AES encrypted circuit structure for data stream executed in desequencing
A circuit structure, encryption circuit technology, applied in the direction of encryption device with shift register/memory, etc., can solve the problem of not being accepted as
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0164] We have realized a data stream AES encryption chip (THDFAES04) according to the present invention, and carried out the casting experiment. The following is an example to introduce the specific implementation method:
[0165] 1. Working method
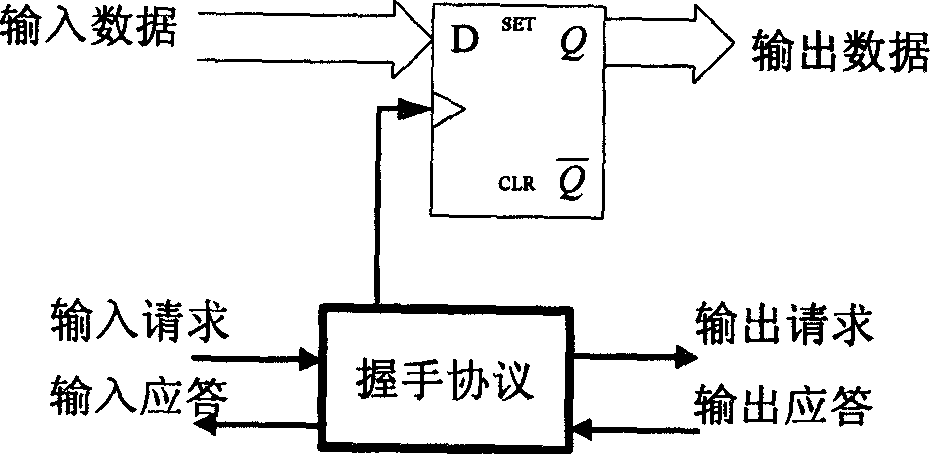
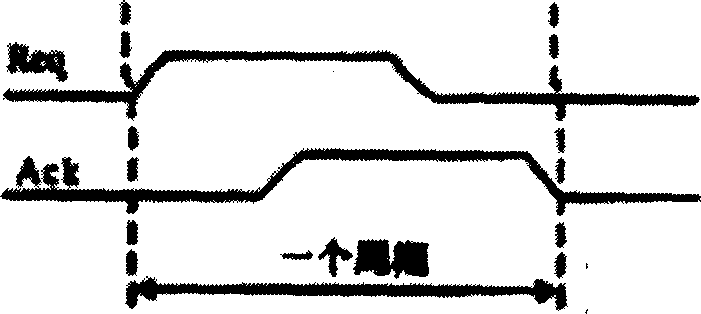
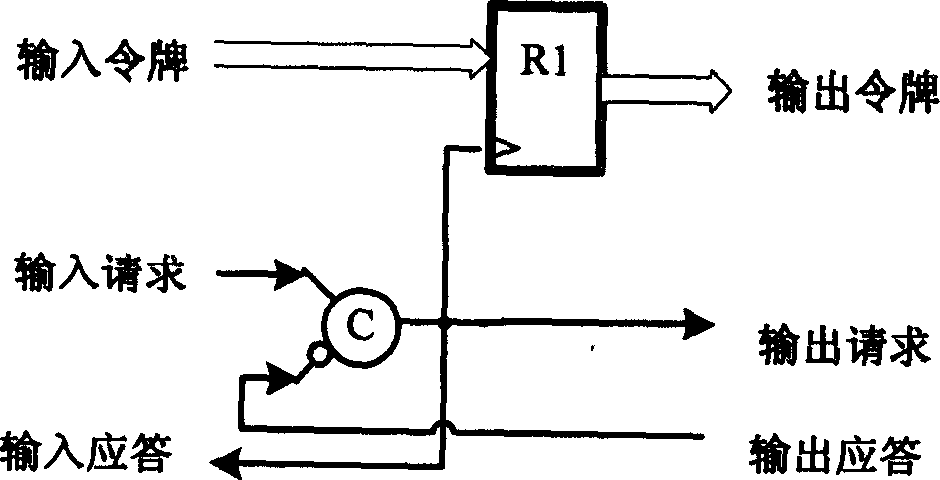
[0166] The chip processes a group at a time, and before starting to encrypt, the key column number (NK) and the initial key are sent to the internal setting register and the initial key register of the chip respectively through the data input bus. Then the plaintext packet is sent to the chip. The start signal triggers the chip to start working. The final operation result is first temporarily stored in the output register. When the output register is full—that is, after the entire packet is generated, the end signal (OK) becomes high, and the result data can be read from the data output bus. The data in the initial key register is rewritten into the internal key scratchpad every time a new packet is started.
[0167] 2. Circu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com