Dependence management system structure based on confidence reckon
A technology of trust management and architecture, applied in transmission systems, electrical components, etc., can solve problems that cannot satisfy trust management, and achieve the effect of ensuring interoperability and high-credibility trust management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
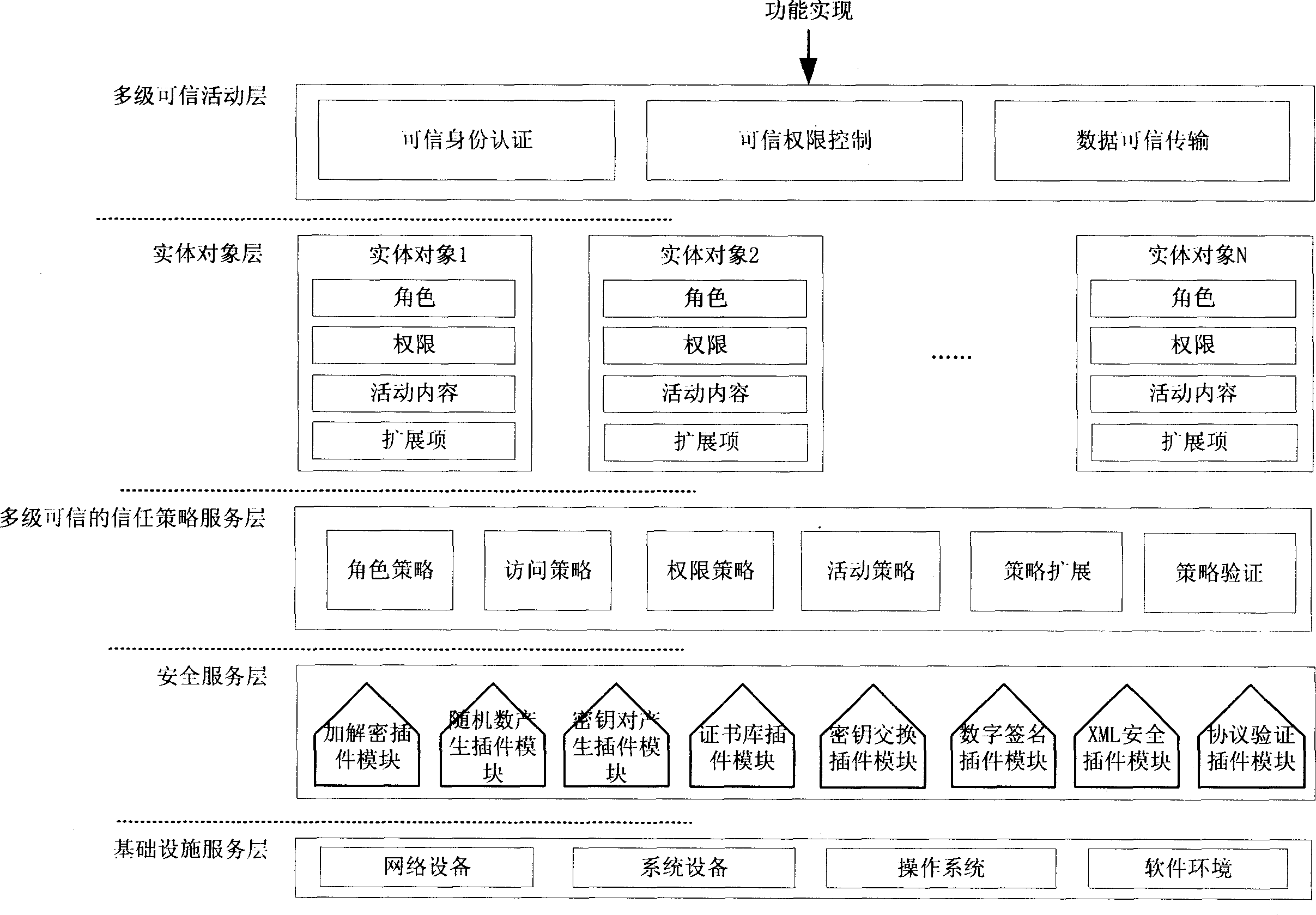
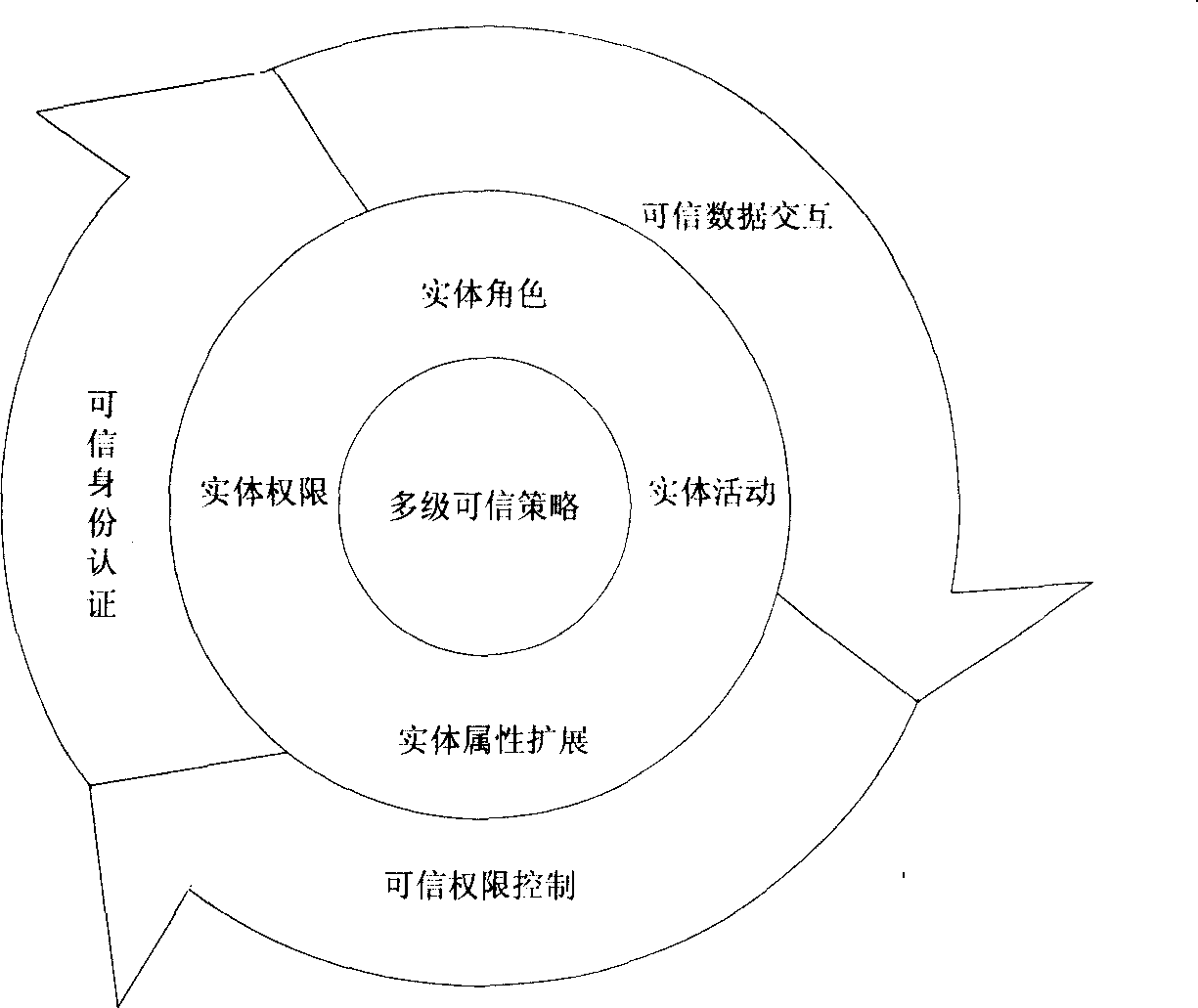
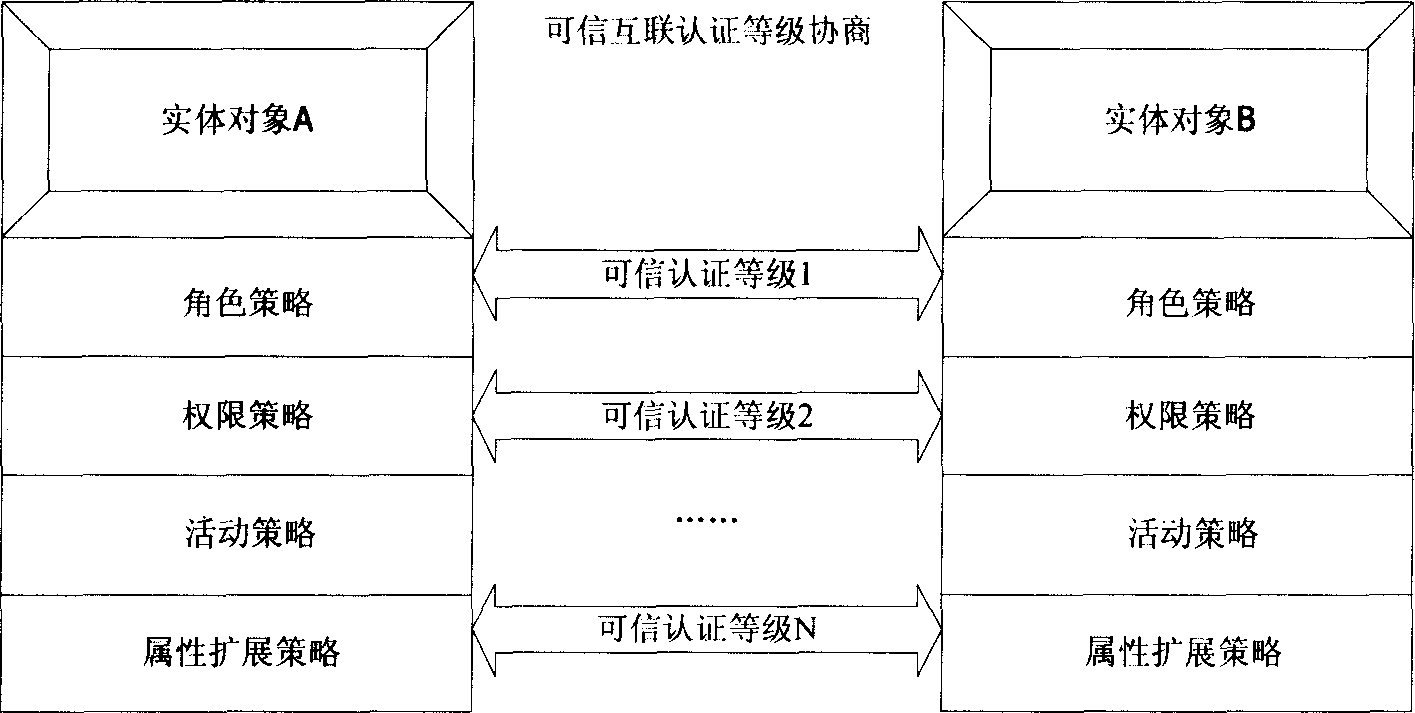
[0018] Such as figure 1 As shown, the architecture has five layers from bottom to top, and the specific description is as follows:
[0019] 1. Infrastructure service layer:
[0020] The infrastructure layer is the lowest layer of the system structure, which is connected with the security service function layer through the software interface, and is the software and hardware environment on which the system structure depends. Such as figure 1 shown, including network equipment, system equipment, operating system, and software environment.
[0021] 2. Security service layer:
[0022] The security service layer is connected downwards with the infrastructure service layer through software and hardware interfaces to realize basic security service functions. This layer is upwardly connected to the multi-level trusted trust policy service layer, providing security service plug-ins for the realization of the above three-layer functions, such as figure 1 As shown, such as: encrypti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com