Authentication processing method for broadband network
A broadband network and network terminal technology, applied in the field of network communication, can solve the problems of forced offline of network terminals, short-term abnormalities, and accurate detection of network terminals, etc., to reduce the potential cost of authentication processing, disperse processing load, reduce Effects of Potential Threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
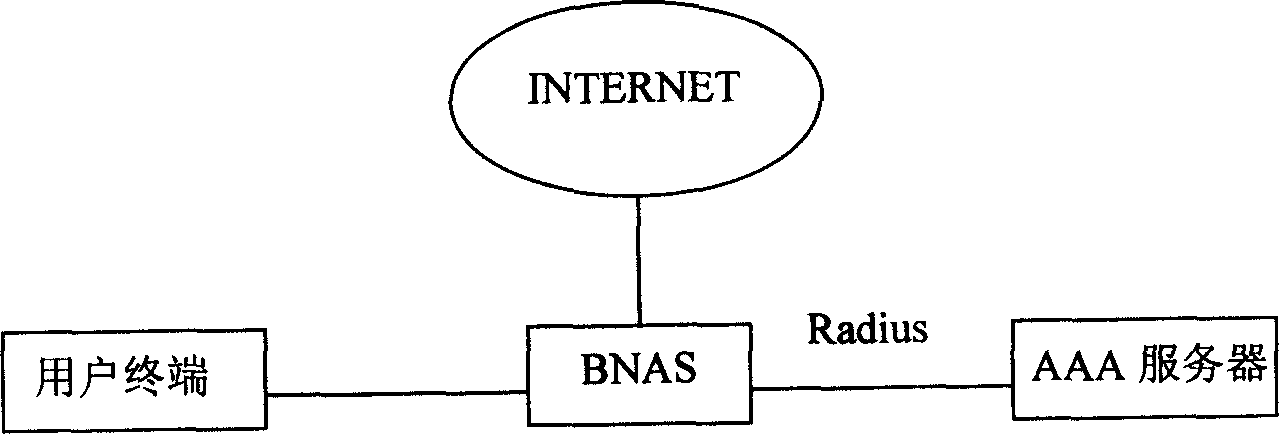
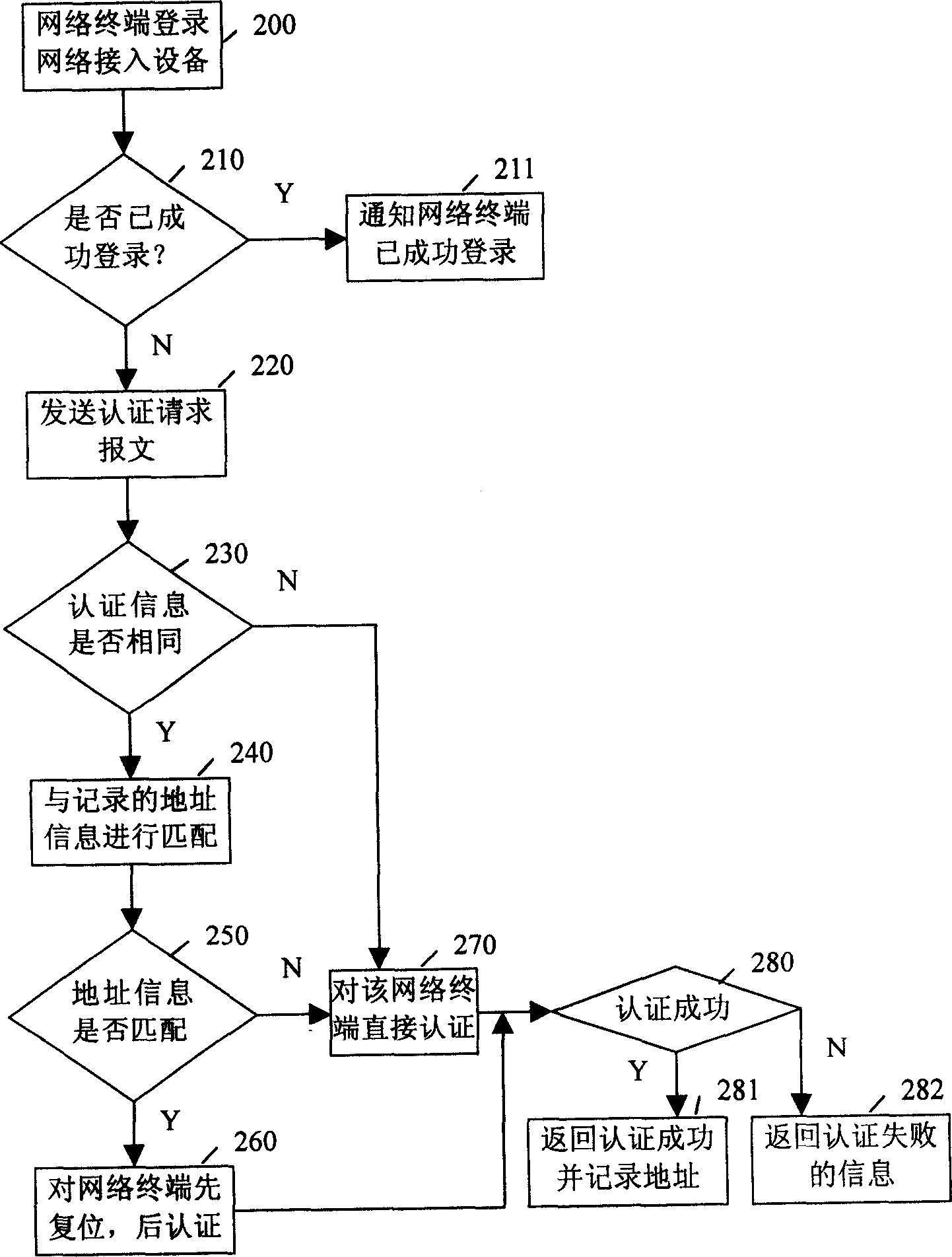
[0051] Since the network terminal is hacked, the network terminal will not be properly authenticated, so that the network terminal cannot be online, so the present invention increases the detection when authenticating the network terminal. Whether the network terminal is hailed, through which the detection process is determined, it is determined that the network terminal is hacked, and immediately resets it, the hanger is released, and then the network terminal is authenticated. Therefore, whether it is due to the authentication server, the network access device has caused the network terminal to be hanged, or because the network between the authentication server and the network access device causes the network terminal to be hanged, when the network terminal will apply for authentication again It can be detected in time, not affecting the authentication server for normal authentication, ensuring that the network terminal is always online. The hanger detection of the present inven...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com