Risk assessment for network access control through data analytics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
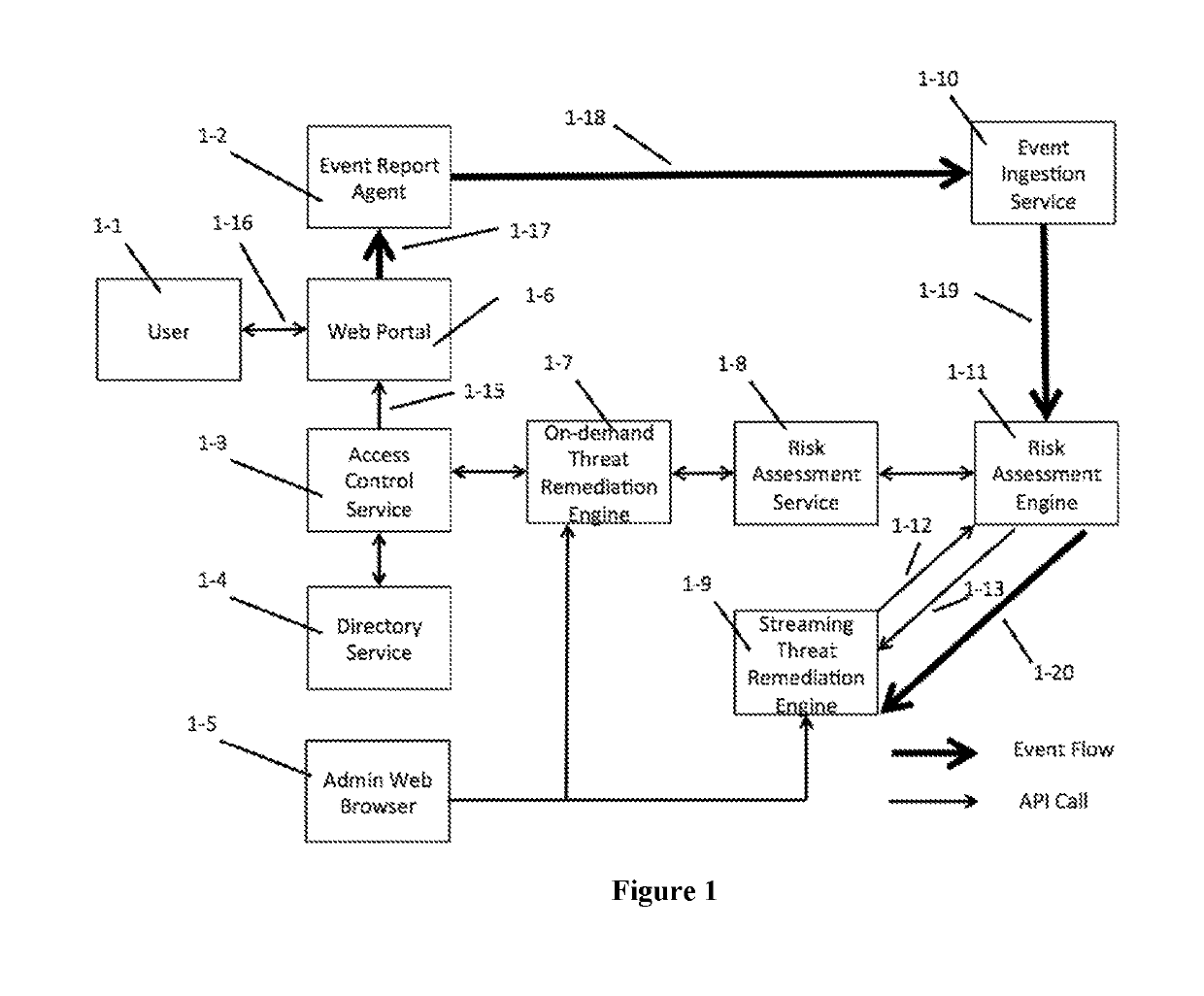
[0014]FIG. 1 shows the components of an embodiment of the invention as they exist in a web portal within a computer network, or other computing environment that requires authentication and authorization to use the environment's resources.
[0015]An event reporting agent 1-2 within the environment detects entity behavior and reports it to an embodiment of the invention as events, each event with a set of attributes and can include:
[0016]Login events, which can include parameters such as the IP address of the device used, the type of device used, physical location, number of login attempts, date and time, and more.
[0017]Application access events, which can specify what application is used, application type, date and time of use, and more.
[0018]Privileged resource events such as launching a Secure Shell (SSH) session or a Remote Desktop Protocol (RDP) session as an administrator.
[0019]Mobile device management events such as enrolling or un-enrolling a mobile device with an identity manag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com