Access point and method for controlling access point
A technology for controlling access points and communication terminals. It is applied in user identity/authority verification, data exchange through path configuration, security devices, etc., and can solve problems such as increasing the cost of wireless access points and heavy burdens on client terminals.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0040] According to a first embodiment of the present invention, an access point with a filtering function is used in a network including a local area network and a backbone network. In the local area network, IEEE 802.11 wireless LAN and Bluetooth (Bluetooth) network are used as communication media of the wireless local area network.
[0041] The operation of the access point is explained below.
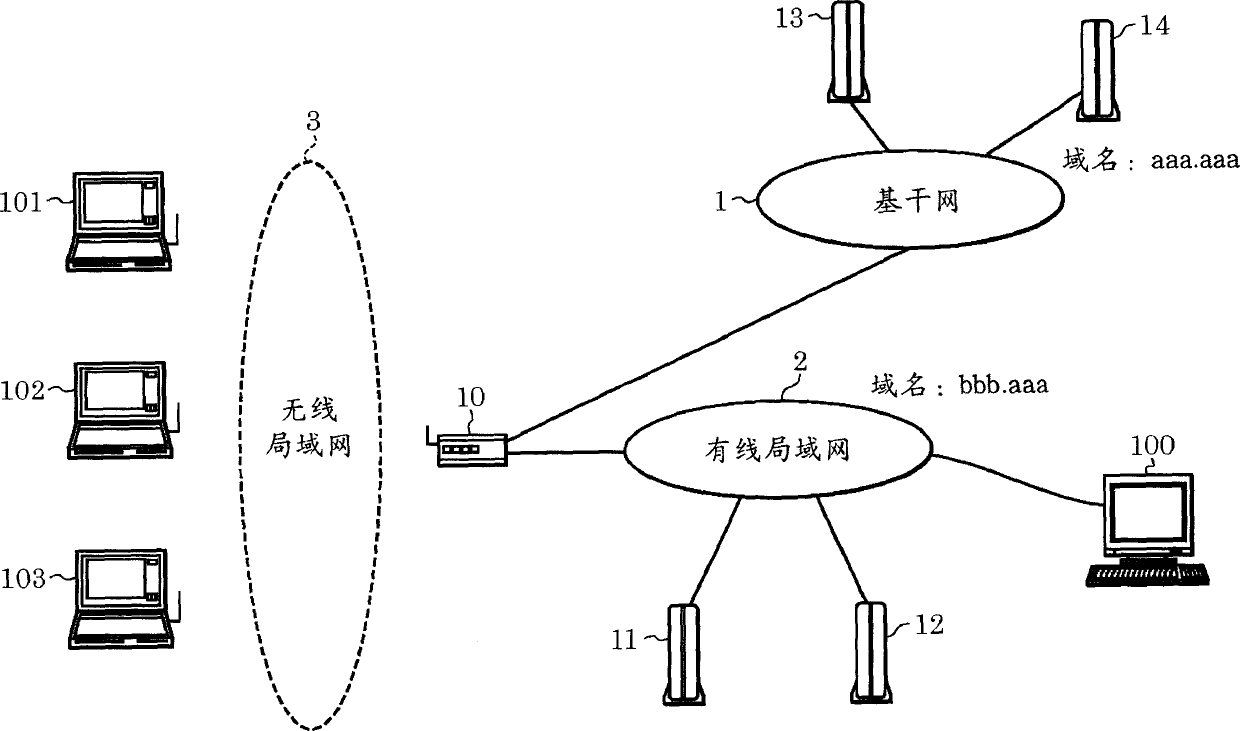
[0042] FIG. 1 is a schematic diagram of a network configuration according to this embodiment. As shown in Figure 1, the network configuration includes: a backbone network 1, a wired LAN 2, a wireless LAN 3, a wireless access point 10 with a filtering function according to this embodiment, a LAN data server 11, and a proxy (proxy) used by the LAN. Functional remote authentication dial-in user service (Remote Authentication Dial-In User Server, RADIUS) server 12, backbone network data server 13, backbone network RADIUS server 14, wired client terminal 100 and wireless client terminal...
no. 2 example
[0061] Fig. 11 shows a schematic diagram of a network configuration according to the second embodiment.
[0062] As shown in Figure 11, the network configuration includes: backbone network 1101, wired LAN 1102, wireless LAN 1103, wireless access point 1110 with filtering function according to this embodiment, LAN data server 1111, RADIUS server with proxy function on the backbone network 1114 (i.e., such as an authentication server of an xDSL provider), backbone network data server 1113, backbone network RADIUS servers 1115 to 111n (i.e., such as user authentication servers of an Internet Service Provider (ISP), wired client terminal 11100, and wireless Client Terminal 11101 to Wireless Client Terminal 11103.
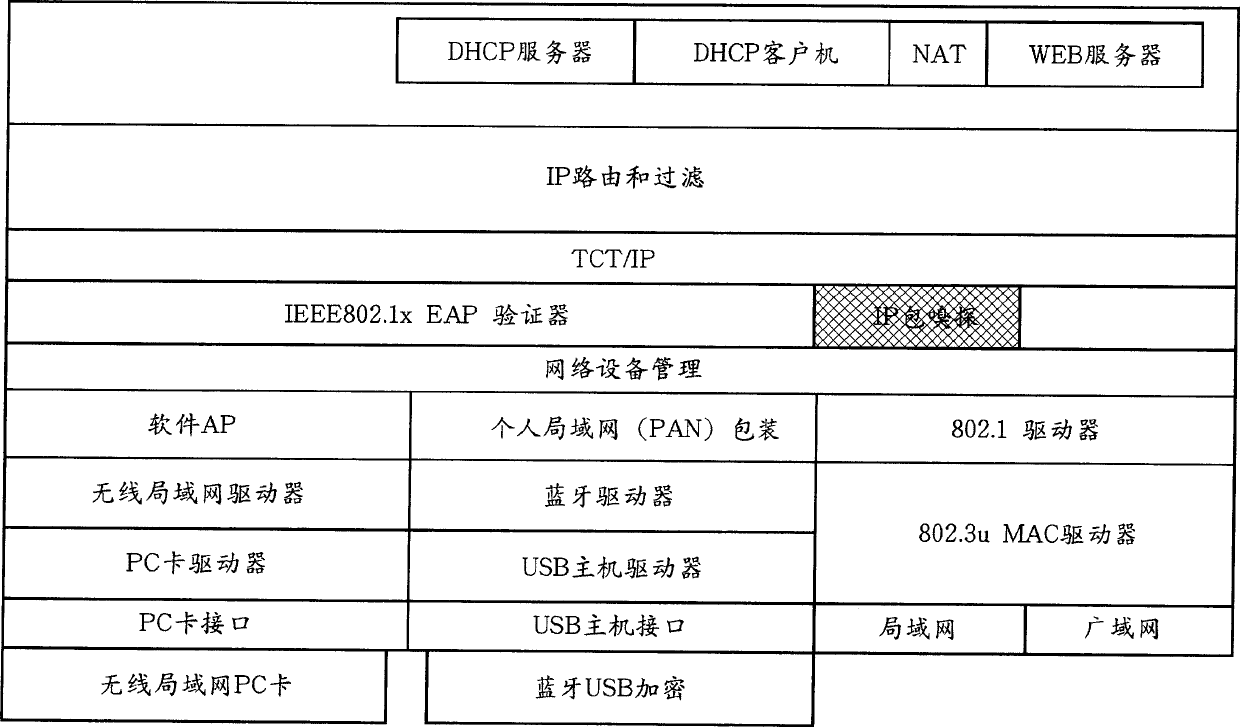
[0063] FIG. 12 is a schematic diagram showing functional layers of a wireless access point 1110 with a filtering function according to this embodiment. In order to realize the function according to this embodiment, the IP packet sniffing function block monitors the aut...
no. 3 example
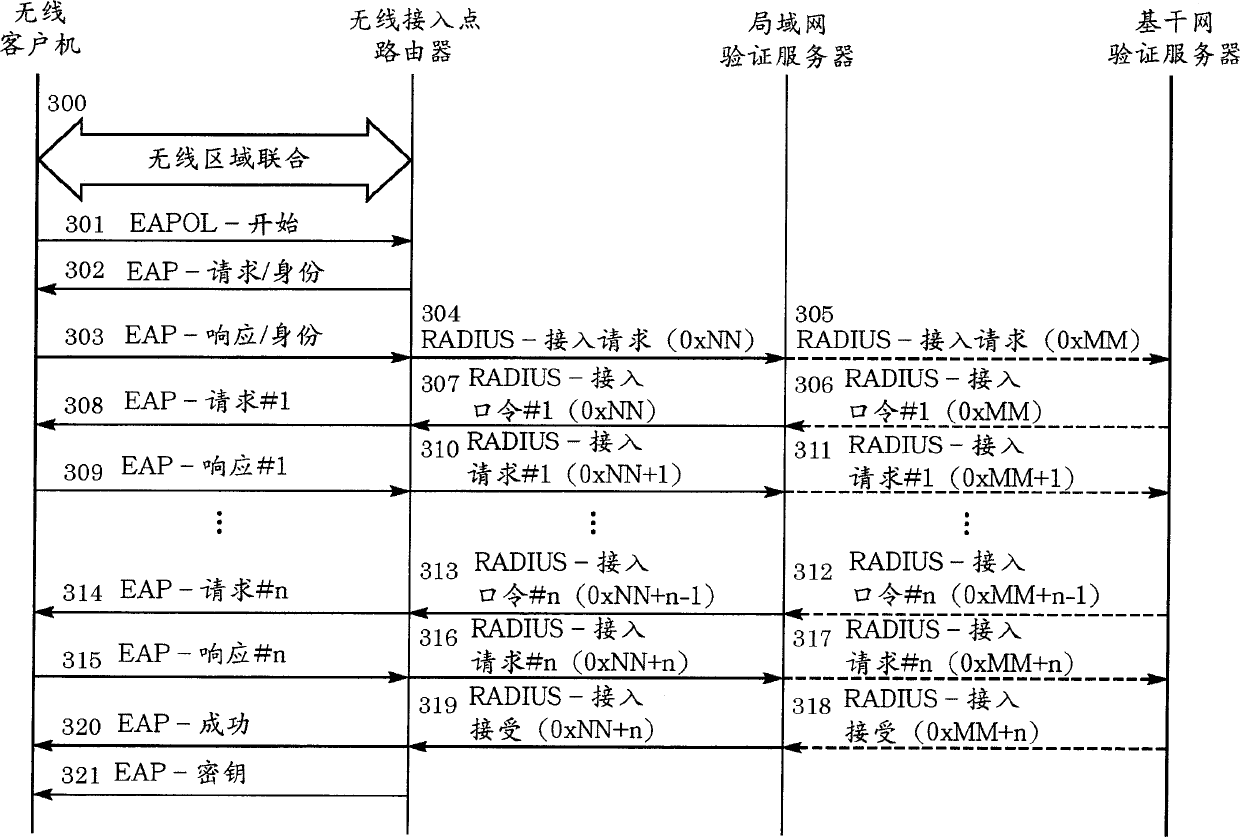
[0068] Fig. 15 shows a schematic diagram of a network configuration according to the third embodiment. As shown in Figure 15, the network configuration includes: backbone network 1501, wired local area network 1502, wireless local area network-1 1503, wireless local area network-2 1504, wireless access point 1510 with filtering function according to this embodiment, local area network data server 1511, Backbone RADIUS Server-1 1514 (i.e., such as an authentication server of an xDSL provider), Backbone Data Server 1513, Backbone RADIUS Server-2 1515 to RADIUS Server-N 151n (i.e., such as an ISP's User Authentication Server), Wireless Access Point 1520 with IEEE 802.1x EAP function, Wired Client Terminal 15100, Wireless Client Terminal-A 15101, Wireless Client Terminal-B 15102, Wireless Client Terminal-C 15103, Wireless Client Terminal-α15201, and Wireless Client Terminal-β15202.
[0069] In this embodiment, the functional layer of the wireless access point with filtering funct...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com