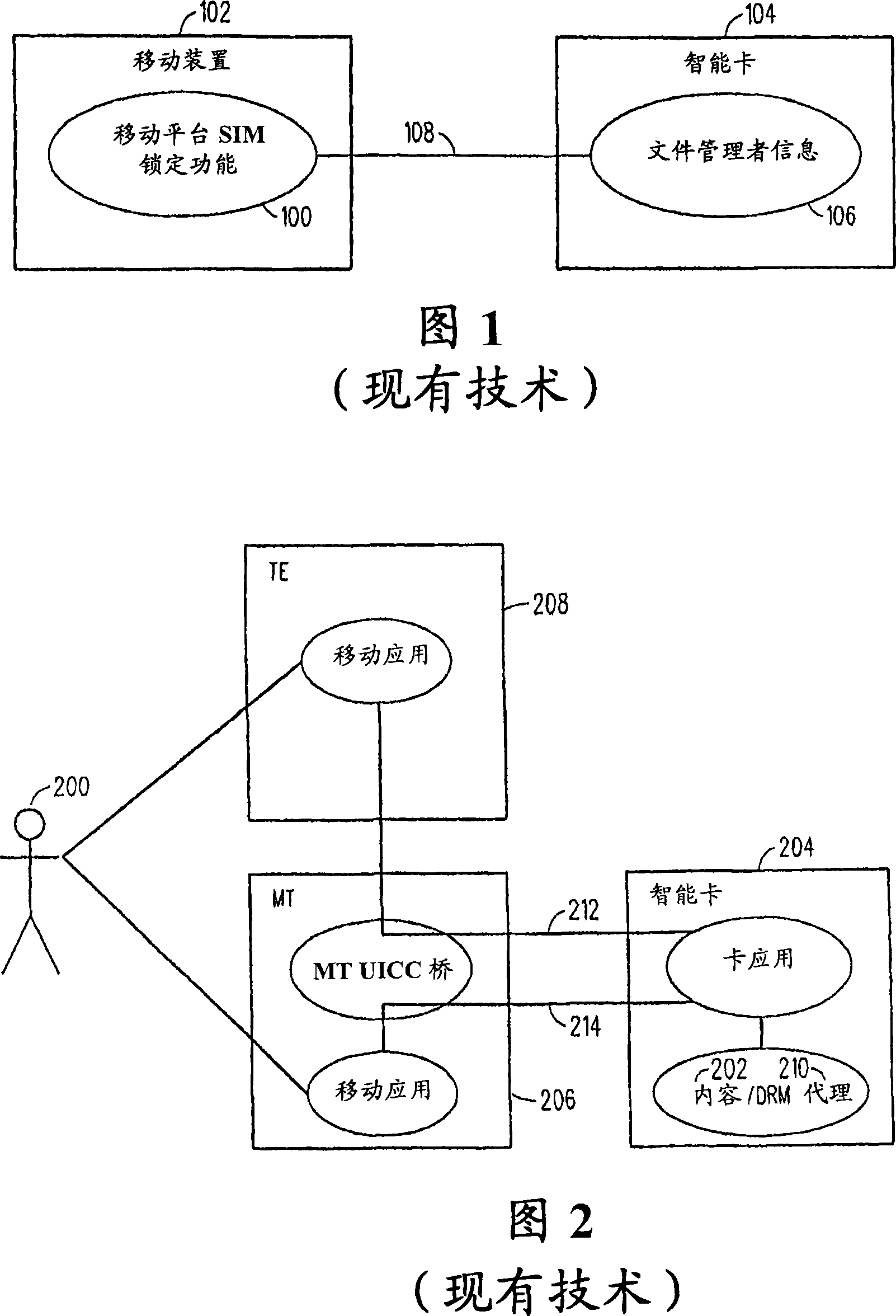
Network assisted terminal to SIMM/UICC key establishment
A shared key, mobile terminal technology, applied in the field of network-assisted terminal to SIMM/UICC key establishment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
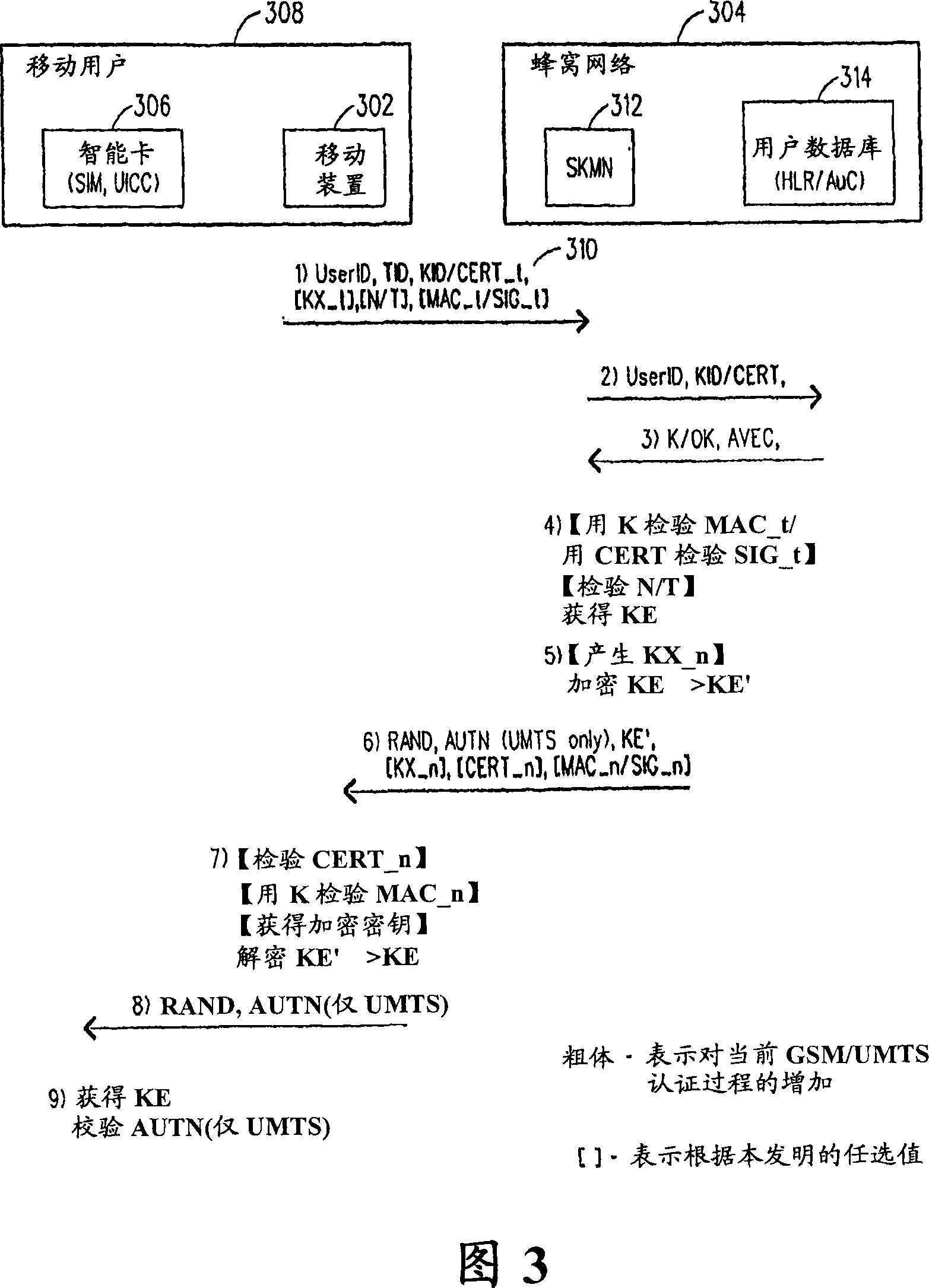
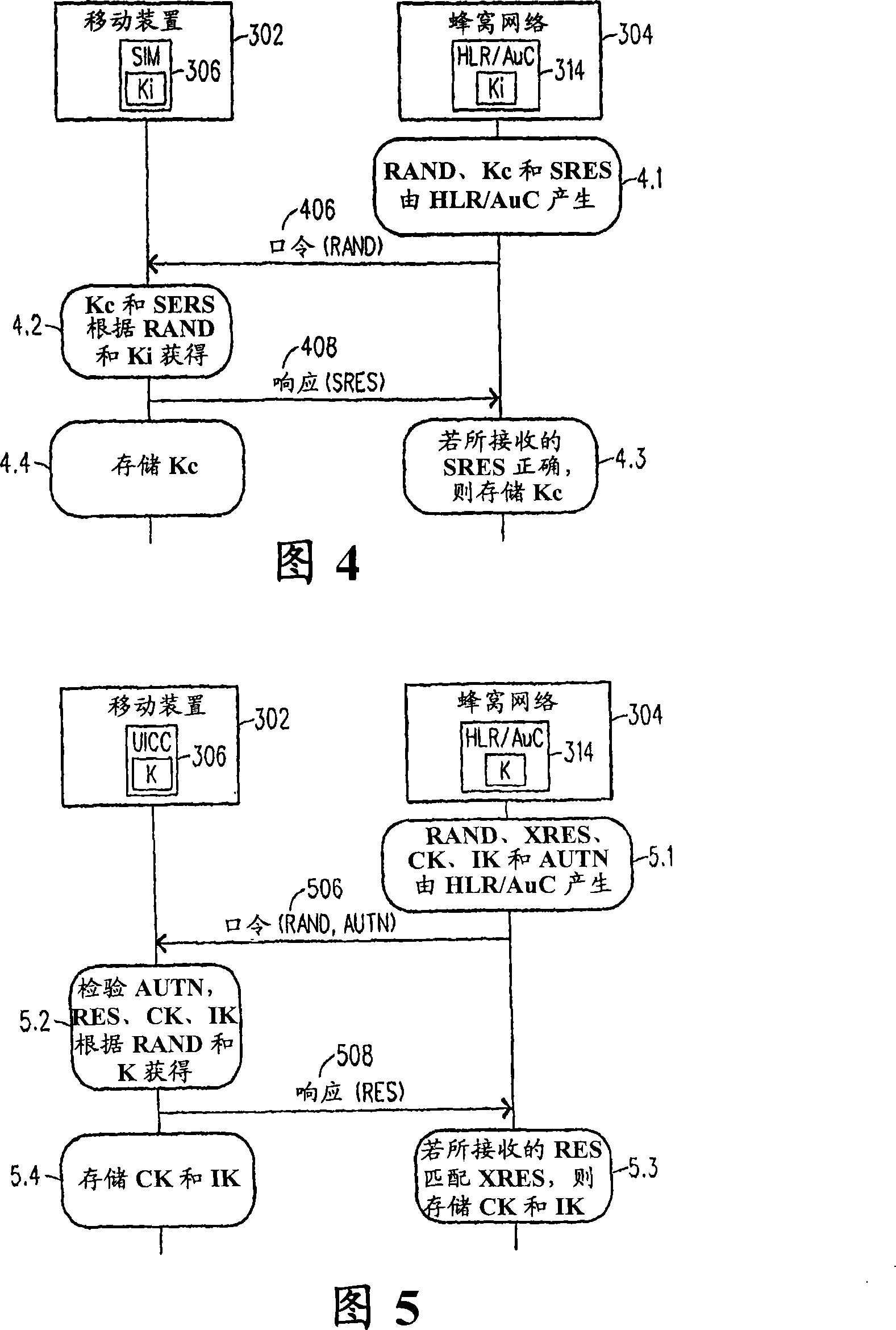
[0042] The present invention relates to a method for establishing a shared key between a mobile device and a smart card (containing a SIM or UICC application). In particular, the present invention relates to a method that utilizes a mobile network operator (and subscriber database) to perform the key exchange necessary to establish a shared key between a mobile device and a smart card (SIM or UICC) of. To help achieve this, the method employs a key generation function associated with the existing GSM / UMTS authentication standard. An embodiment of the present invention will be described step by step with reference to FIG. 3 .
[0043] Referring to FIG. 3, a signal flow diagram therein illustrates step by step the key exchange method according to the first embodiment of the present invention. In this embodiment, it is assumed that the mobile device 302 has access and connected to the cellular network 304 . This means that the mobile device 302 has been authenticated by the ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com