Security management method of dual-encryption channel cooperation in network management system
A network management system and encrypted channel technology, applied in the field of security management of double encrypted channel cooperation, can solve the problems of failure to exert transmission efficiency and low efficiency, and achieve good practical application significance and value, effective system resources, and effective utilization. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
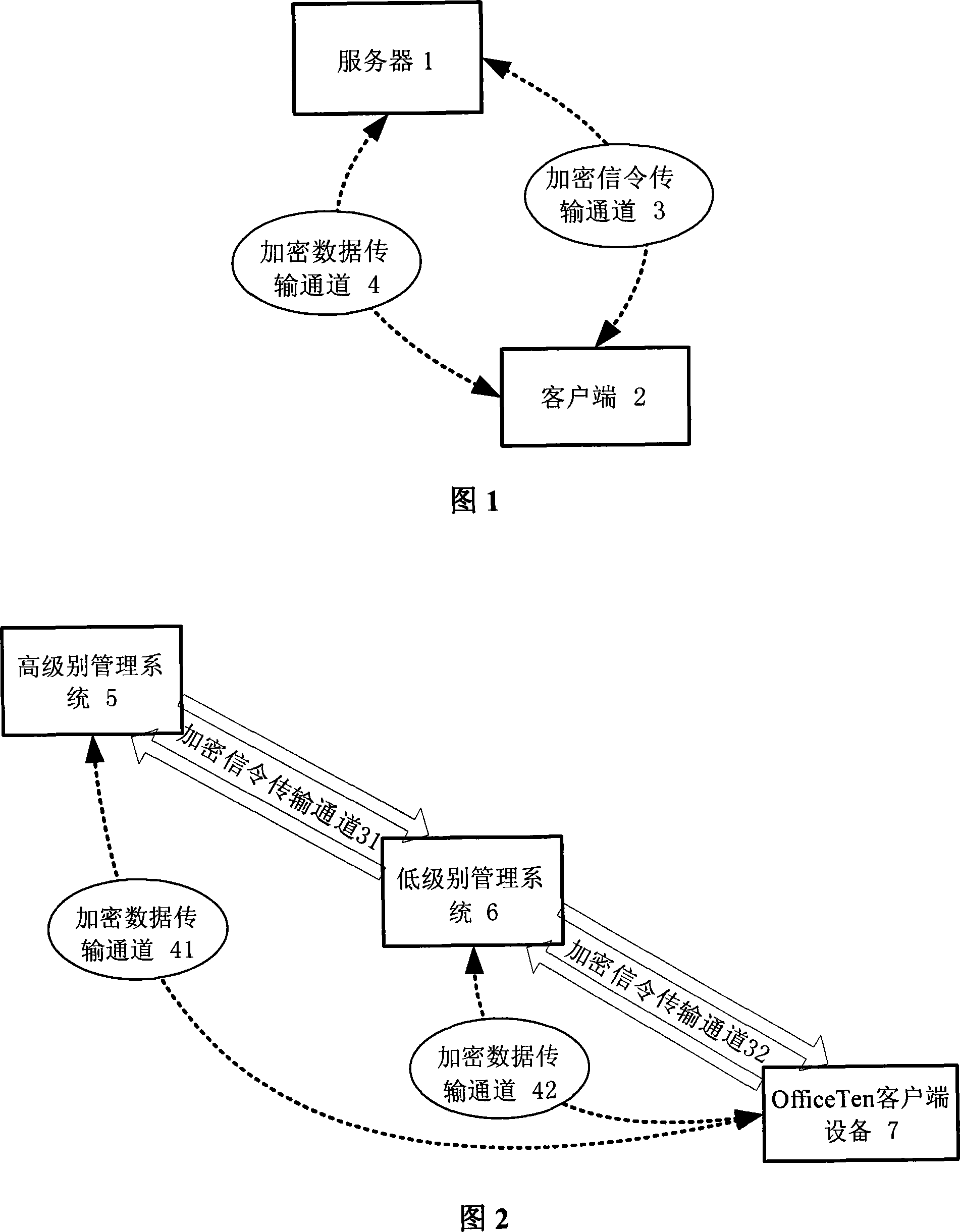
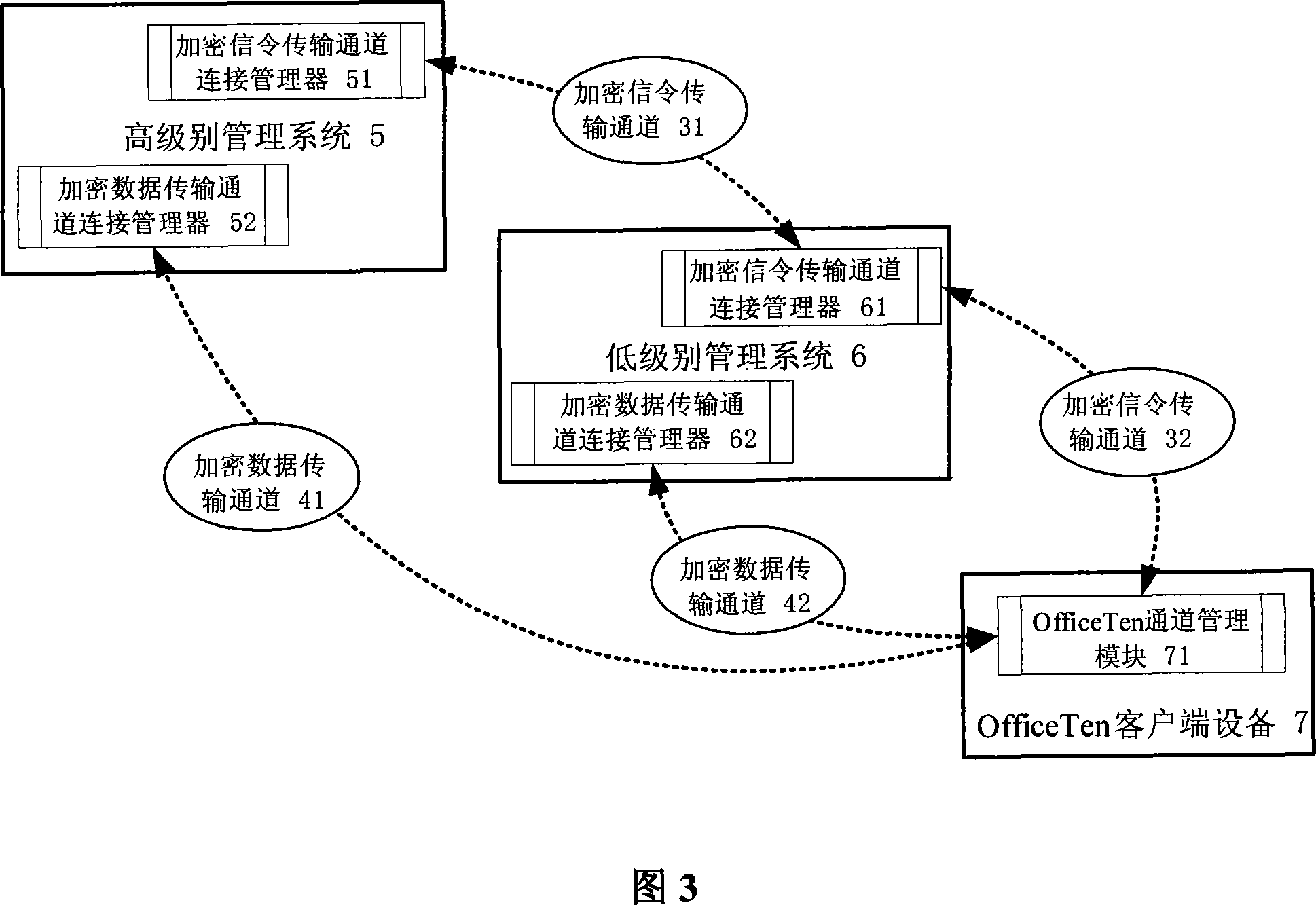
[0024] A security management method for double encryption channel cooperation in a network management system, which uses encryption channel technology to divide transmission data into two types, establishes two different types of encryption channels according to different data types, and adopts different encryption methods and Transmission mode, at the same time, the two channels cooperate with each other to complete the entire data transmission requirements. The data is divided into two types: control signaling data and file data. An encrypted signaling transmission channel is established to transmit control signaling data, and an encrypted data transmission channel is established to transmit file data. The specific execution process of the two channels is in charge of the control module. , so that the two encrypted channels cooperate with each other to transmit data securely.
[0025] The architecture of the dual encryption channel of the network management system is shown i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com