Authentication method and system
a technology applied in the field of authentication method and system, can solve the problems of method losing value for authentication, inherently vulnerable to counterfeiting of deterministic authentication mechanism,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0257]The detailed preferred embodiments of the invention will now be described with respect to the drawings. Like features of the drawings are indicated with the same reference numerals.
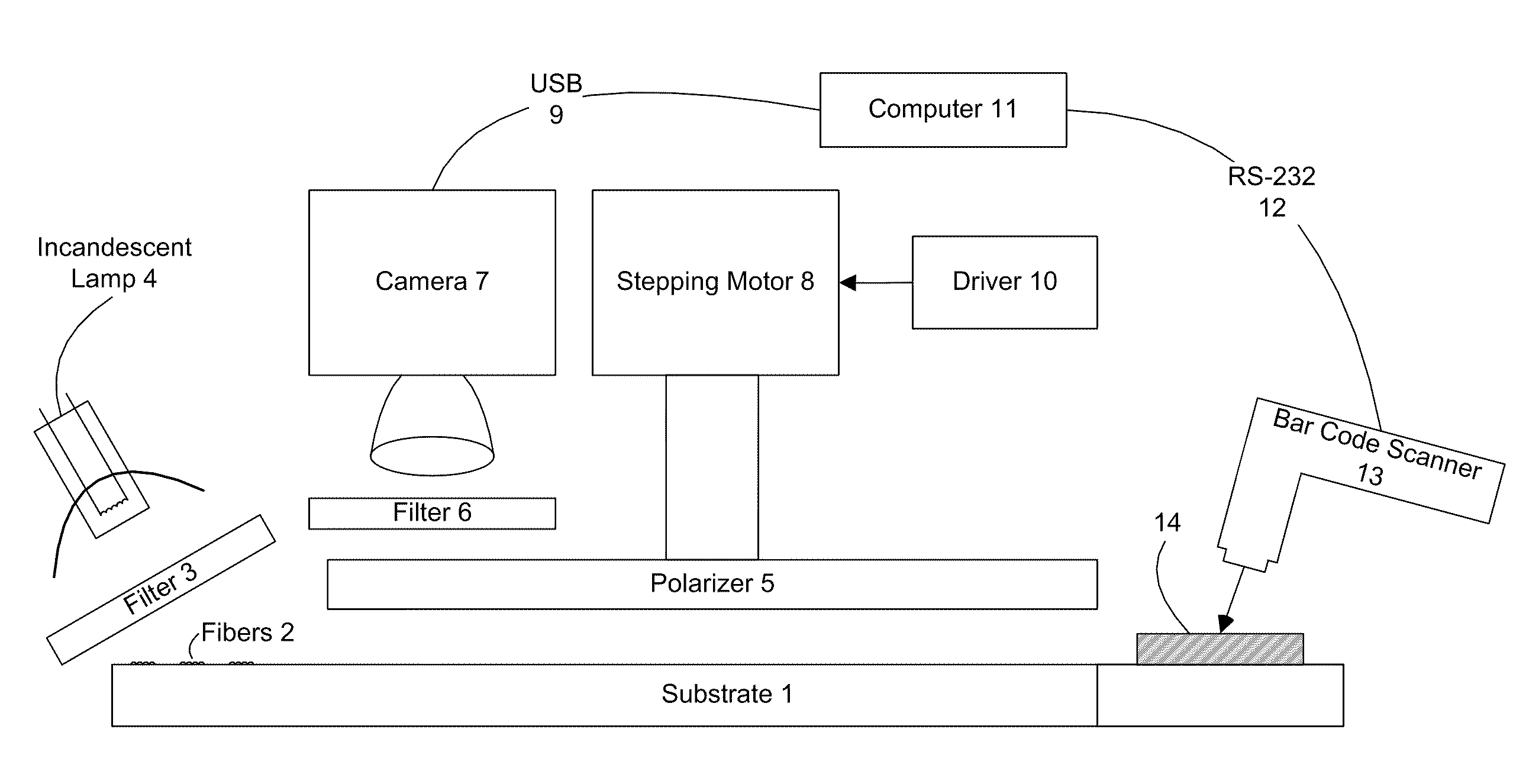
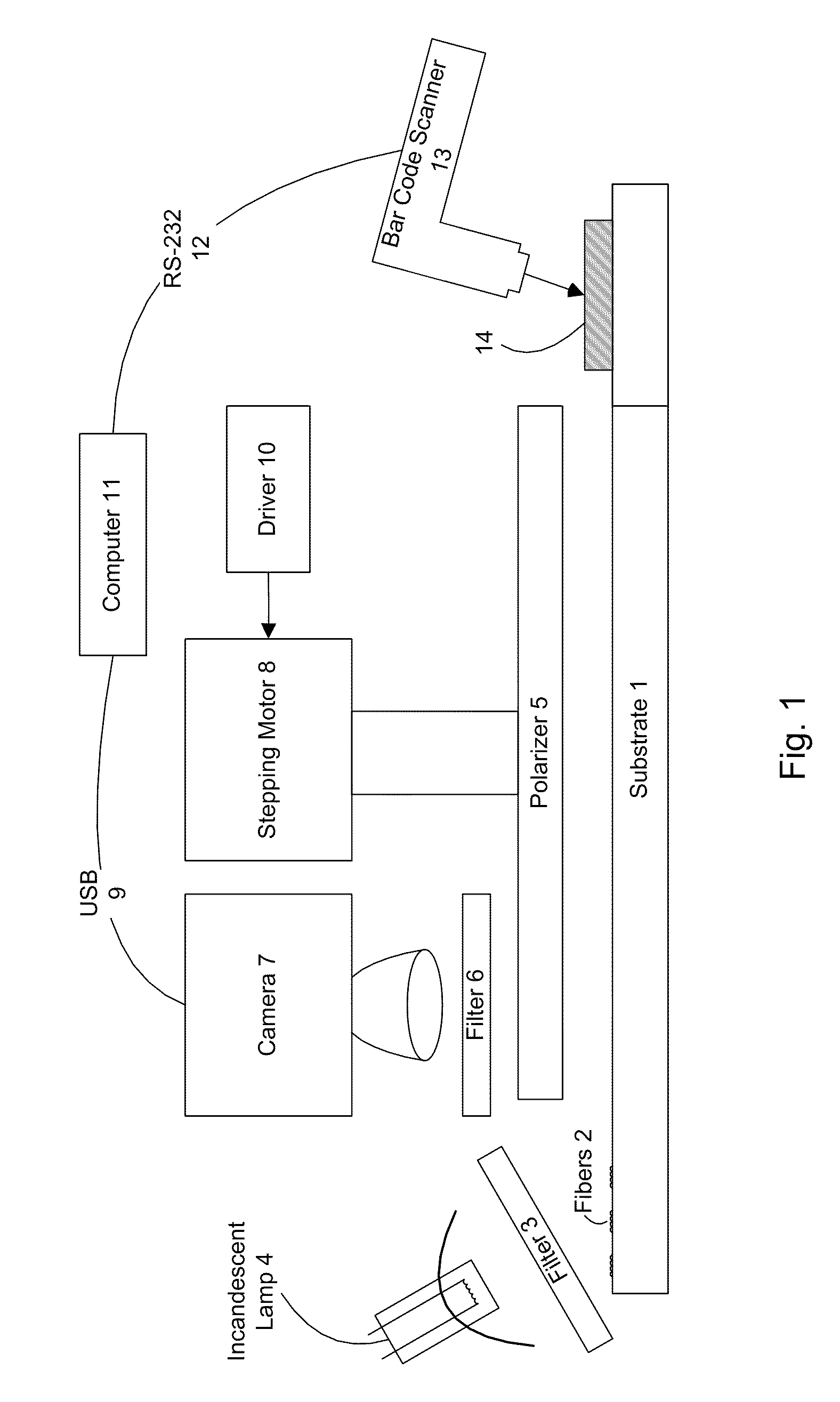
[0258]In FIG. 1, a substrate 1 with dichroic fibers 2 located on it is subject to a filter 3 of an incandescent lamp 4. A polarizer 5 is beneath a filter 6 underneath a camera 7 and this camera 7 via a Universal Serial Bus (USB) 9 is connected to a computer 11 which is in turn connected to a bar code scanner 13 via a RS-232 standard serial port 12. The bar code scanner 13 scans the bar code 14 on the substrate 1 and completes the authentication procedure with the aid of the computer 11.
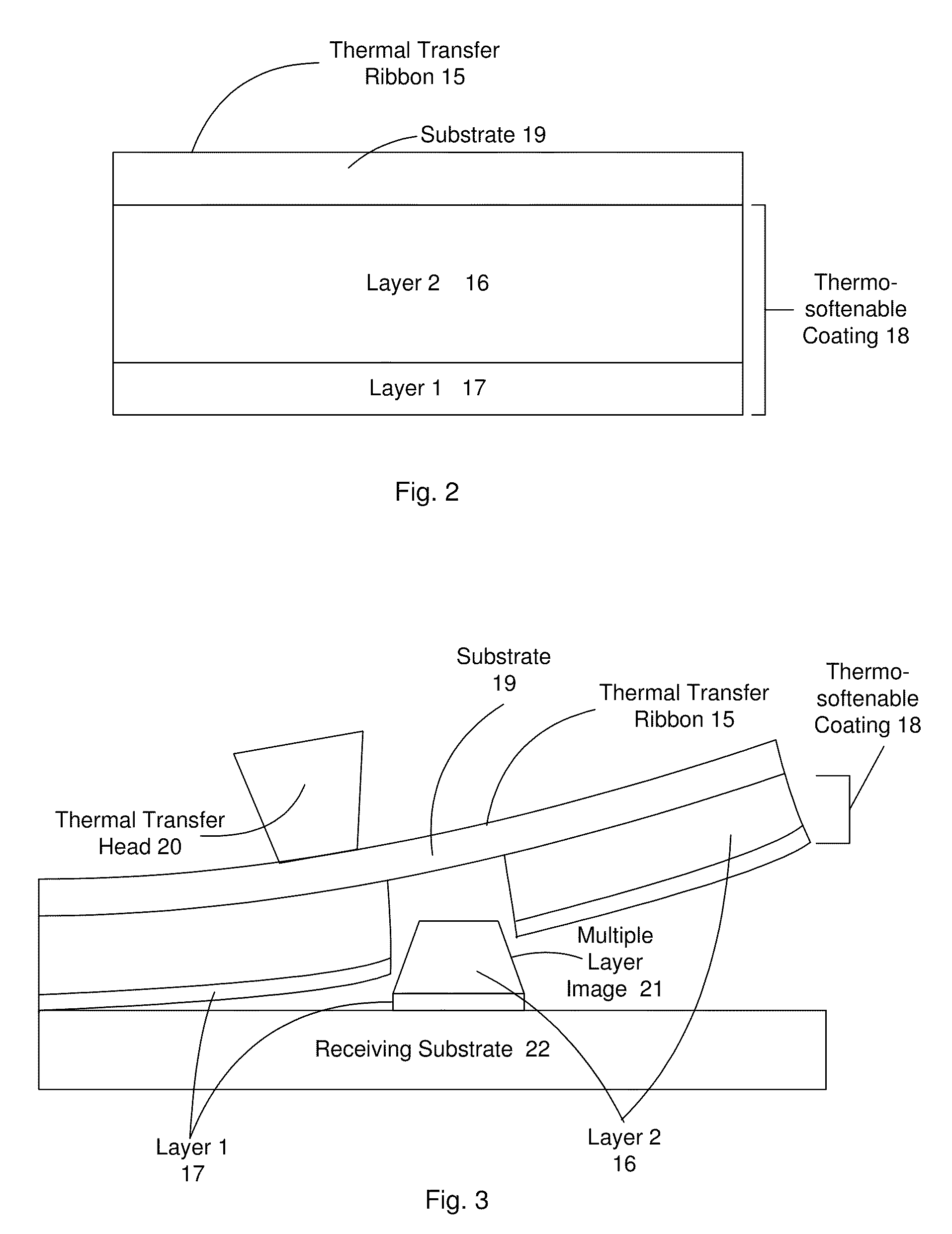
[0259]FIG. 2 shows a thermal transfer ribbon 15 comprising a substrate 19, and positioned on the substrate 19 is a thermosoftenable coating 18 which comprises a layer 16 and a layer 17. Layer 17 comprises a sensible material, e.g. binder compounds. Layer 16 is crystalline, and has a melting temperature above the print...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com