Wireless switching network re-authentication method based on wireless LAN secure standard WAPI
A wireless local area network and switching network technology, which is applied in the application field of the wireless local area network security standard WAPI, can solve the problems that the pre-identification method cannot meet the user's fast moving needs, is complicated, and is not conducive to network expansion, and is conducive to large-scale expansion and reduction. Burden, the effect of shortening the delay time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in further detail below in conjunction with the accompanying drawings.
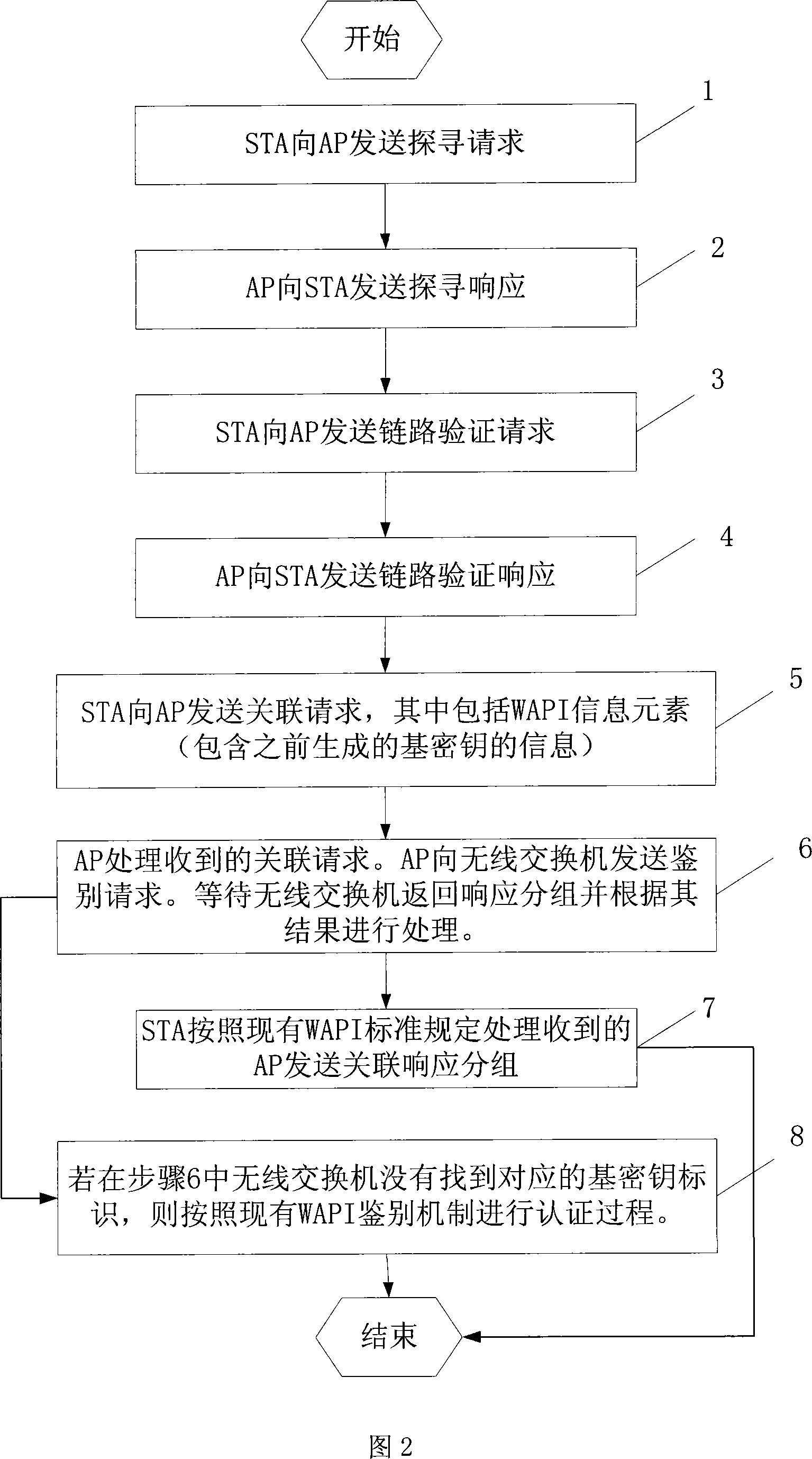
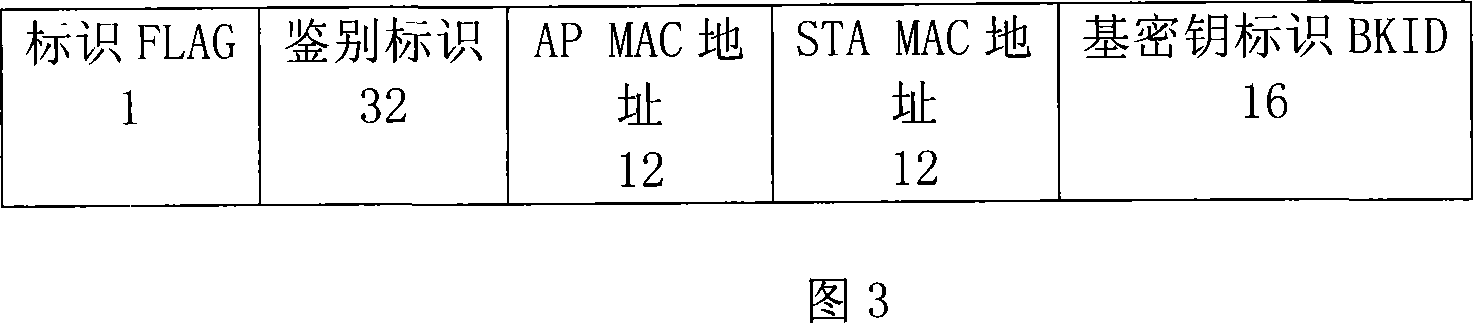
[0039] In this application method, the wireless switch is used to cache the previous key information. When the STA connects to the new AP, the previous key information is used to complete the fast connection, so as to adapt to the mobile network supported by the real-time streaming media application. performance requirements. After a period of time after the handover is completed, the existing WAPI standard key update process can be started, and a new base key and session key are negotiated between the STA and the AP.
[0040] The WAPI application mechanism process based on the pre-authentication cache mechanism is as follows:
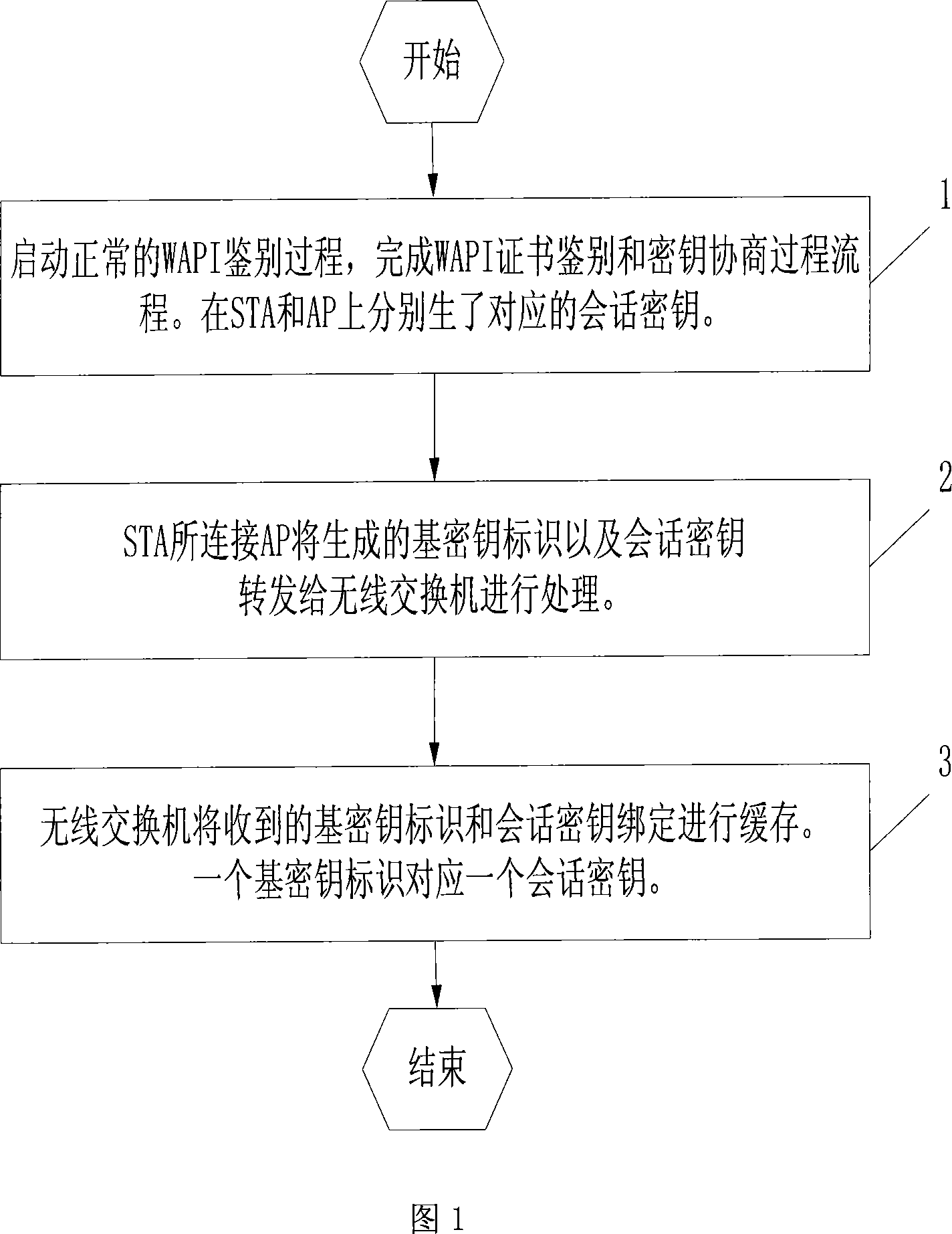
[0041] In the first phase, the STA connects to the wireless switching network for the first time.
[0042] FIG. 1 is a flow chart of an authentication process for a STA connecting to a wireless switching network for the first time. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com