Method for carrying out private security data communication base on decimal communication numbers
A communication number and security data technology, applied in the field of communication, can solve problems such as difficult communication, difficulty in remembering IP addresses for both parties in communication, message spoofing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] 1. Communication terminal creation:
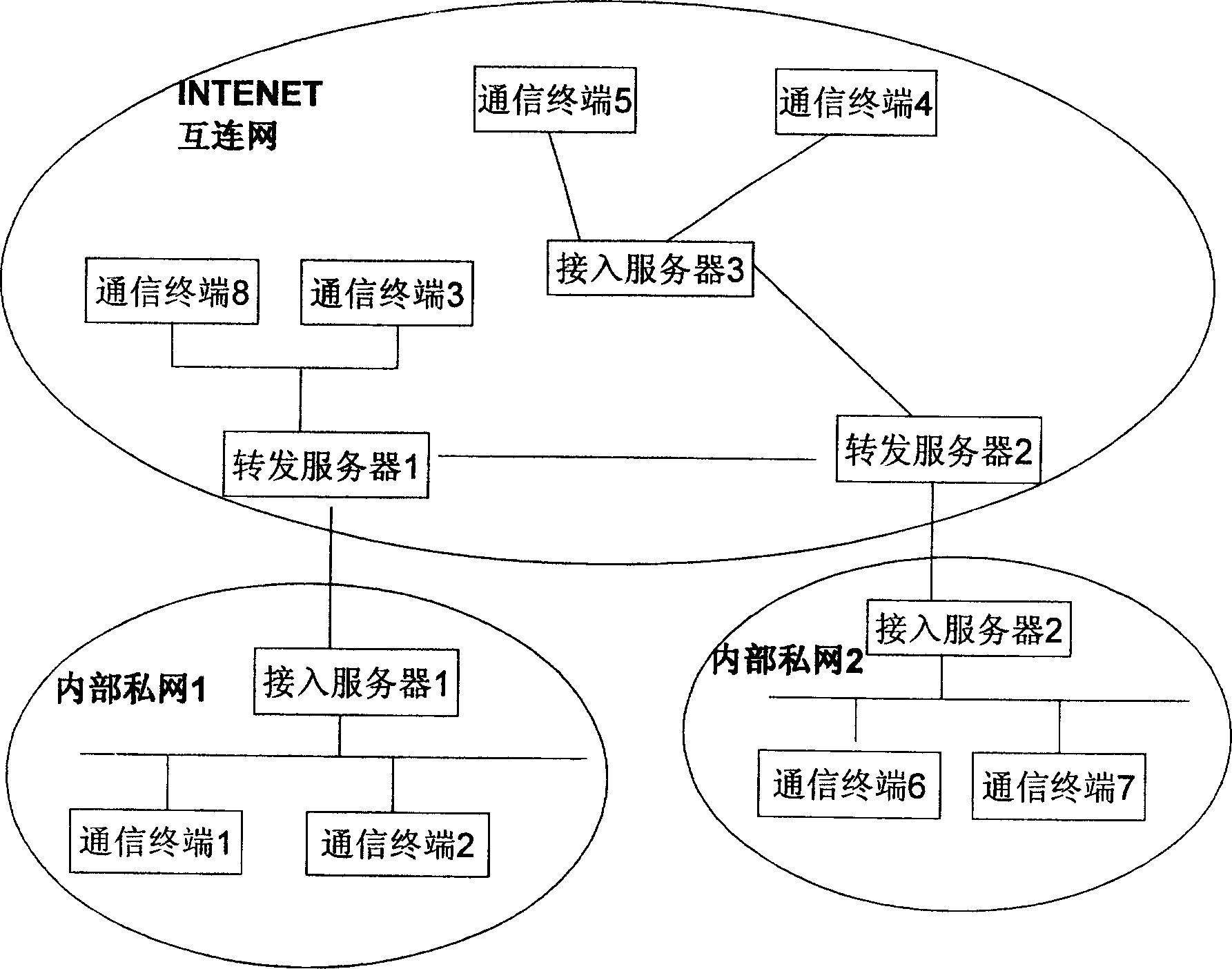
[0057] Such as figure 1 As shown, the access server (1) and the access server (2) are located inside the private network, respectively connected to the forwarding server (3) and the forwarding server (4) in the public network; the access server (5) is located in the public network (INTERNET network), the forwarding server (4) is connected; the forwarding server (3) is an access server at the same time, and the communication terminal (8) and the communication terminal (6) are directly connected on the forwarding server (3). The length of the set network number section is 4 bits, the network number section of the forwarding server (1) is 1111; the network number section of the forwarding server (2) is 2111.
[0058] The access server (1) is placed in the internal private network 1, and communicates with the forwarding server (1) in the Internet through a proxy. The length of the subnet number segment of the access server (1) is three...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com