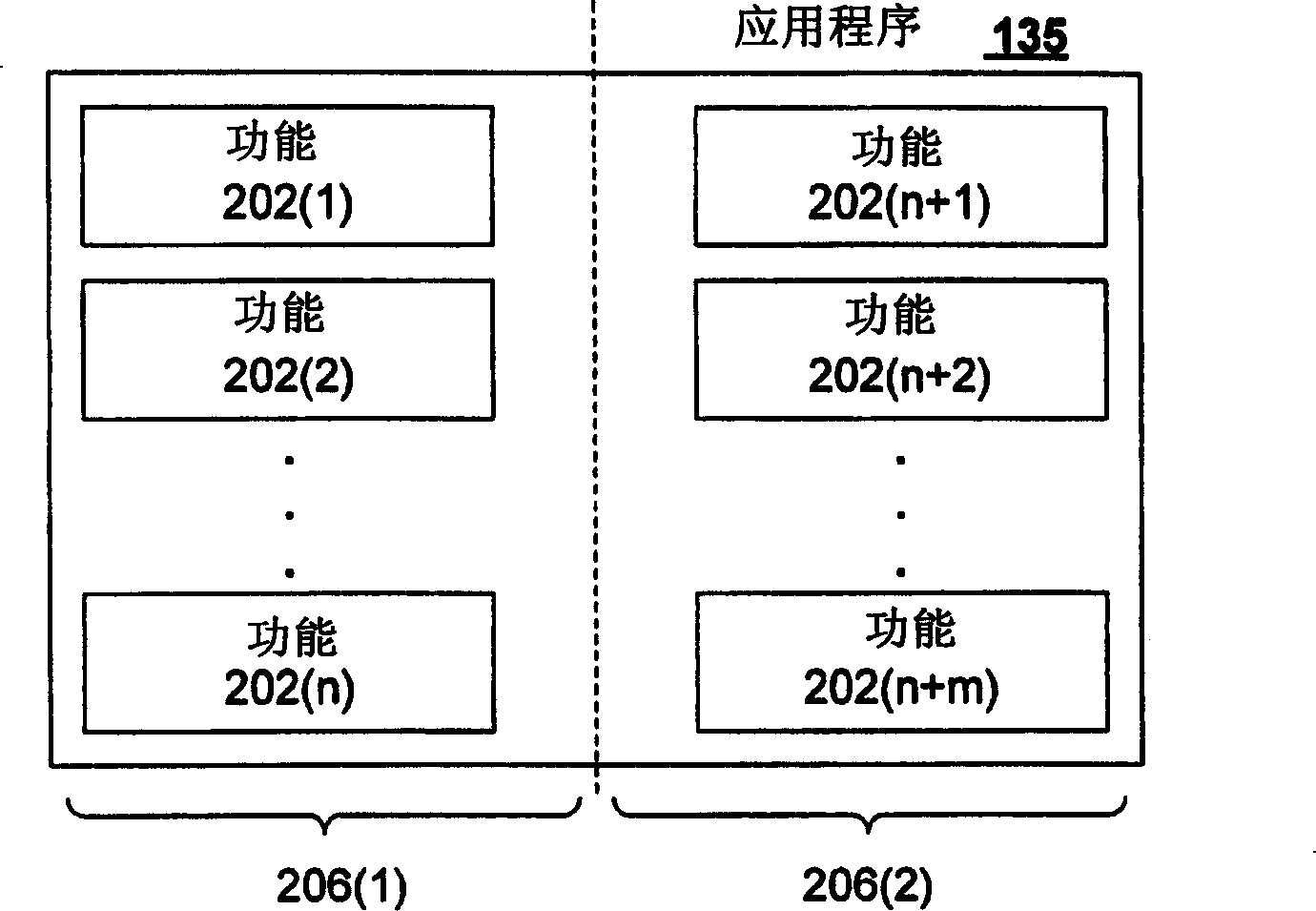
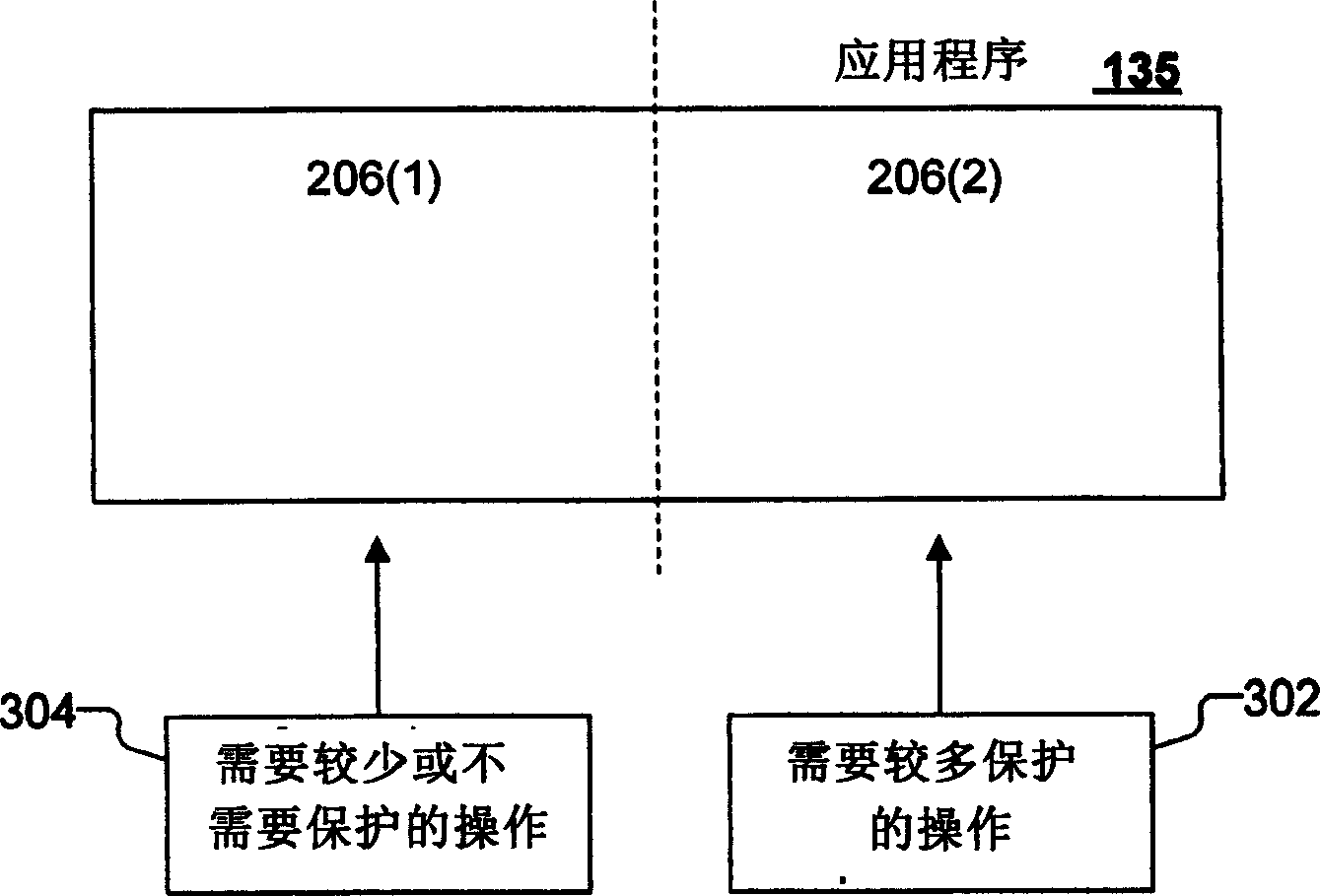
[0019] The present invention provides a mechanism that allows an application to be divided or "decomposed" into secure and non-secure components, and to allow these components to work together to provide an integrated user experience with respect to the application. For example, a word processing program can be divided into a non-secure component that performs most of the layout, editing, printing, spell checking, grammar checking, etc. functions associated with a word processor, and a non-secure component that enables the display and Edited security components. Non-secure components can run in common, open environments, such as typical commercial operating systems. A secure component may run in a high-assurance environment that allows certain types of software to run with a high assurance that the software will behave correctly. The present invention provides various features in relation to this situation. First, the present invention provides a user expe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com