Physical certifying method and device
An authentication method and physical technology, applied in the field of physical authentication, which can solve the security risks of authentication methods, cannot solve the problem of binding legal users to electronic devices, and cannot guarantee other problems, so as to facilitate physical authentication and realize the flexibility of physical authentication. , to achieve the effect of flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
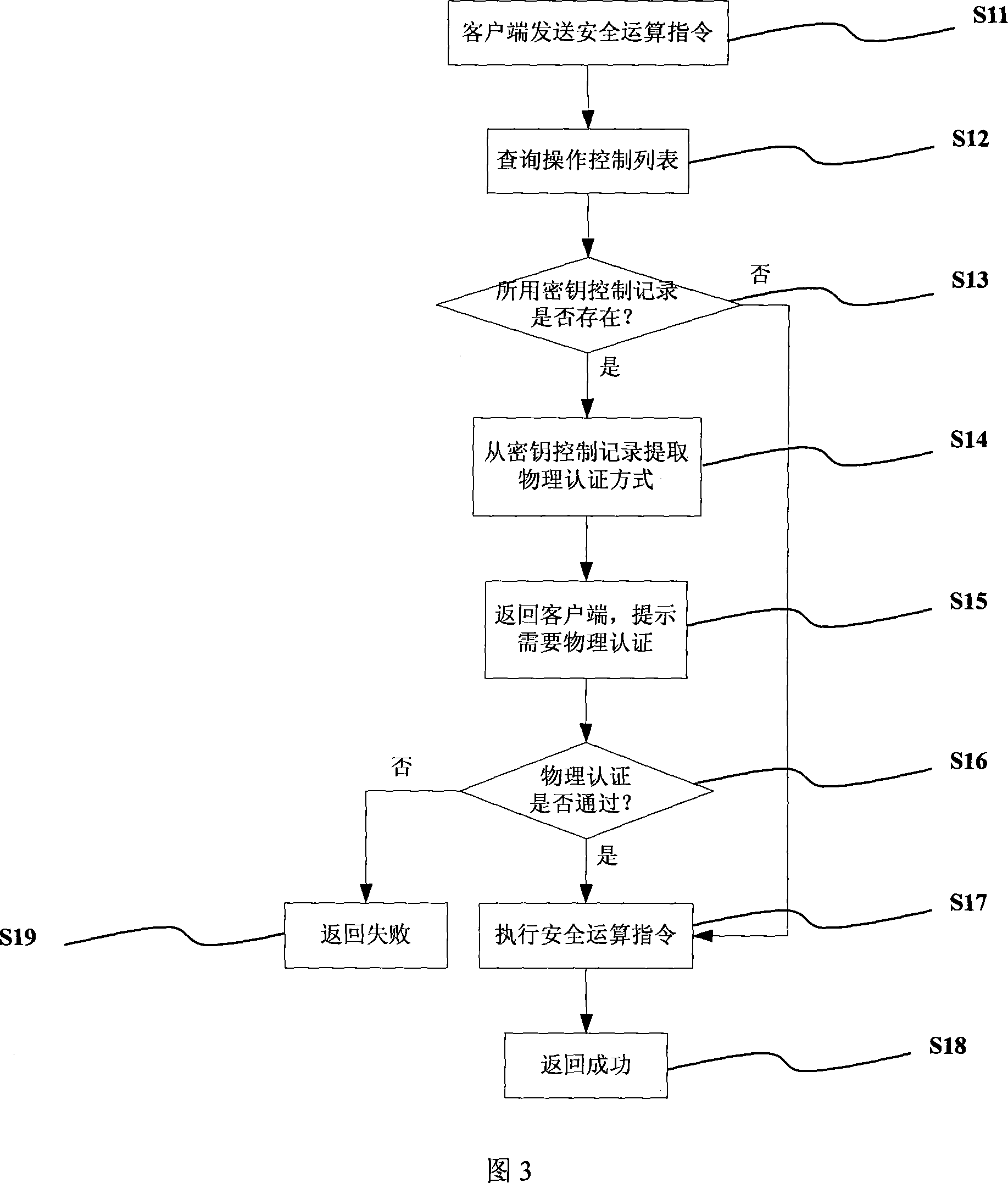
[0104] As shown in Figure 3, it is a schematic flow chart of Embodiment 1. This flow chart demonstrates the process of the user using the present invention to implement security operations. As can be seen from the figure, it mainly includes the following steps:
[0105] S11. The client sends a secure computing command to the electronic device;
[0106]S12. The electronic device searches the operation control list according to the key used by the secure computing instruction;
[0107] S13. The electronic device judges whether there is a corresponding operation control record for the key? If yes, enter step S14, if no, enter step S17;
[0108] S14. The electronic device extracts physical authentication mode information from the operation control record;
[0109] S15. The electronic device returns the physical authentication information to the client, and the client prompts the user to perform corresponding physical authentication;
[0110] S16. The electronic device judges wh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com