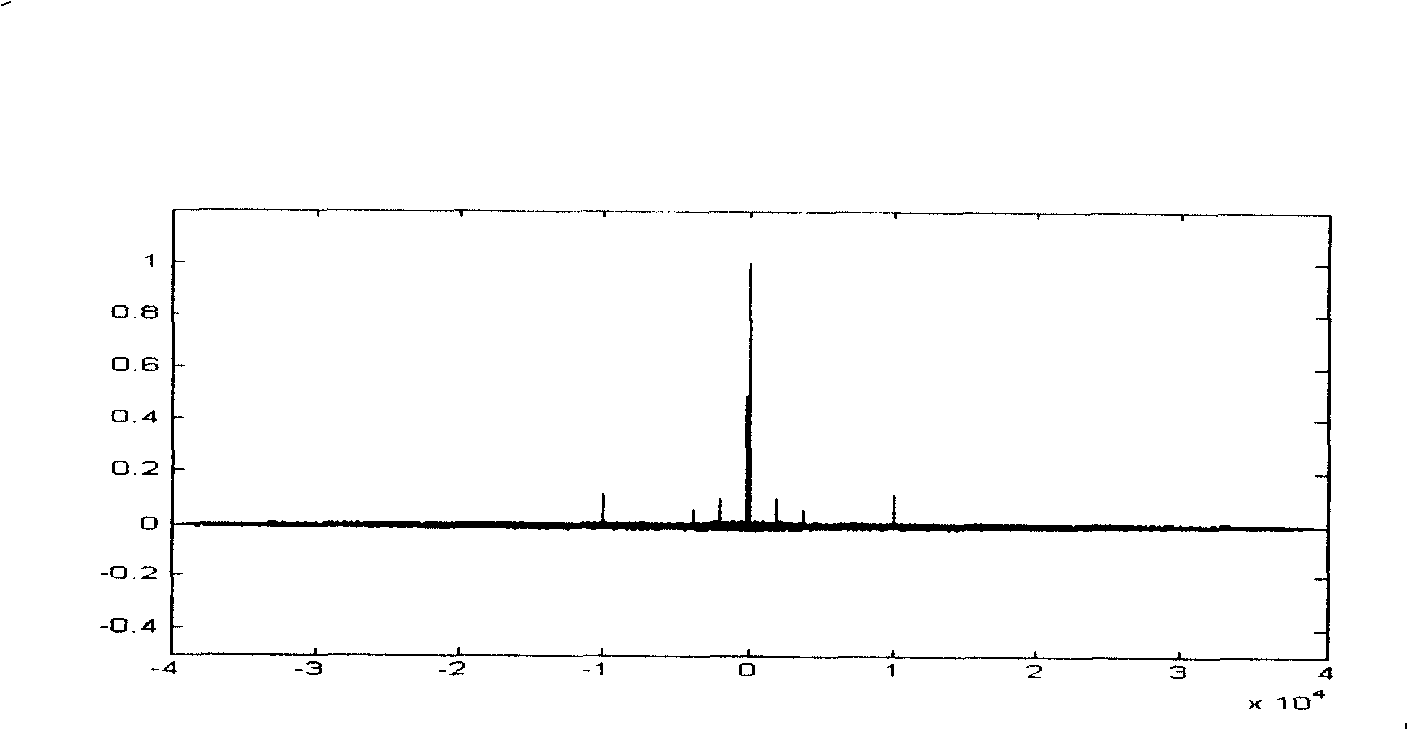
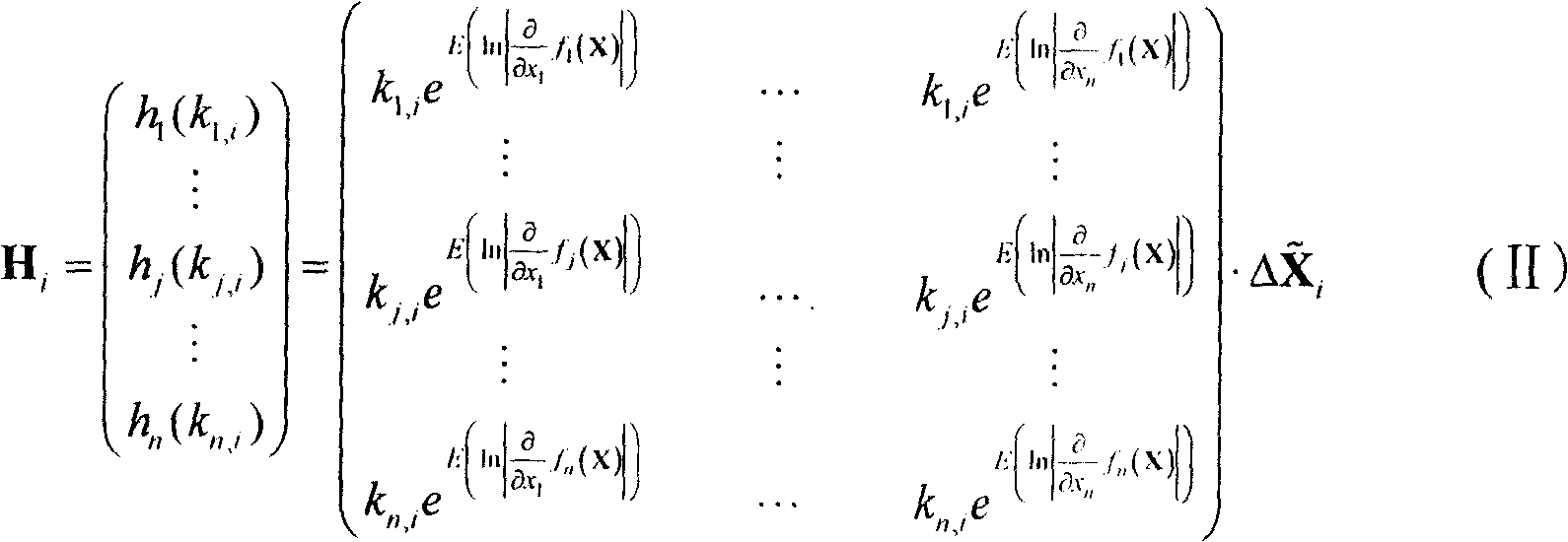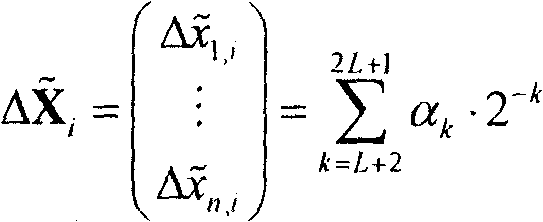Method of chaos cipher based on precision complement
A technology of chaotic cryptography and precision compensation, which is applied in the field of information security, can solve problems such as characteristic degradation, and achieve the effects of extended cycle and good cryptographic properties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0039] In this example, a cryptographic system is designed by using one-dimensional chaotic map, and the operation precision is 16 bits. The set of compensation parameters determined according to the properties and calculation precision of chaotic map f(x) is: U={k[0]=0.5, k [1]=0.65, k[2]=0.7, k[3]=0.75, k[4]=0.8, k[5]=0.85, k[6]=1.0, k[7]=1.1, k[ 8]=1.25, k[9]=1.4, k[10]=1.45, k[11]=1.55, k[12]=1.6, k[13]=1.7, k[14]=1.75, k[15] ]=1.8, k[16]=1.85, k[17]=1.9, k[18]=1.95, k[19]=-0.55, k[20]=-0.6, k[21]=-0.65, k [22]=-0.75, k[23]=-0.8, k[24]=-0.85, k[25]=-0.9, k[26]=-0.95, k[27]=-1.1, k[28 ]=-1.15, k[29]=-1.25, k[30]=-1.4, k[31]=-1.45, k[32]=-1.5, k[33]=-1.55, k[34]= -1.6, k[35]=-1.7, k[36]=-1.75, k[37]=-1.8, k[38]=-1.85, k[39]=-1.9}. In this embodiment, the compensation parameters are selected according to the sequence, therefore, the formula (4) can be specifically written as the following form:
[0040] x ~ ...
example 2
[0051] In this example, a cryptographic system is designed by using one-dimensional chaotic map, and the operation precision is 16 bits. The set of compensation parameters determined according to the properties and calculation precision of chaotic map f(x) is: U={k[0]=0.5, k [1]=0.65, k[2]=0.7, k[3]=0.75, k[4]=0.8, k[5]=0.85, k[6]=1.0, k[7]=1.1, k[ 8]=1.25, k[9]=1.4, k[10]=1.45, k[11]=1.55, k[12]=1.6, k[13]=1.7, k[14]=1.75, k[15] ]=1.8, k[16]=1.85, k[17]=1.9, k[18]=1.95, k[19]=-0.55, k[20]=-0.6, k[21]=-0.65, k [22]=-0.75, k[23]=-0.8, k[24]=-0.85, k[25]=-0.9, k[26]=-0.95, k[27]=-1.1, k[28 ]=-1.15, k[29]=-1.25, k[30]=-1.4, k[31]=-1.45, k[32]=-1.5, k[33]=-1.55, k[34]= -1.6, k[35]=-1.7, k[36]=-1.75, k[37]=-1.8, k[38]=-1.85, k[39]=-1.9}. Randomly select the compensation parameter from the compensation parameter set U, and use it to compensate the i-th iteration of the chaotic map f(x). Therefore, formula (4) can be specifically written as the following form:
[0052] ...
example 3
[0063] In this example a 30-dimensional chaotic map is used
[0064] x 1 , i + 1 x 2 , i + 1 x 3 , i + 1 · · · x ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com