Encrypting read / write method in use for NAS storage system
A technology of storage system and reading and writing method, which is applied in the field of network storage, can solve the problems of reducing the performance of the file system, and achieve the effects of improving security, overcoming inconvenient use, and overcoming low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
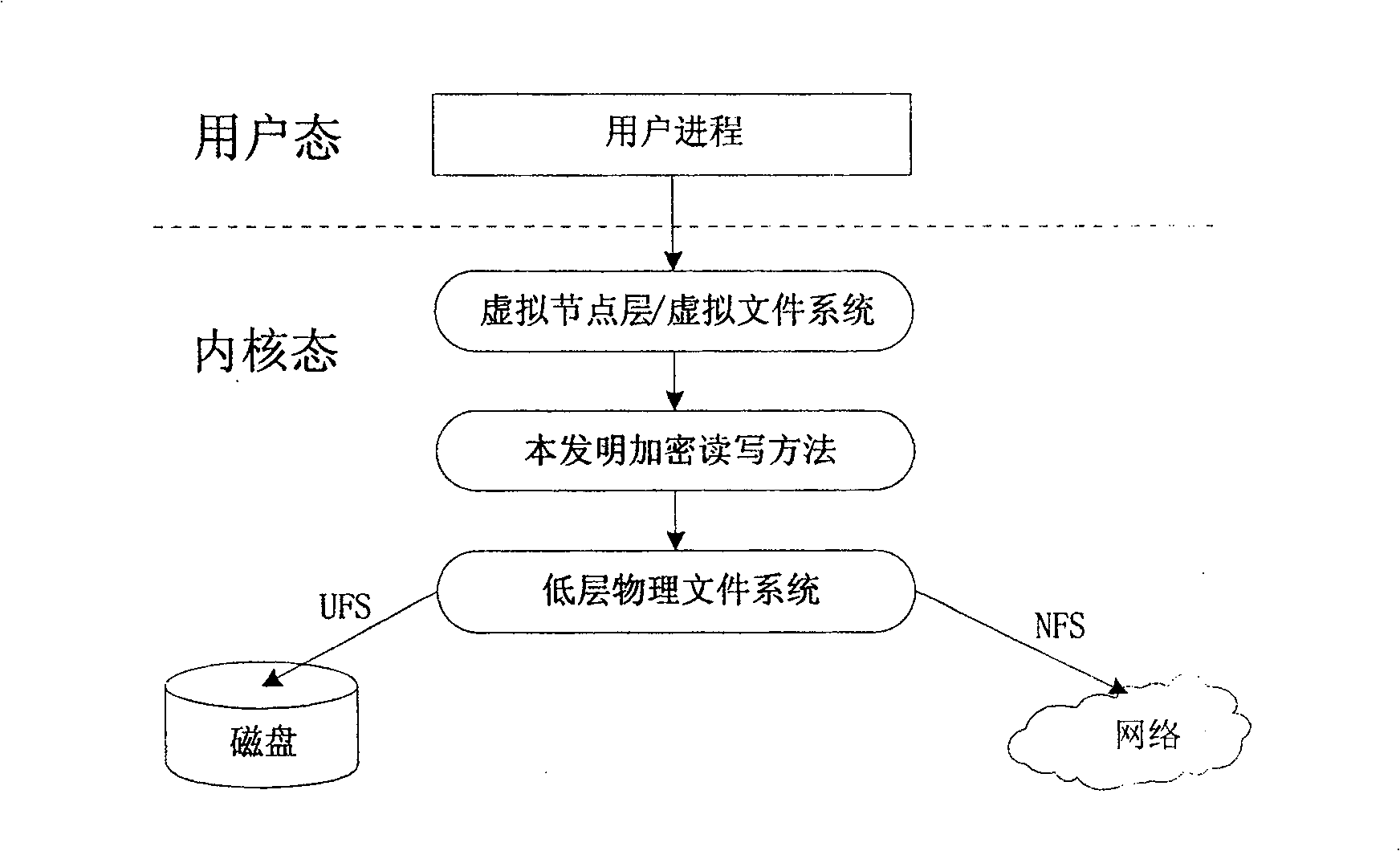
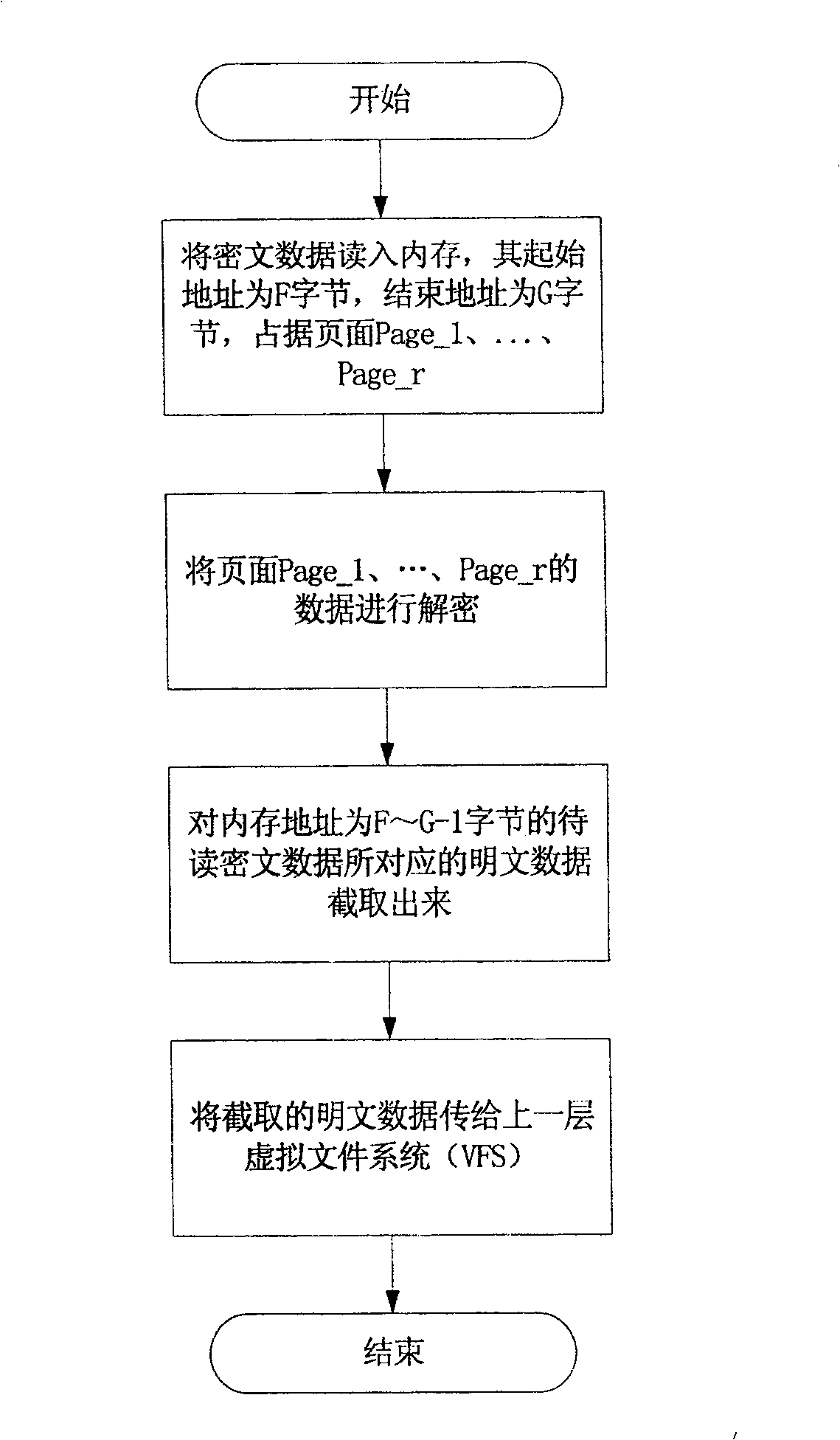
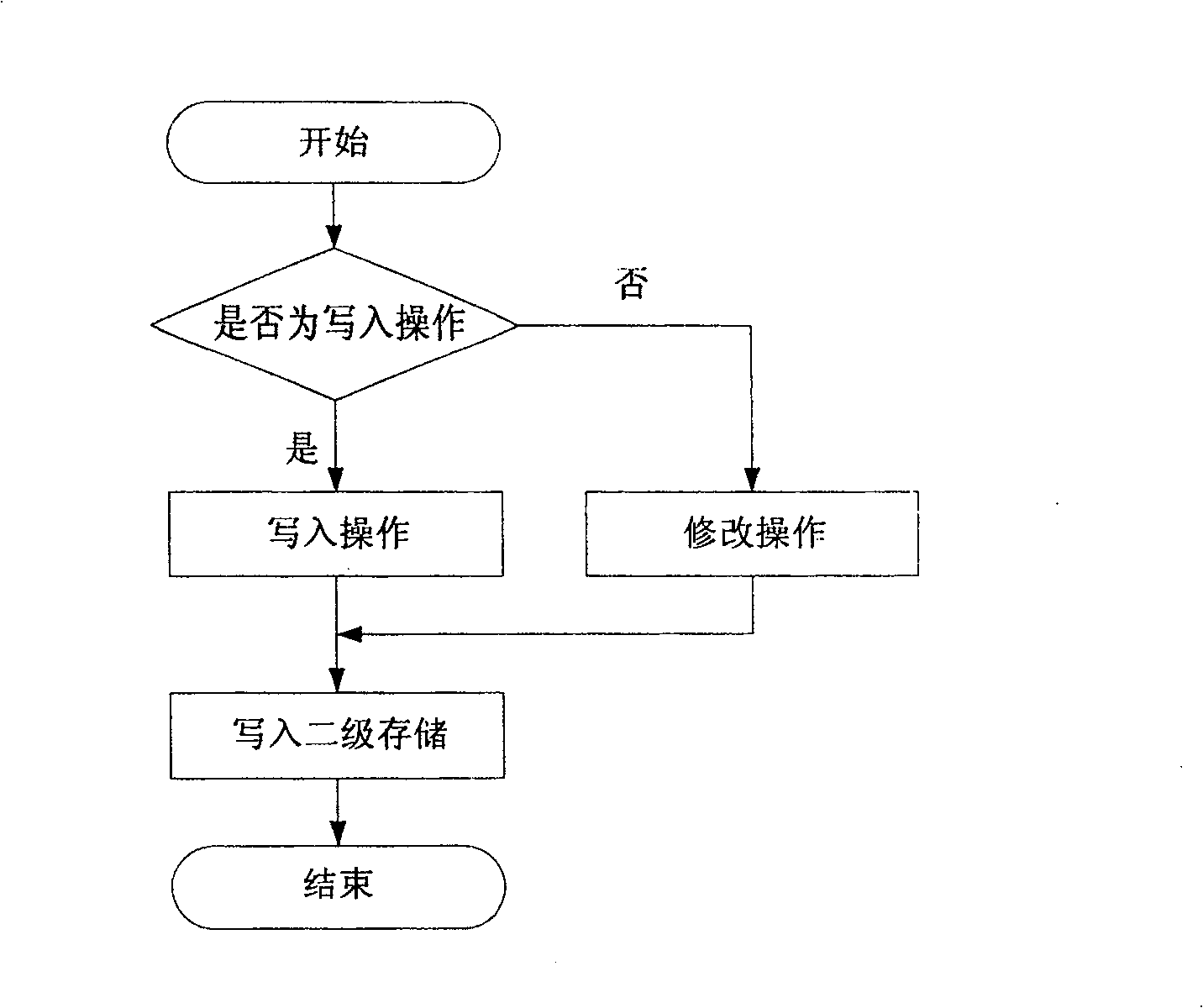
[0040] When accessing the NAS, the data will reach the server through the network, passing through the network file system layer. Read and write data for encryption and decryption. The encryption algorithm adopts Blowfish proposed by Bruce Schneier, which can ensure that the data size before and after encryption is the same. For reference, see http: / / www.schneier.com / blowfish.html. This transparent encryption method not only maintains the user's usage habits, but also overcomes the shortcomings of low performance and efficiency of user-mode encrypted file systems (such as CFS).
[0041] In data encryption, data before encryption is called plaintext data, and data after encryption is called ciphertext data, and this term is used in the application of the present invention.
[0042] Such as figure 1 As shown, the file system often resides in the kernel and communicates directly with the device driver. The virtual file system abstracts the file system operation from the impleme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com