Network security system and method
a network security and network technology, applied in the field of network communication, can solve the problems of cloning techniques, affecting the security of network providers, and affecting the ability of authorized card users to conceal cloned devices from the server, so as to reduce the risk of successful hacking and not easily hacked or duplicated
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
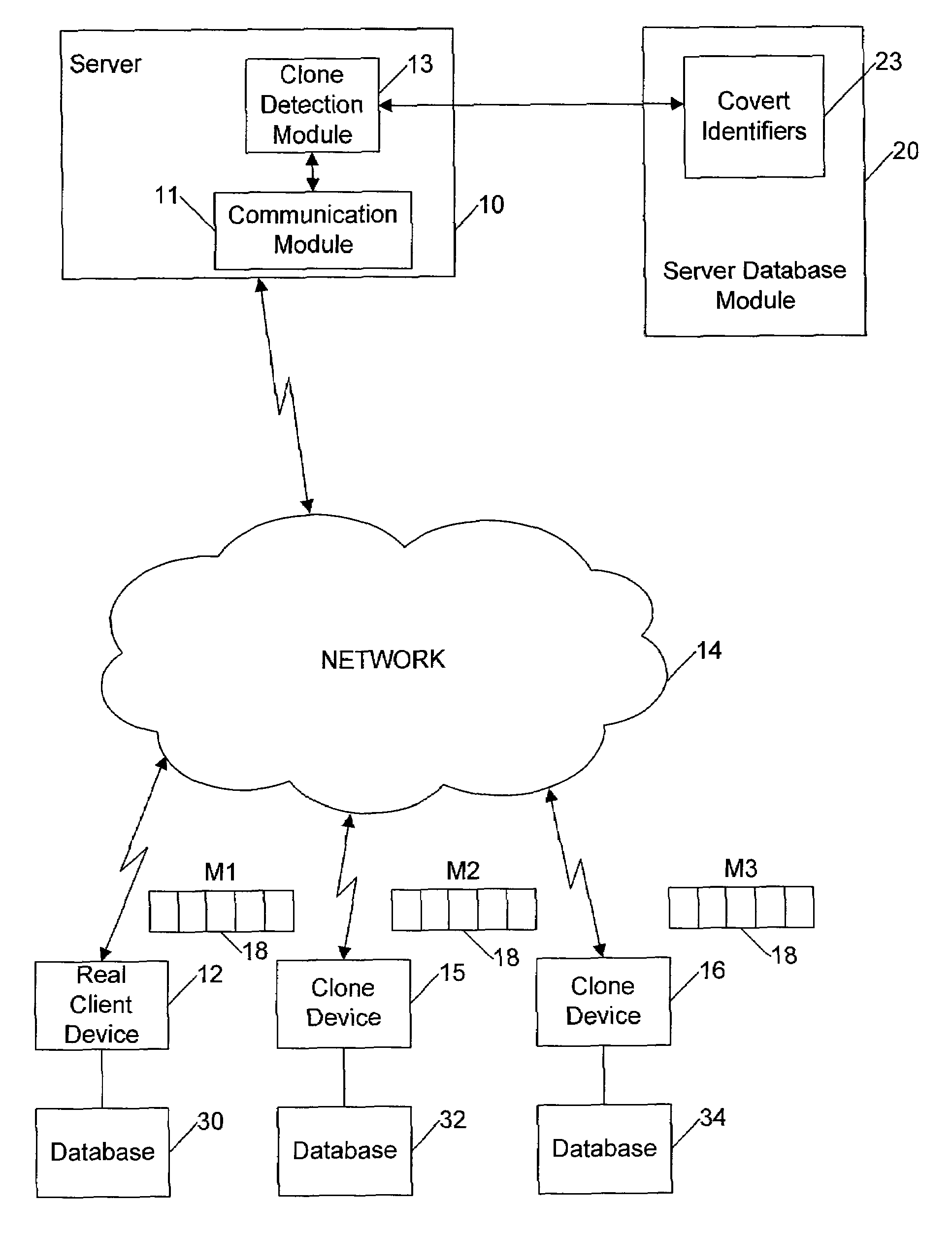
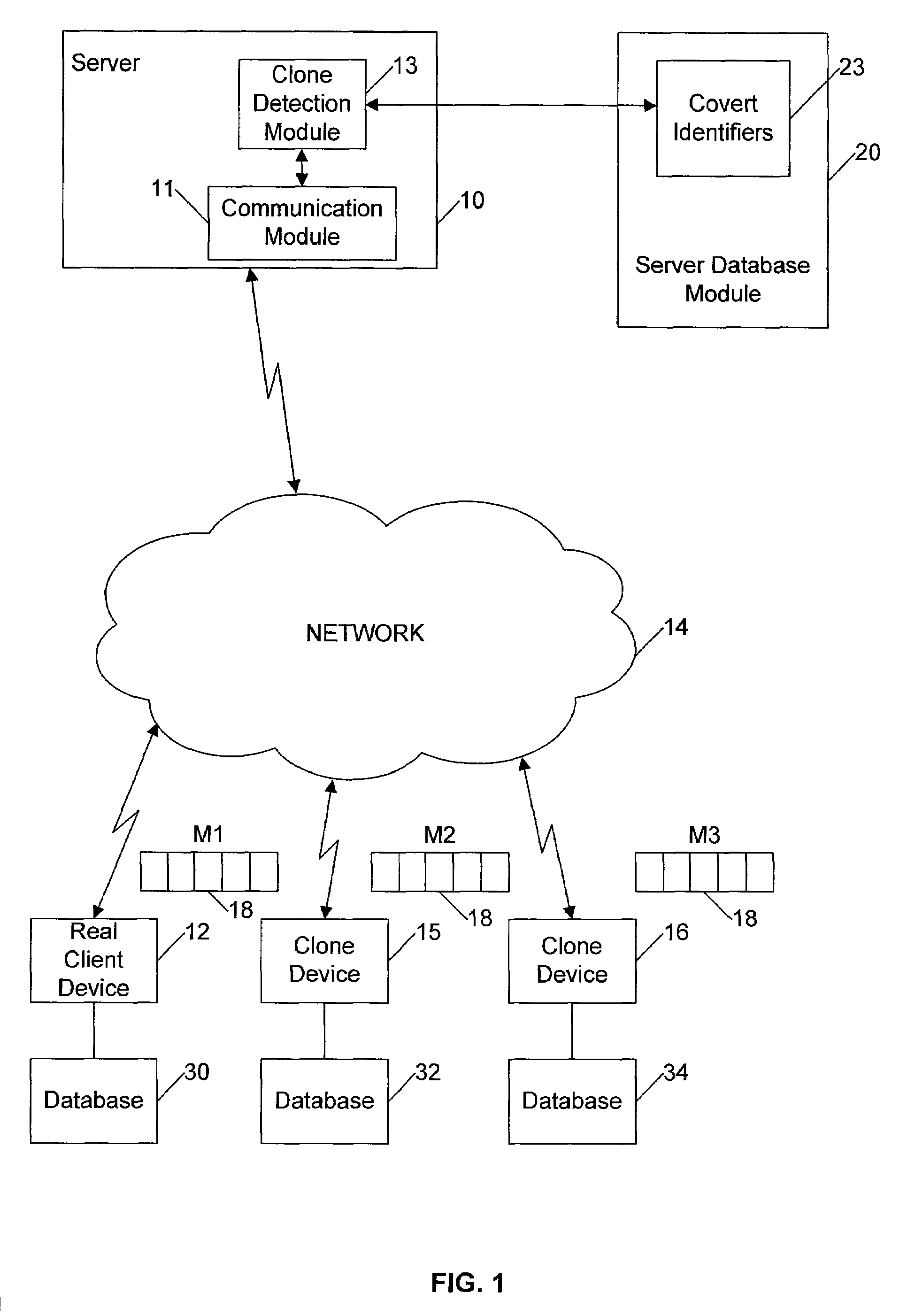
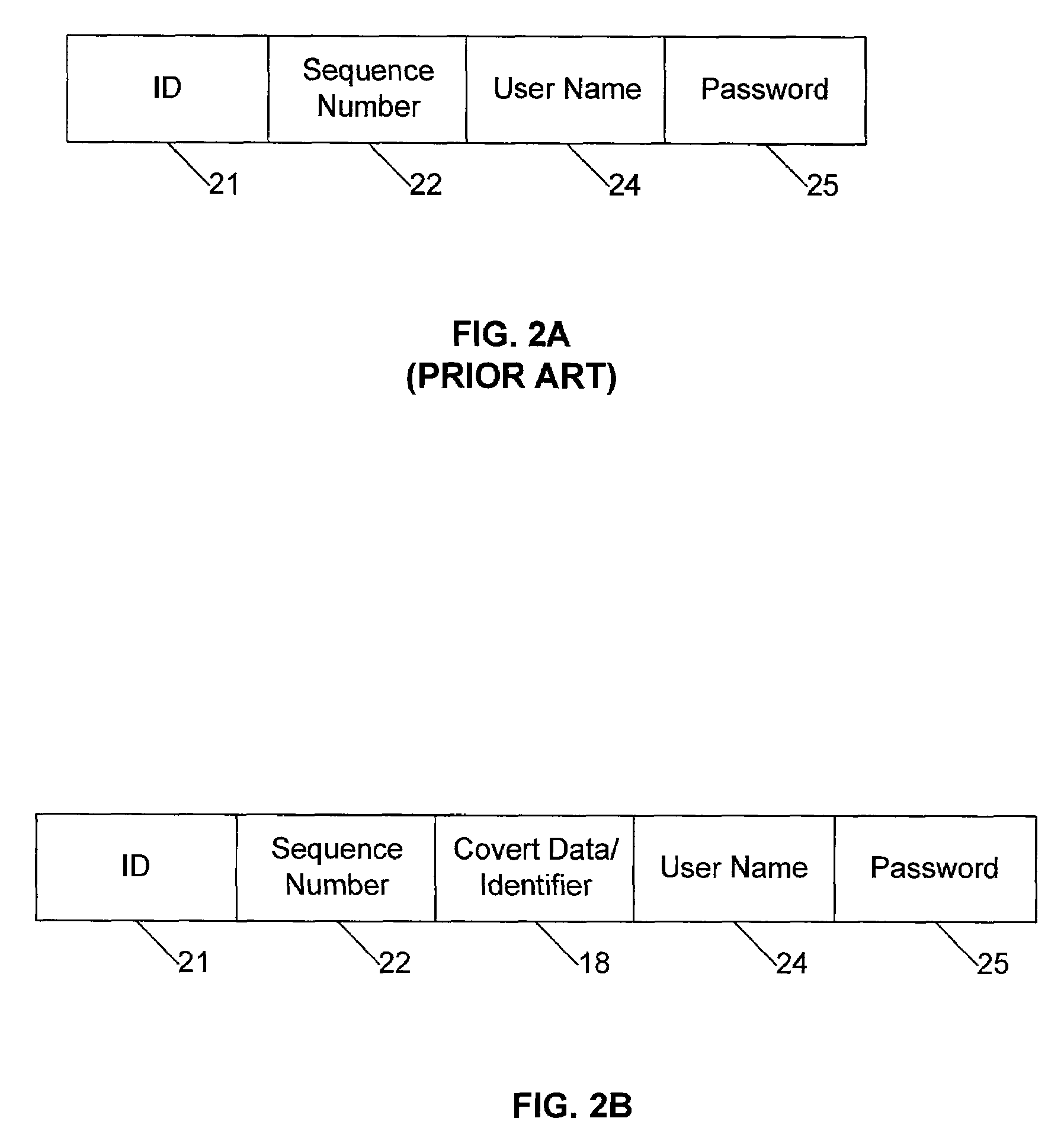
[0034]Certain embodiments as disclosed herein provide for detection of more than one client device using identical credentials. For example, one method and system as disclosed herein allows for detection of potential clone devices using a covert identifier based on values of operational events specific to a client device which is added into the normal messaging between a client device and a server.
[0035]After reading this description it will become apparent to one skilled in the art how to implement the invention in various alternative embodiments and alternative applications. However, although various embodiments of the present invention are described herein, it is understood that these embodiments are presented by way of example only, and not limitation. As such, this detailed description of various alternative embodiments should not be construed to limit the scope or breadth of the present invention as set forth in the appended claims.
[0036]In the following description, a client ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com