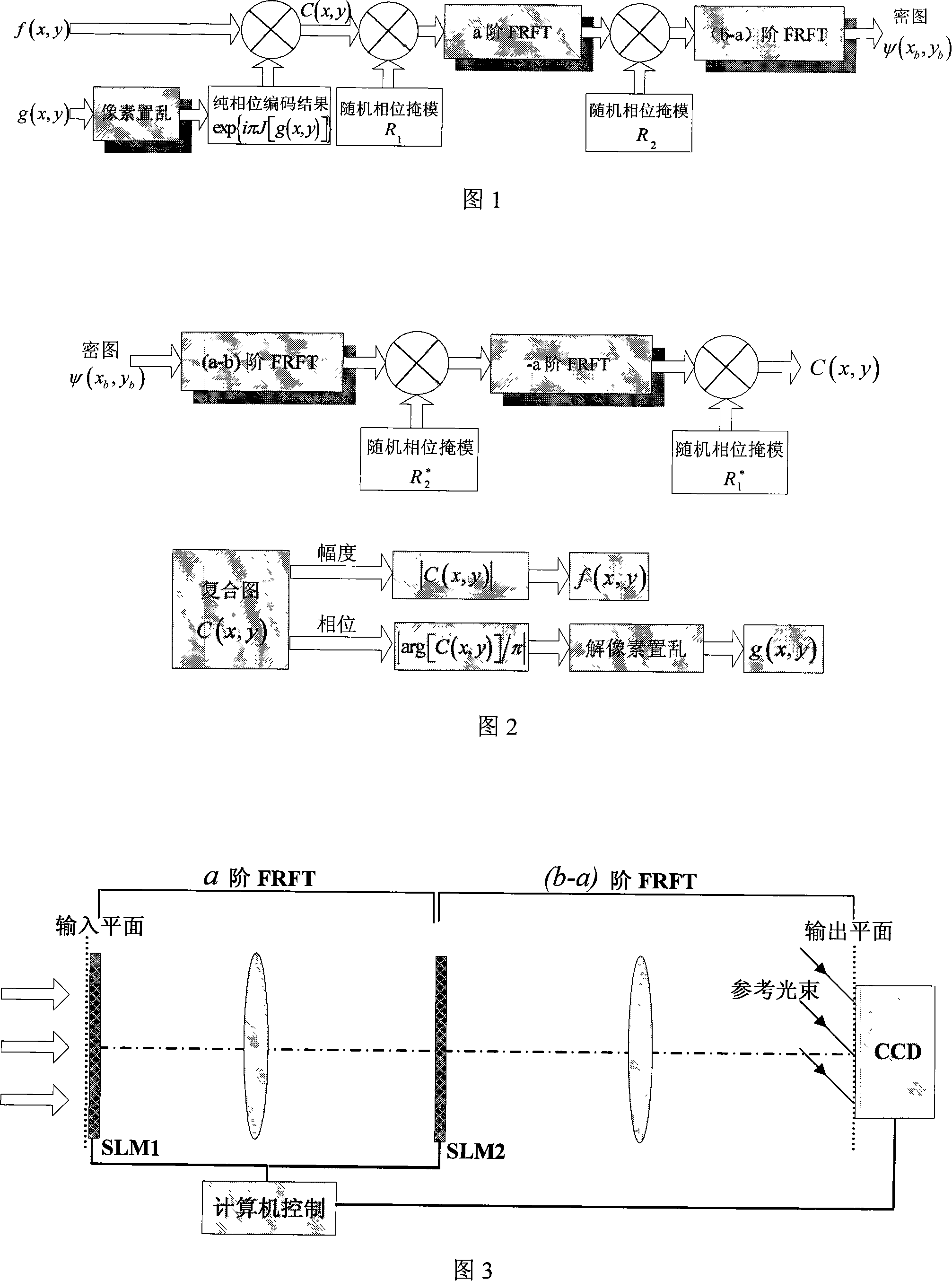
A dual graph encryption method based on fraction rank Fourier conversion
A technology of fractional Fourier and encryption method, which is applied in the field of information security, and can solve the problems of undiscussed secret map performance, difficult optical realization, mutual interference of decrypted maps, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0092] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
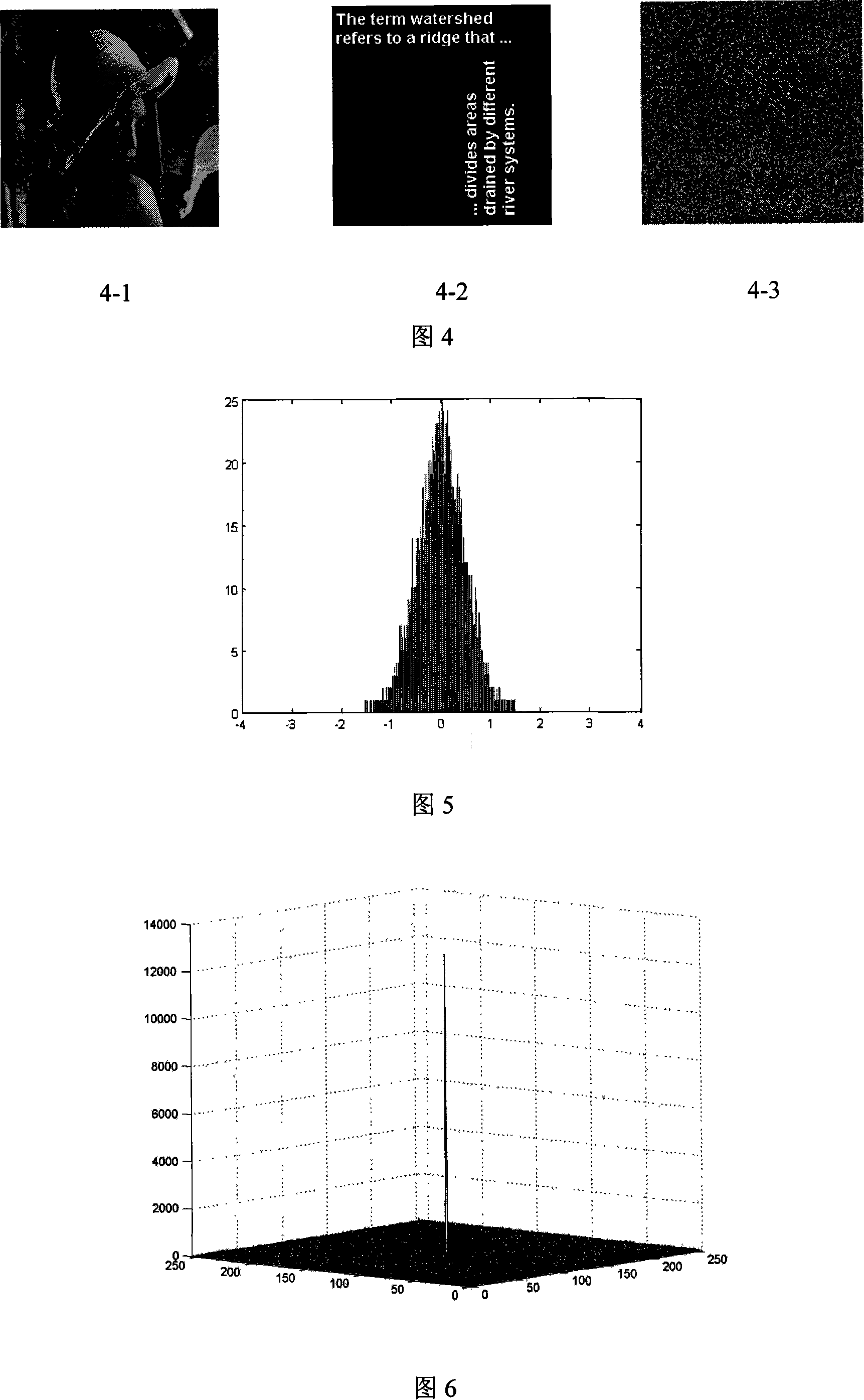
[0093] Select a standard test grayscale image "Lena" and a binary image "text" with a size of 256×256 as the original images f(x, y) and g(x, y) to be encrypted in this embodiment, as shown in Figure 4 -1 and Figure 4-2. The simulation is carried out using Matlab 2006a.
[0094] First normalize their pixel values. After the binary image is scrambled, phase-only encoding is performed, and then a composite image is generated with the gray-scale image for bi-phase encoding. The transformation order of the two-dimensional fractional Fourier transform is a x =a y = 0.82 and b x =b y = 0.45. The magnitude of the result of double-image encryption using the present invention is shown in Figure 4-3.
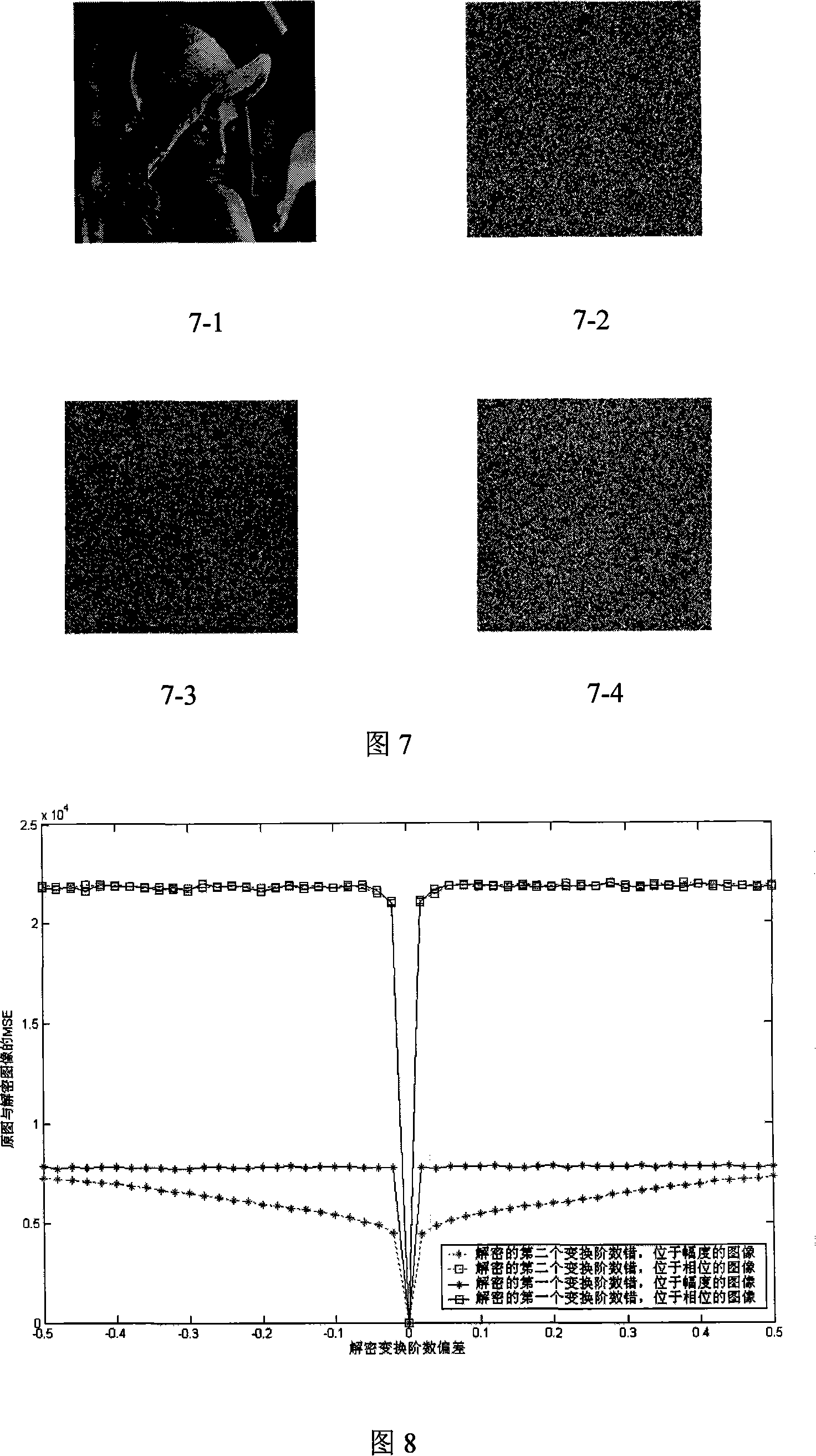
[0095] Embodiment is explained and performance analysis below in conjunction with accompanying drawing:
[0096] The histogram of the real part of the den...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com